Security researchers are warning that some 30,000 WordPress websites, 85% of them based in the US, have been compromised by a mass-injection hijack attack which sees visitors to any of more than 200,000 individual pages redirected to a Trojan infected rogue AV scam.
The senior security researcher with Websense Labs, Elad Sharf, admits that while rogue AV is old hat these days it's obviously still a money-making exercise and one that turns enough profit for the bad guys for them to keep plodding away at it. "With such a high number of compromised web pages and websites in this on-going campaign, it's evident these scams are still working. Websense Security Labs has been following this mass injection campaign for months and we've seen over 200k web pages and close to 30k unique websites compromised" Sharf says, adding "vulnerable websites are a rich source of opportunity for cybercriminals".
According to the researchers who have been working with data from the Websense Threatseeker Network, the vast majority of the targets of this latest mass-injection exploit are based in the US. In fact, some 85% of them it would seem, and most are also hosted by the WordPress content management system.
The actual code that is injected into these vulnerable sites is pretty short, as is the norm, and can be found nestling just before the closing 'body' tag at the bottom of an infected page. What it does is the same old same old, hijacking unsuspecting visitors to those pages and redirecting them, via a three-level chain in this instance, to a rogue AV site where social engineering and fear factor techniques are employed in an attempt to get them to install malware in the form of a Trojan.
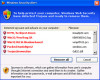
Websense Security Labs discovered that the first link in the redirection chain points to a rr.nu domain (which is the South Pacific island state of Niue) and ultimately drops the user onto a landing page at a de.lv domain in Latvia. Or at least it may be, as the landing page is changing all the time so the researchers have found. One thing that doesn't change is what happens when the victim arrives, and that is the fake scanning of the computer which results in a 'you are infected' popup claiming a bunch of equally fake malware detections.
The bad guys have made the page look as much like a Windows Explorer window as possible, complete with a Windows Security Alert dialogue box in order to help convince the victim that everything is genuine. If successful, the victim will follow the prompts to download and install an antivirus application which is nothing of the sort, instead being a Trojan executable