According to the fourth annual Web Application Attack Report from Imperva retailers suffer from twice as many SQL injection attacks when compared to other industry sectors. What's more, the United States remains the number one source of all web attacks.
Other key findings of the report include the startling revelation that one website was observed to be under attack for 98% of the time, or 176 out of 180 days if you want to be precise. One web application was seen to receive a mind-boggling 94,057 SQL injection requests in a single day which, if you do the math, works out to 1,567 SQL injection attacks per hour or an average of 26 per minute. The typical attack incident lasted around five minutes, but the worst-case incident was about 100 times longer, lasting more than 15 hours. The overall picture isn't as bad as these extremes, obviously, but even so Imperva reports that most web applications will receive four or more web attack campaigns every month.
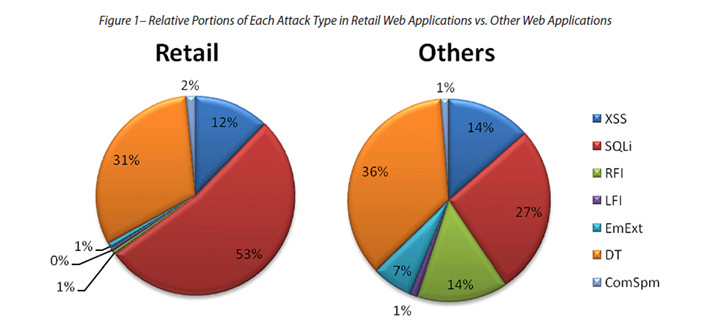
The bottom line from the research though is that retailers are hardest hit, with the intensity of attack being quite brutal both in terms of number of attacks per incident and duration. Retail applications received an average of 749 individual attack requests per attack campaign. The Imperva analysis suggests that SQL injection attacks on retail applications consisted of more HTTP requests and lasted longer than SQL injection attacks on other applications. This is largely attributable to the design, and the size, of the applications. Think about it, a retail application is likely to contain a relatively large number of pages (online catalogs) hence the length and intensity of the SQL injection attacks hitting them.
Amichai Shulman, CTO at Imperva comments "while these findings undeniably demonstrate that web application attacks are far from consistently distributed, the takeaway is that organizations should base security measures on the worst case scenario, not on the average case. We believe that, with the current threat landscape, organizations can no longer afford to take an every-man-for-himself approach to security. This report demonstrates that the automation and scale of attacks leave a large footprint that can be better addressed by looking at data gathered from a large set of potential victims. Thus it is important to rely on one’s peers to acquire intelligence on malicious sources and apply this intelligence in real time."
