It has been officially confirmed that the php.net website of the open-source PHP programming language has been hacked and infected with malware. The successful breach of the site came to light yesterday morning when the Google Safe Browsing service started flagging php.net as serving up malicious scripts. This was, at first, denied by php.net which Tweeted claims that it was down to a false negative by Google. However, that position has changed and now it has been officially confirmed that two servers at php.net had been hacked and were, indeed, hosting malicious code in order to install malware on the computers of unsuspecting visitors.
It would appear that the breach occurred on Tuesday, and the infection window was open through until Thursday morning when spotted by Google. The site has now been relocated to a clean set of servers, and there is absolutely no suggestion that any of the PHP code itself has been compromised in any way so developers can breathe a sigh of relied there at least. If you have visited the php.net site during that attack window period though, it might be a good idea to double-check that your systems have not been infected.
It seems that the breach itself was surprisingly straightforward in approach, rather old-school in fact, with the use of an iFrame injection technique pointing to the Magnitude exploit kit and ultimately dropping a Trojan known as Tepfer onto the visiting computer. Up to date AV scanners should be able to detect if your computer was infected or not, in case you are concerned.
Official statements from officials at the php.net site reveal that the attack was at first thought to be a false positive by Google as "we had some minified/obfuscated javascript being dynamically injected into userprefs.js" and while this looked suspsicious "it was actually written to do exactly that so we were quite certain it was a false positive". However, analysis of the static.php.net access logs revealed it was periodically serving up userprefs.js with the wrong content length and then reverting back to the right size after a few minutes. "This is due to an rsync cron job" the statement continues "So the file was being modified locally and reverted. Google's crawler caught one of these small windows where the wrong file was being served, but of course, when we looked at it manually it looked fine."
The statement goes on to confirm that after a quick git fsck --no-reflog --full --strict on all the PHP repos plus a manual check of the md5sums for PHP distribution files "we see no evidence that the PHP code has been compromised".
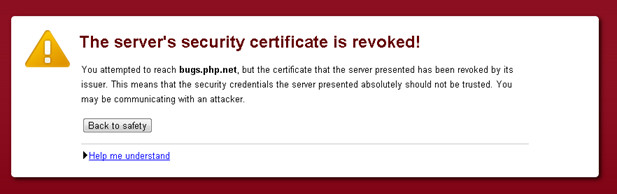
In the meantime, as there is a possibility that the attackers could have accessed the private key of the php.net SSL certificate, this has been revoked by the owners who are currently in the process of getting a new one. Access to those php.net sites requiring SSL, which includes bugs.php.net and wiki.php.net, should be back real soon now folks.
Keep an eye on the updates on Twitter from @official_php.
