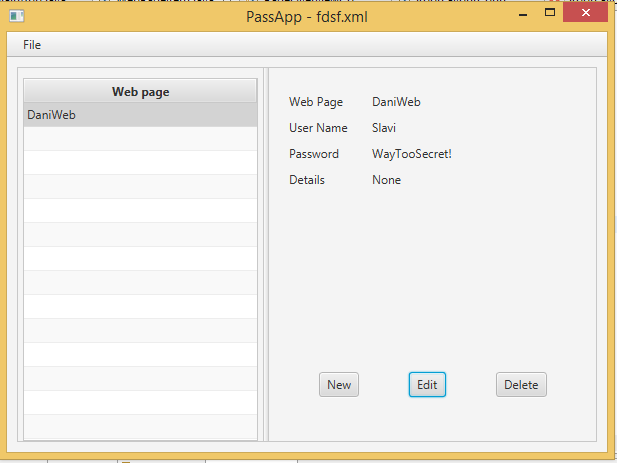
In the past couple of days, I've been practicing with JavaFX and I made myself an app, which I am planning to use in the future. It is supposed to keep track of web pages and the passwords I use for them, usernames as well of course. The program itself works great now, however, when I have to keep the state/last used(or already written in) items, I am facing a problem. Mainly, databases are used for such purpose, arent they? However, right now I am having java objects as my data, not database items or what they are called. How should I save my information? Currently, I am saving to an XML file, and then reading from the file, but I have no idea whether that is a good practice to do so
This is how the app looks like( Only missing CSS to make it fancy)