When a CALL instruction is executed, the address of the current instruction is pushed into the stack. Then, the execution makes an unconditional JMP to the address specified as the parameter of the call instruction.
.code
Test:
call delta
delta:
pop ebp
sub ebp,offset delta
mov esi,[esp]
and esi,0ffff0000h
push 0
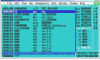
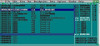
call ExitProcessScreen shot (unable to paste here from the word file hence attaching it) of debugger after the call instruction is executed is as below:
00401000 call test. 00401005
00401005 pop ebp
esp 0012FFC0
eip 00401005The current code address is: 00401005. (True. EIP confirms this fact).
This address is supposed to have been pushed to stack.
This address is on the top of the stack. (True. EBP shows it after the POP).
And below is the sketch of my partially faulty assumption and understanding.
That, ESP points to the top of the stack.
But, ESP Does not shows 4001005, but another value 0012FFC0.
Request help... a little illumination on this situation.
Thank you.