Just because security holes and vulnerabilities get reported to software vendors doesn't mean they are actually patched. A new report from IBM's X-Force security team found that of all the software holes reported in the first half of this year, more than half are still unpatched.
IBM's X-Force report is published twice per year and provides an in-depth look at software security from across the spectrum of developers. So far this year, the bug catchers are doing better than the bug squashers. More bugs are being reported, but more are going unpatched.
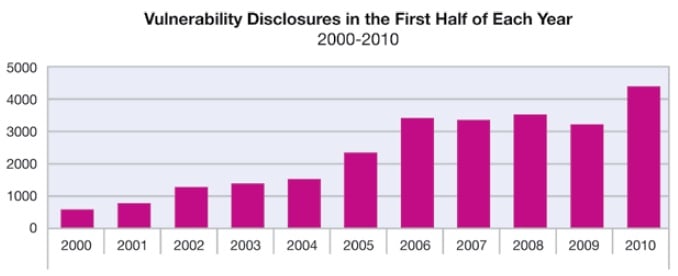
In the first six months of 2010, 4,396 new vulnerabilities were documented and reported to software vendors, a 36 percent increase over the same period last year. However, as of the writing of the report, 55 percent of those vulnerabilities had no vendor-supplied patch. Last year, 52 percent of the known vulnerabilities were unpatched, so the trend is definitely in the wrong direction.
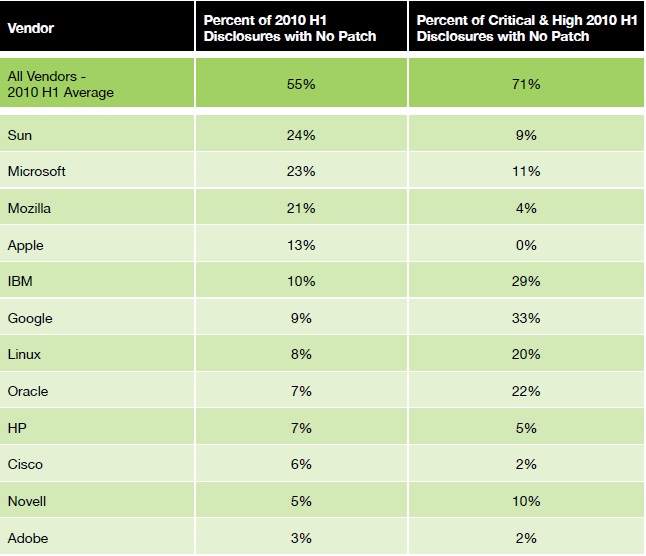
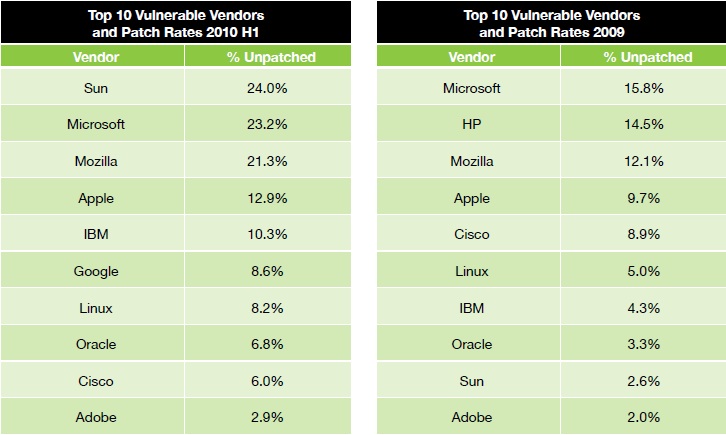
That problem is made worse by the fact that the security we've all come to depend on is becoming increasingly worthless. "We have seen traditional security solutions become wholly ineffective against new methods of obfuscation and low-volume attack vectors. Attacks targeting Web servers via SQL injection and cross-site scripting are nothing new, but they continue to be creatively concealed to bypass many security products," IBM researchers wrote in the report. The 55 percent figure is cumulative of all the major software vendors tracked. The worst offender was Sun, now a part of Oracle (NASDAQ: ORCL). It did not plug 24 percent of reported open security holes, the majority of which were in Java. Then again, Sun has been in a state of chaos for some time due to the protracted acquisition by Oracle.
Microsoft (NASDAQ: MSFT) is in second place with 23.2 percent of unpatched bugs, up from 15.8 percent last year. The Mozilla Foundation is third with 21.3 percent of bugs unpatched, a near doubling of the 12.1 percent from last year. Apple (NASDAQ: AAPL) is fourth with 12.9 percent, IBM (NYSE: IBM) is fifth at 10.9 percent.
HP (NYSE: HPQ) had been number two in 2009, with 14.5 percent of the unpatched vulnerabilities. But it has improved so much that it dropped off the list. Adobe Systems (NASDAQ: ADBE), long maligned by Apple for vulnerabilities in Flash, has only a 3 percent unpatched rate, a better rate than Apple's. However, none of Apple's unpatched bugs are considered critical, while 2 percent of Adobe's were considered critical.
The report says more than half (55 percent) of vulnerabilities come in the form of Web application bugs, and it should come as no surprise that two of the most popular forms of attacks are JavaScript and PDF exploits. IBM said it found a 37 percent year-over-year increase in PDF attacks alone, thanks in part to a botnet called Zeus. Botnets are a massive number of compromised computers with malware hidden on them and running in the background, unbeknownst to the user. They do everything from send out spam to launch other malware attacks.
The Zeus botnet monitors Internet traffic on the infected PC and reports information back to a central command and control sever. The information collected varies, but usually it's designed to collect bank account information. An update to the botnet this year gave it new life to cause considerable financial damage.
It seems ironic, then, that IBM would report phishing is on the decline. Phishing is the process of trying to obtain vital information from a compromised computer, like bank account information, which is exactly what Zeus does. But while Zeus made its presence known, overall, phishing dropped 82 percent from 2009 levels, according to IBM. The U.S. and Europe make up 98.8 percent of the targets of phishing attacks. "Threat dynamics continue to multiply and evolve at a furious pace, making it more crucial than ever to look at unfolding trends so we can better prepare our clients for the future," said Steve Robinson, general manager of IBM Security Solutions in a statement. "This year's X-Force report reveals that although threats are on the rise, the industry as a whole is getting much more vigilant about reporting vulnerabilities. This underscores the increased focus among our clients to continue looking for security solutions that help them better manage risk and ensure their IT infrastructure is secure by design."
One of those changing dynamics is virtualization. In the last four years, the number of vulnerabilities has exploded, and many of them are critical bugs. VMware, the biggest name in virtualization, accounted for 80 percent of known bugs. Every other vendor was in single digits.
Part of the problem is third-party developers. IBM noted that every year since 2005, except for 2007, the number of vulnerabilities from third-party virtualization providers has exceeded the number from vendors like VMware, Citrix and Microsoft.
The IBM X-Force Trend and Risk Report is available here as a PDF, free registration required.