Researchers at security company AppRiver have issued a warning regarding a variant of the Fareit malware family which is using fake Amazon purchase confirmation emails to inject itself and steal any type of crypto currency that can be found on the target machine.
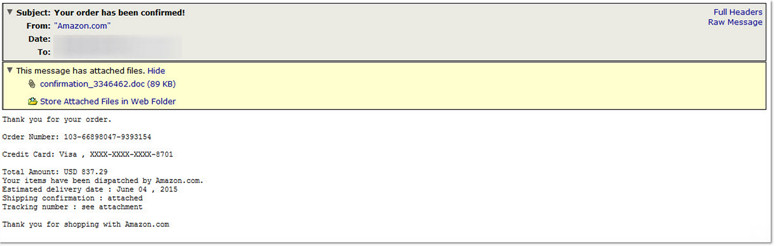
Troy Gill, manager of security research at AppRiver, details how his team have been monitoring, and blocking, what he describes as a stream of malicious emails during the last week. All posing as legitimate Amazon purchase confirmations, all stating that 'your order has been confirmed’ and all directing the reader to the attached, and infected, .doc file for the shipping and tracking details. If the recipient has macro's enabled in Microsoft Office, specifically Microsoft Word, then their machine will become infected upon opening that document. Although it has never really gone away entirely, the Word Macro threat has seen something of a resurgence in recent months and this is just the latest in a long line of examples.
"This family of malware is often distributed via Word documents with malicious macros embedded and has been known to drop multiple malware variants on the target machine" Troy Gill explains, continuing "in this particular case the malware quickly goes to work attempting to steal the Outlook password along with website passwords from various browsers such as Firefox, IE, Chrome and Opera. It then attempts to harvest account credentials for a lengthy list of FTP and multiple file storage programs."
It also starts looking for, and stealing, any crypto currency it finds on the target machine. A behavior that Gill says is becoming increasingly common in the threats they are seeing. "The anonymous nature and lack of regulation in the Crypto Currency market make it more akin to stealing actual cash than to committing wire fraud by raiding someone’s online bank accounts" he observes. Not that the perpetrators seemed to worried about that here, seeing as the last observed behavior of the malware was to drop a copy of Zeus onto the machine just in case any bank related data could be captured...