Menu
Menu
DaniWeb
Log In
Sign Up
Read
Contribute
Meet
Search
Search
About 1,000 results for
government
- Page 1
Re: How I get big data for statistical analysis of my pre seed pitch deck
Digital Media
UI / UX Design
2 Months Ago
by rproffitt
… what you want can't be in the USA. Our
government
has enabled DOGE to break through any security there was…
Re: What makes a technical E-commerce web standout?
Programming
Web Development
2 Months Ago
by simplixi
… or influencers to increase brand visibility. - Partner with NGOs or
government
programs focused on housing to tap into larger projects. **9…
Re: How would we poison AI web crawls?
Hardware and Software
Information Security
2 Months Ago
by rproffitt
Update February 25, 2025 as others are kicking it into high gear to resist certain
government
data collecting. 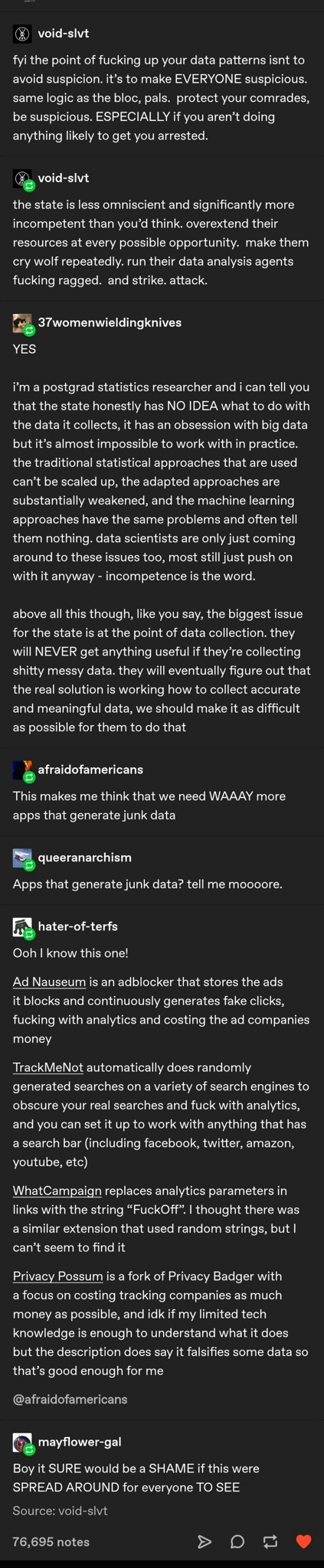 And here I was only thinking about poison for the AI bots.
Re: What do you do for work?
Community Center
Geeks' Lounge
1 Month Ago
by rproffitt
… to representatives which I find with 5calls.org and the
government
web pages. We are living the part of the story…
Re: ‘Advanced AI should be treated similar to Weapons of Mass Destruction’
Community Center
2 Months Ago
by rproffitt
UPDATE: Feb 4, 2025 — Google on Tuesday updated its ethical guidelines around artificial intelligence, removing commitments not to apply the technology to weapons or surveillance.
Re: Government Saves Billions Using Open Source Software. Really?
Hardware and Software
Linux and Unix
14 Years Ago
by nmstategov
Government
workers (especially those in State/Local govenments) are generally not …
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by bumsfeld
Government
label on a chair: "This is not a ladder."
Government Social Media Site Sold
Digital Media
Digital Marketing
15 Years Ago
by slfisher
…been sold to GovDelivery Inc., a venture-backed
government
communications platform, with GovLoop founder Steve Ressler as …quot;]GovDelivery [/URL]is "a supplier of
government
-to-citizen email and wireless communication systems (mostly…gartner.com/andrea_dimaio/2009/09/29/high-profile-
government
-social-network-gets-acquired-what-is-govloops-…
Government Saves Billions Using Open Source Software. Really?
Hardware and Software
Linux and Unix
16 Years Ago
by khess
…software, like Linux and OpenOffice.org, the federal
government
would save billions of dollars in IT costs. …source software--though admitting that, in fact, the
government
can enjoy significant savings by using cloud computing and…It takes a significant economic disaster for the federal
government
to start looking for ways to save money? Really…
Re: Government Social Media Site Sold
Digital Media
Digital Marketing
15 Years Ago
by InsightsDigital
This is no surprise to me. Look at the USPS, I read somewhere that it will be run by private company soon and mostly computerized kiosks. I went to a post office in the 90's that is like that. Anyway going back to this blog post, this buy can start a trend among
government
sites and properties. What do you think?
Re: Government Social Media Site Sold
Digital Media
Digital Marketing
15 Years Ago
by MktgRob
I don't know if it will start a trend but if it is financially prudent to move the day-to-day management to a private, 3rd party group, I am all for better fiscal decisions by the
government
. I just hope that whatever info that is moving around these sites are secure and that the 3rd party firms are fully vetted and regularly monitored!
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by MidiMagic
… 72 PERCENT TO
GOVERNMENT
DANGER: STRESS FROM TOO MUCH
GOVERNMENT
CAUSES OBESITY. CAUTION:
GOVERNMENT
ID NUMBERS CAUSE … HIGH TAXATION DESTROYS JOBS. WARNING: THE LATEST
GOVERNMENT
-REQUIRED OBESITY SOLUTION CAUSES DIARRHEA. WARNING: DON'T…TIME, EVEN THOUGH IT WASTES ENERGY WARNING:
GOVERNMENT
HAS DESIGNED ELECTIONS SO THERE IS NO …
Re: Government Saves Billions Using Open Source Software. Really?
Hardware and Software
Linux and Unix
16 Years Ago
by OlyComputers
The
government
has used open source for years, Los Alamos started implementing … use Windows, and if every desk jockey in the US
government
needs 10 hours of IT help to save a $120… VLK license, you run into problems. The
government
, and most organizations, should be using open source for their…
Re: Government Saves Billions Using Open Source Software. Really?
Hardware and Software
Linux and Unix
16 Years Ago
by khess
… up there in Los Alamos. When I think of Federal
government
, here in the states, I'm not generally thinking of…
Government gets tough on pirates after Mandy dines with Geffen
Hardware and Software
Networking
15 Years Ago
by happygeek
…which was published by none other than the UK
Government
itself. Of course, the turnaround could have nothing…mandelson-s-filesharing-corfu-link-denied-$1321086.htm"]
Government
spokesperson[/URL] who said "I believe …quot;a disproportionate response." Here's what the
Government
has to say about ISP account suspension: [QUOTE…
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by GrimJack
…quote=jwenting;448024]to install some sense of what the
government
is actually spending on things into its own staff. … at this time, to point out that no US
government
official ever threw a 20 million dollar birthday party that… I know that all you Libertarian/conservative/Republican anti-
government
types love to castigate the Feds but there is no…
Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by Lardmeister
You know that our
government
's answer to any problem is to attach a label. … of being overrun. I like to help our hard working
government
staff with this suggested label to be attached to every… when driving!" No doubt, you yourself can help your
government
too, and give us a helpful label suggestion.
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by jwenting
to install some sense of what the
government
is actually spending on things into its own staff. They… is real. I've spent some time working for a
government
department myself (as an outside contractor) and we (all … used). Things like that happen every year in almost every
government
department around the world. And to the people working there…
Government crackdown on happy slapping cyber bullies
Hardware and Software
macOS
17 Years Ago
by happygeek
The UK
government
has started a concerted [URL="http://yp.…"particularly insidious type of bullying." According to
government
figures more than one third of teenagers between the ages…emails and Internet video clips. Amongst the recommendations from the
government
, that teachers confiscate mobile phones and laptops. Simon Sinnot, …
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by vegaseat
Interesting story jwenting, so what kind of
government
label should be attached to each
government
purchase order (or employee) to prevent this waste?
Re: Government shutting down food stamps & WIC program
Community Center
Geeks' Lounge
11 Years Ago
by Ancient Dragon
The us
government
spends about $60 BILLION per DAY. That cannot go on … like you have to control your own spending the US
government
needs to do the same. So how are they supposed… to control spending? Simple, by reducing the size of
government
, stop all the pork bills, stop entitlements, and stop foreign…
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by jwenting
yah, the noise is there for the deaf, the light for the blind. Anything the
government
"produces" (iow, makes available internally or externally in its organisations) should carry a label mentioning the exact cost in tax money of the item. This should extend from sachets of coffee creamer in the canteen to vehicles and buildings.
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by Lardmeister
These guys are heavily armed foreign mercenaries that pretty much behave like the Mafia. They escort US, British or Australian civilian
government
convoys, and shoot at pretty much anything they don't like.
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by harry truman
The ultimate stupidity will be when
government
decides it is in our best interest and that of our "ailing planet" to require all products state their CARBON FOOTPRINT.
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by bumsfeld
[QUOTE=harry truman;463404]The ultimate stupidity will be when
government
decides it is in our best interest and that of our "ailing planet" to require all products state their CARBON FOOTPRINT.[/QUOTE]Maybe number of black footprint images covering the package, so that bag of charcoal would be totally covered.
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by GrimJack
[quote=Lardmeister;446974]You know that our
government
's answer to any problem is to attach a label. …
Re: Government Labels I like To See
Community Center
Geeks' Lounge
17 Years Ago
by vegaseat
A
government
authorized label on each reindeer (Rangifer tarandus): "Do not attempt to fly this animal"
Re: Government crackdown on happy slapping cyber bullies
Hardware and Software
macOS
17 Years Ago
by happygeek
Is that not just the greatest name for a member of the
government
ever? Ed [B]Balls[/B]. Brilliant...
Government Surveillance of Social Media Sites Questioned
Digital Media
Digital Marketing
15 Years Ago
by slfisher
…/social_networking_FOIA_complaint_final.pdf"]filed suit[/URL] against a number of
government
agencies for refusing to disclose their policies for using social… Security, and other agencies, asking for information about how the
government
collects and uses social media information. Several agencies did not…
Re: Government Surveillance of Social Media Sites Questioned
Digital Media
Digital Marketing
15 Years Ago
by MktgRob
If the
government
is scanning social media for evidence of illegal activity, I have no problem with that. If the
government
is scanning social media to identify dissenting opinion with the purpose of eventually suppressing the opinions, then I have a problem with it.
1
2
3
17
Next
Last
Search
Search
Forums
Forum Index
Hardware/Software
Recommended Topics
Programming
Recommended Topics
Digital Media
Recommended Topics
Community Center
Recommended Topics
Latest Content
Newest Topics
Latest Topics
Latest Posts
Latest Comments
Top Tags
Topics Feed
Social
Top Members
Meet People
Community Functions
DaniWeb Premium
Newsletter Archive
Markdown Syntax
Community Rules
Developer APIs
Connect API
Forum API Docs
Tools
SEO Backlink Checker
Legal
Terms of Service
Privacy Policy
FAQ
About Us
Advertise
Contact Us
© 2025 DaniWeb® LLC