You know you are old when a student wants to interview you as part of a piece about 'Internet history' and you realise it's becuase you were there at the time.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
LastMitch commented: Thanks for the article! +2
diafol commented: hilarious! +14
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
androtheos commented: I like dwindera but happygeek seems to describe you better. +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
 Although the physical threat does, in fact, cross over into the world of IT (at least hypothetically) with the possibility of a state sponsored hacking or malware attack on critical national infrastructure such as electricity supplies, the reality is likely to be less James Bond and more mundane in approach.
Although the physical threat does, in fact, cross over into the world of IT (at least hypothetically) with the possibility of a state sponsored hacking or malware attack on critical national infrastructure such as electricity supplies, the reality is likely to be less James Bond and more mundane in approach.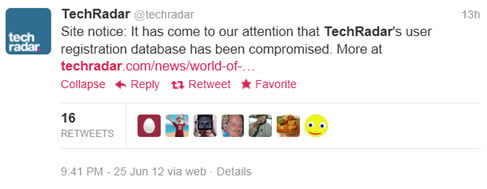 Late last night the site, owned by magazine giants Future Publishing and which gets in excess of seven million visitors from around the world each month, made the announcement on Twitter and the website forums were closed while an investigation into the breach is underway. According to an official statement from Nick Merritt "user details including username, email address, date-of-birth and encrypted passwords have been stolen" due to the compromise of the user registration database for the site.
Late last night the site, owned by magazine giants Future Publishing and which gets in excess of seven million visitors from around the world each month, made the announcement on Twitter and the website forums were closed while an investigation into the breach is underway. According to an official statement from Nick Merritt "user details including username, email address, date-of-birth and encrypted passwords have been stolen" due to the compromise of the user registration database for the site. Here's the problem: ask Google "How busy is it in New York?" and you will be confronted by a whole bunch of results which don't answer you query at all. In fact, I've just done exactly that and the first result unhelpfully told me what time it was in NYC, and this was followed by equally poor results including a three years old news story concerning Anne Hathaway, tripadvisor.com reviews of Washington Square and a story about the construction of the Freedom Tower (One World Trade Center) but absolutely nothing to help me gauge how bust New York City is.
Here's the problem: ask Google "How busy is it in New York?" and you will be confronted by a whole bunch of results which don't answer you query at all. In fact, I've just done exactly that and the first result unhelpfully told me what time it was in NYC, and this was followed by equally poor results including a three years old news story concerning Anne Hathaway, tripadvisor.com reviews of Washington Square and a story about the construction of the Freedom Tower (One World Trade Center) but absolutely nothing to help me gauge how bust New York City is.




 The vulnerability impacts users of all currently supported versions of Windows including Windows 7, as well as Microsoft Office 2003 and 2007 and is serious enough that a successful exploit as seen in both the attacks discovered this week can launch a drive-by compromise which simply requires a user to visit the infected website to become a victim. Assuming, that is, they do not have anti-malware protection installed that spots the thing or have disabled JaveScript which it uses. Both the sites identified by SophosLabs had four files dropped into them by the attackers: deploy.html containing the vulnerability itself and loading the JavaScript library deployJava.js which interrogates your browser, movie.swf is then run if possible in order to compromise your computer and for good measure an iframe is loaded into faq.htm as well. The end result is that the attacker can potentially gain the same user rights as whoever is using the target computer at the time.
The vulnerability impacts users of all currently supported versions of Windows including Windows 7, as well as Microsoft Office 2003 and 2007 and is serious enough that a successful exploit as seen in both the attacks discovered this week can launch a drive-by compromise which simply requires a user to visit the infected website to become a victim. Assuming, that is, they do not have anti-malware protection installed that spots the thing or have disabled JaveScript which it uses. Both the sites identified by SophosLabs had four files dropped into them by the attackers: deploy.html containing the vulnerability itself and loading the JavaScript library deployJava.js which interrogates your browser, movie.swf is then run if possible in order to compromise your computer and for good measure an iframe is loaded into faq.htm as well. The end result is that the attacker can potentially gain the same user rights as whoever is using the target computer at the time. Sound familiar? Well that's because this has the hand of the LinkedIn password hacker all over it. As
Sound familiar? Well that's because this has the hand of the LinkedIn password hacker all over it. As 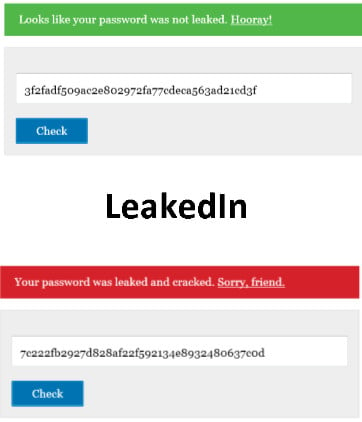 The list of compromised passwords was published in a file that contained the passwords in unsalted SHA-1 hashed form, and appeared online in a Russian based public forum. I am led to believe that at least a quarter of a million of these hashes have been cracked, and that number will inevitably increase as the cracking work continues. Although no associated account data such as usernames were published within the file, at this point in time it is unknown if the hackers have access to this information or not.
The list of compromised passwords was published in a file that contained the passwords in unsalted SHA-1 hashed form, and appeared online in a Russian based public forum. I am led to believe that at least a quarter of a million of these hashes have been cracked, and that number will inevitably increase as the cracking work continues. Although no associated account data such as usernames were published within the file, at this point in time it is unknown if the hackers have access to this information or not.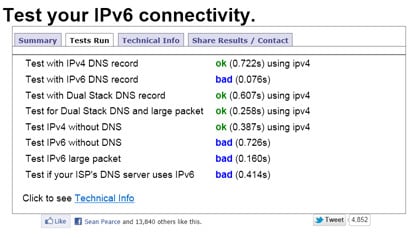 The chances are pretty high that, for now, your test results will not be 'awesome' in regards to IPv6 connectivity but then neither is it 'critical' that they should be right now. It may be World IPv6 Launch Day but that doesn't mean that the Internet will somehow stop working from now on if you remain an IPv4 user for the foreseeable …
The chances are pretty high that, for now, your test results will not be 'awesome' in regards to IPv6 connectivity but then neither is it 'critical' that they should be right now. It may be World IPv6 Launch Day but that doesn't mean that the Internet will somehow stop working from now on if you remain an IPv4 user for the foreseeable …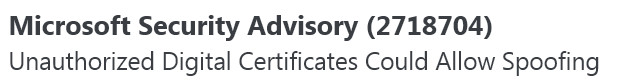 At first the advisory with the expanded title of "Unauthorized Digital Certificates Could Allow Spoofing" issued on June 3rd doesn't hold out much hope in the immediately interesting stakes. However, when you realise that components of the Flame worm (
At first the advisory with the expanded title of "Unauthorized Digital Certificates Could Allow Spoofing" issued on June 3rd doesn't hold out much hope in the immediately interesting stakes. However, when you realise that components of the Flame worm (
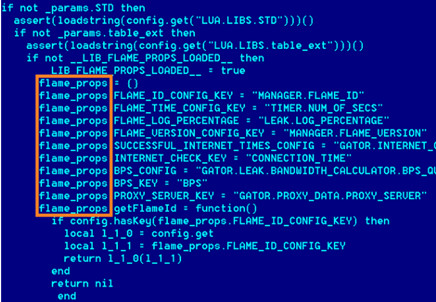 Perhaps the most surprising piece of information that has emerged about this cyber weapon is that it appears to have been first fired some two years ago in 2010. At present, however, there are no clues as to which nation-state is behind the worm. That is if it is, indeed, a state-sponsored attack at all. The chances do appear high that it is, given the complexity of the code and the fact that this isn't some bank login scraping affair or something that delivers a denial of service or site defacement payload. So if we rule out the organised cyber-criminal gangs and the political hacktivists, that only really leaves the nation states. It has been suggested that there are 'similarities' with Stuxnet in the code design itself, but at this moment in time …
Perhaps the most surprising piece of information that has emerged about this cyber weapon is that it appears to have been first fired some two years ago in 2010. At present, however, there are no clues as to which nation-state is behind the worm. That is if it is, indeed, a state-sponsored attack at all. The chances do appear high that it is, given the complexity of the code and the fact that this isn't some bank login scraping affair or something that delivers a denial of service or site defacement payload. So if we rule out the organised cyber-criminal gangs and the political hacktivists, that only really leaves the nation states. It has been suggested that there are 'similarities' with Stuxnet in the code design itself, but at this moment in time …