Could some one please tell me if my analysis about the FTP pasv and port modes is right.
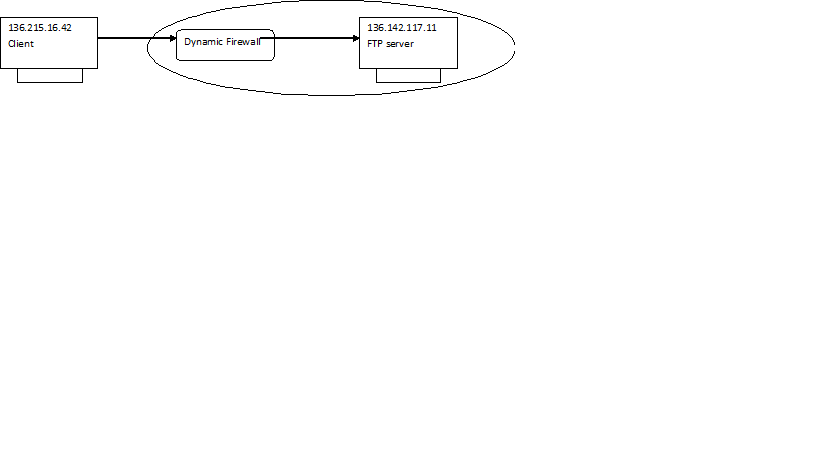
Let there be a dynamic firewall that protects the network 136.142.117.0/24. It blocks most incoming TCP connections but allows incoming FTP requests to port number 21 and destination IP address 136.142.117.11.
Identify the interfaces and show the rulesets that are created for those interfaces in the firewall when the FTP session is ongoing. Assume that the client uses the PORT command.
The client initiates the creation of a control channel between itself at port ex; 5000 and the server at port 21(typical FTP port) ip 136.142.117.1. It sends a SYN packet. Since the firewall allows connections to the FTP server at port 21, it allows the SYN packet to enter the network with destination ip 136.142.117.11.
The server responds back to the client with a SYNACK to the port 5000. The client sends an ACK packet.
The authentication takes place by providing the username and password. If successful, the client creates a random port (256 * 3) + 10 = 778. Then the client issues a port command port(130,215,16,42,3,10) to server. The server acknowledges the information and sends a confirmation status 200 ok message.
Meanwhile the dynamic firewall creates a ruleset stating that, allow incoming packets to destination 136.142.117.11:20 from source ip 130.215.16.42:778.
The data connection is established between port 20 of the server and the port 778 on the client.
The client sends the file name that it requires through the control channel and the server responds if it can provide that file with the help of three digit status code which comes along with a message. The file transfer starts off is the status code is fine.
Once the entire file is transferred, a 226 status message is sent back to the client, the dynamic firewalls tears down the rule set.
What problems do you see (because of the firewall) if PORT is used? Do you see any if PASV is used?
Since the server is the one that is protected by the firewall, it does not accept any incoming TCP connections except for the FTP request at port 21, but it can connect to ports outside the network. The information provided by the port command ie; ip address of the client, port number at which it is ready to listen helps the server to create the connection with the client. But if the client is a malicious one, the client in the process of receiving data, can send data to the server after the port establishment and corrupt the server. The server has no choice but to accept the data leading to server hacks
The pasv mode cannot be used since the dynamic filter will drop the packet which contains the pasv information considering it as an incoming TCP connection. Thereby, there is no harm to the server as the data connection would never get established.