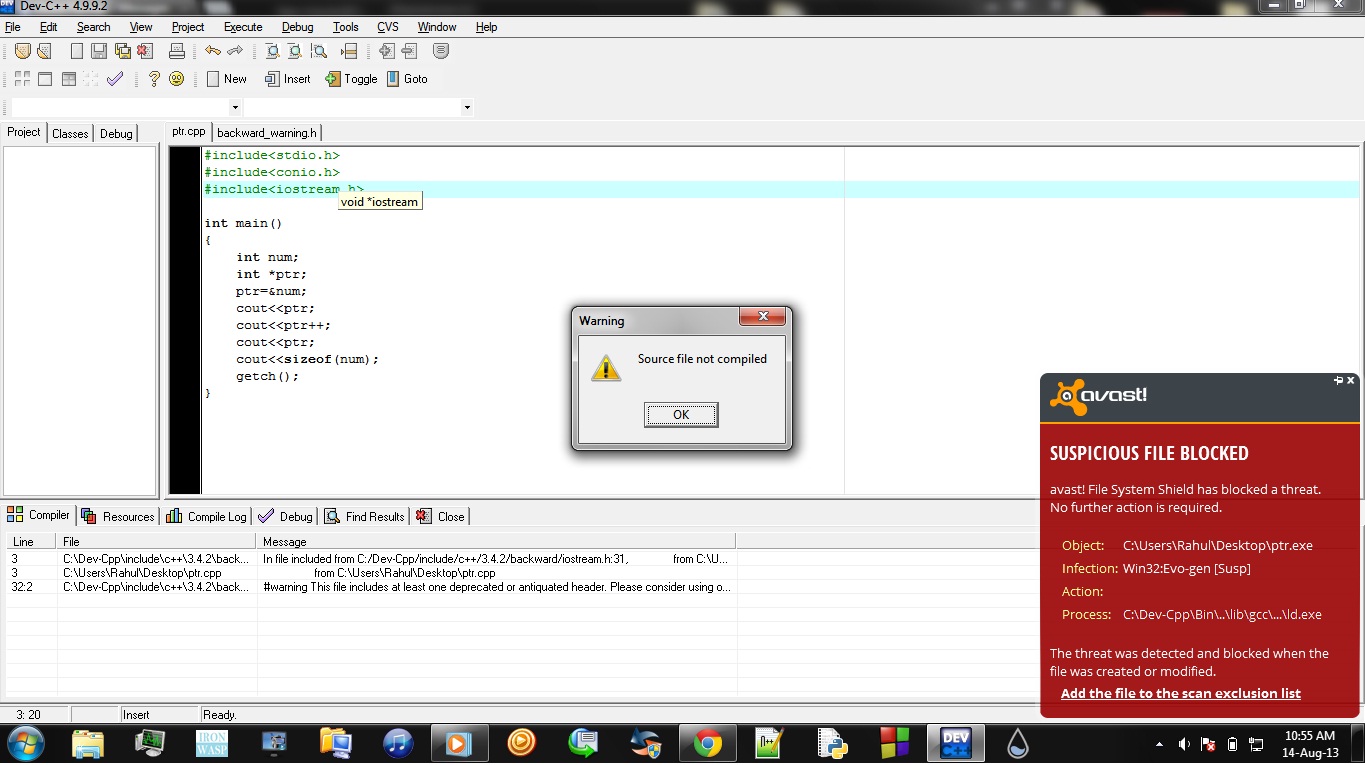
This simple program of pointer generating THREAT Warning and identified as MALWARE. I dont see HOW ?
#include<stdio.h>
#include<conio.h>
#include<iostream.h>
int main()
{
int num;
int *ptr;
ptr=#
cout<<ptr;
cout<<ptr++;
cout<<ptr;
cout<<sizeof(num);
getch();
}
Thanx.
