Security researchers at ESET have revealed that a prolonged and highly targeted data stealing attack aimed at Pakistan, using fake PDF documents, appears to have originated in India.
Using a code signing certificate (issued to what looks like a legitimate company 'Technical and Commercial Consulting Pvt. Ltd') to sign malicious binaries the chances of them being able to distribute the payload was greatly improved. The company concerned, ESET says, was based in New Delhi and the certificate itself was issued in 2011. Documents, mainly PDFs, attached to emails were infected with data stealing malware and signed off with the aforementioned certificate to add authenticity.
ESET malware researcher Jean-Ian Boutin reveals that during the investigation there were several leads that indicated the threat originates from India. "First, the code signing certificate was issued to an Indian company. In addition, all the signing timestamps are between 5:06 and 13:45 UTC, which is consistent with 8-hour work shifts falling between 10:36 and 19:15 in Indian Standard Time" he says, continuing, "we have identified several different documents that followed different themes likely to be enticing to the recipients. One of these is the Indian armed forces". Although Boutin admits that there is no precise information at this point as to which individuals or organisations were specifically targeted by the files. "Based on our investigations" he continues "it is our assumption that people and institutions in Pakistan were targeted".
One of the fake PDF files was delivered through a self-extracting archive called “pakistandefencetoindiantopmiltrysecreat.exe”, and ESET telemetry data shows that Pakistan is heavily affected by this campaign with 79% of detections being in that country. The first infection vector was utilising a widely used and abused vulnerability known as CVE-2012-0158. This vulnerability can be exploited by specially crafted Microsoft Office documents and allows arbitrary code execution. The documents were delivered by email, and the malicious code was executed as soon as the document was opened – without the attacked computer user even knowing. The other infection vector was via Windows executable files appearing to be Word or PDF documents – again distributed via email. In both cases, to evade suspicion by the victim, fake documents are shown to the user on execution.
"The malware was stealing sensitive data from infected PCs and sending them to the attackers’ servers" Boutin adds "It was using various types of data-stealing techniques, among them a key-logger, taking screenshots and uploading documents to attackers’ computer. Interestingly, the information stolen from an infected computer was uploaded to the attacker’s server unencrypted."
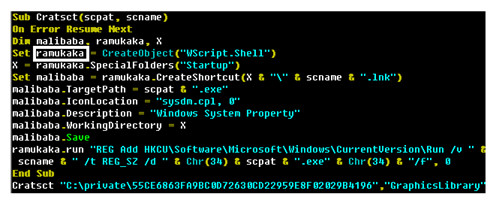
As you can see from the above screenshot, several strings in the binaries analysed by ESET are related to Indian culture, in particular a variable called ramukaka was used. Boutin explains that "Ramu Kaka is a typical Bollywood-style servant in a house. Considering that this variable is responsible for achieving persistence on the system, this definition is a good fit".
However, the most compelling argument to suggest that the attacks originate in India is to be found within the ESET research telemetry data. According to Boutin lots of malware variants tied to the attack appeared in the same location during a small time-frame. Each of these were very similar to each other, which strongly suggests an attempt to evade malware detection. "These files all appeared in the same region of India" Boutin concludes...
