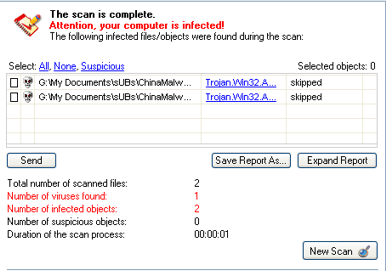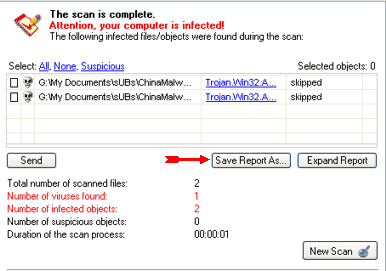
Hi,
Would appreciate some help ... Every time I try to access an anti-virus website (using Internet Explorer), I get the "The page cannot be displayed" screen. (Other sites are fine.) Suspect virus.
HijackThis log below. Thanks.
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 00:52:06, on 25/01/2010
Platform: Windows XP SP1 (WinNT 5.01.2600)
MSIE: Internet Explorer v6.00 SP1 (6.00.2800.1106)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\System32\wltrysvc.exe
C:\WINDOWS\System32\bcmwltry.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\System32\00THotkey.exe
C:\WINDOWS\System32\TPWRTRAY.EXE
C:\Program Files\TOSHIBA\TOSHIBA Controls\TFncKy.exe
C:\WINDOWS\system32\dla\tfswctrl.exe
C:\Program Files\Apoint2K\Apoint.exe
C:\Program Files\TOSHIBA\Wireless Hotkey\TosHKCW.exe
C:\WINDOWS\system32\ntvdm.exe
C:\Program Files\Apoint2K\Apntex.exe
C:\Program Files\3 Mobile Broadband\3Connect\AutoUpdateSrv.exe
C:\Program Files\3 Mobile Broadband\3Connect\WilogApp.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\WINDOWS\System32\taskmgr.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
R1 - HKCU\Software\Microsoft\Internet Explorer,SearchURL = http://www.ewebsearch.net/sp.htm
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,HomeOldSP = http://www.ewebsearch.net/
O2 - BHO: AcroIEHlprObj Class - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Adobe\Acrobat 7.0\ActiveX\AcroIEHelper.dll
O2 - BHO: SSVHelper Class - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files\Java\jre1.5.0_09\bin\ssv.dll
O2 - BHO: Google Toolbar Helper - {AA58ED58-01DD-4d91-8333-CF10577473F7} - c:\program files\google\googletoolbar1.dll
O3 - Toolbar: &Google - {2318C2B1-4965-11d4-9B18-009027A5CD4F} - c:\program files\google\googletoolbar1.dll
O3 - Toolbar: &Radio - {8E718888-423F-11D2-876E-00A0C9082467} - C:\WINDOWS\system32\msdxm.ocx
O4 - HKLM\..\Run: [00THotkey] C:\WINDOWS\System32\00THotkey.exe
O4 - HKLM\..\Run: [Tpwrtray] TPWRTRAY.EXE
O4 - HKLM\..\Run: [TFncKy] TFncKy.exe /Type 10
O4 - HKLM\..\Run: [dla] C:\WINDOWS\system32\dla\tfswctrl.exe
O4 - HKLM\..\Run: [Apoint] C:\Program Files\Apoint2K\Apoint.exe
O4 - HKLM\..\Run: [TosHKCW.exe] C:\Program Files\TOSHIBA\Wireless Hotkey\TosHKCW.exe
O4 - HKUS\S-1-5-18\..\RunOnce: [RunNarrator] Narrator.exe (User 'SYSTEM')
O4 - HKUS\.DEFAULT\..\RunOnce: [RunNarrator] Narrator.exe (User 'Default user')
O4 - Startup: Books on Loan (Reminder).lnk = C:\BOOK\BOOK.EXE
O4 - Global Startup: Adobe Reader Speed Launch.lnk = C:\Program Files\Adobe\Acrobat 7.0\Reader\reader_sl.exe
O4 - Global Startup: AutorunsDisabled
O8 - Extra context menu item: &Google Search - res://C:\Program Files\Google\GoogleToolbar1.dll/cmsearch.html
O8 - Extra context menu item: &WordWeb... - res://C:\WINDOWS\System32\wweb32.dll/lookup.html
O8 - Extra context menu item: Backward &Links - res://C:\Program Files\Google\GoogleToolbar1.dll/cmbacklinks.html
O8 - Extra context menu item: Cac&hed Snapshot of Page - res://C:\Program Files\Google\GoogleToolbar1.dll/cmcache.html
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~3\Office10\EXCEL.EXE/3000
O8 - Extra context menu item: Si&milar Pages - res://C:\Program Files\Google\GoogleToolbar1.dll/cmsimilar.html
O8 - Extra context menu item: Translate Page - res://C:\Program Files\Google\GoogleToolbar1.dll/cmtrans.html
O9 - Extra button: (no name) - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.5.0_09\bin\ssv.dll
O9 - Extra 'Tools' menuitem: Sun Java Console - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.5.0_09\bin\ssv.dll
O9 - Extra button: Related - {c95fe080-8f5d-11d2-a20b-00aa003c157a} - C:\WINDOWS\web\related.htm
O9 - Extra 'Tools' menuitem: Show &Related Links - {c95fe080-8f5d-11d2-a20b-00aa003c157a} - C:\WINDOWS\web\related.htm
O9 - Extra button: (no name) - {CD67F990-D8E9-11d2-98FE-00C0F0318AFE} - (no file)
O16 - DPF: Microsoft WFC Forms Designer - file://D:\VJ98\wfcforms.cab
O16 - DPF: Visual Studio 6 Extensibility Libraries - file://D:\VJ98\vstudio6.cab
O17 - HKLM\System\CCS\Services\Tcpip\..\{CC4A93D0-031C-4176-927D-99E93FF78295}: NameServer = 217.171.132.1 217.171.135.1
O23 - Service: PsShutdown (PsShutdownSvc) - Systems Internals - C:\WINDOWS\PSSDNSVC.EXE
O23 - Service: Broadcom Wireless LAN Tray Service (wltrysvc) - Unknown owner - C:\WINDOWS\System32\wltrysvc.exe
--
End of file - 4505 bytes