I wouldn't even give him one, having had the misfortune to have heard some of his output escaping from the bedroom of my 10 year old daughter (pretty much the exact target market I imagine).
But, that said, there is no denying he is popular. I posted a news story last night which reveals that Justin Bieber has overtaken Lady Gaga to have the most viewed YouTube video of all time with his 'Baby' song.
If you are not quite interested enough to click the link and read the full story, the Bieber video had been watched a staggering 247,991,181 at the time of writing, which was less than 12 hours ago.
 However, within 48 hours the inevitable weight of Bieber fans has taken its toll and the Baby video has now pulled well clear with 247,991,181 views compared to 'just' 246,609,606 views for Lady Gaga. To put this in to some kind of perspective, the third most viewed YouTube video of all time is 'Charlie bit my finger - again' featuring a cute kid and his baby brother with 210,601,397 views.
However, within 48 hours the inevitable weight of Bieber fans has taken its toll and the Baby video has now pulled well clear with 247,991,181 views compared to 'just' 246,609,606 views for Lady Gaga. To put this in to some kind of perspective, the third most viewed YouTube video of all time is 'Charlie bit my finger - again' featuring a cute kid and his baby brother with 210,601,397 views. 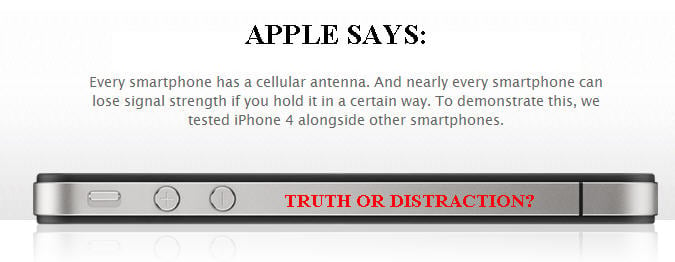 It was
It was  After playing a spoof 'fanbois' video Steve Jobs took to the stage and, standing in front of a banner announcing 'we're not perfect' …
After playing a spoof 'fanbois' video Steve Jobs took to the stage and, standing in front of a banner announcing 'we're not perfect' … Security researchers at Sophos are warning that scammers have struck on Facebook with a message that is spreading fast by proclaiming "I am part of the 98.0% of people that are NEVER gonna drink Coca Cola again after this HORRIFIC video" and which includes a link.
Security researchers at Sophos are warning that scammers have struck on Facebook with a message that is spreading fast by proclaiming "I am part of the 98.0% of people that are NEVER gonna drink Coca Cola again after this HORRIFIC video" and which includes a link. If you hit this link, you get taken to a survey section which …
If you hit this link, you get taken to a survey section which …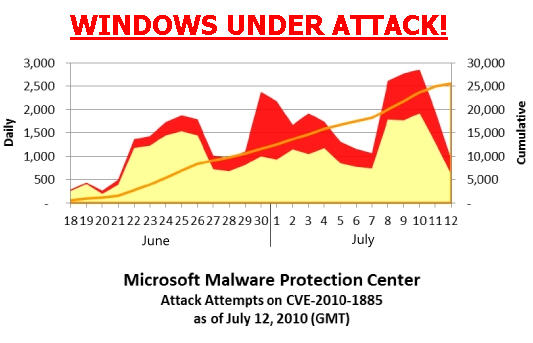 According to
According to 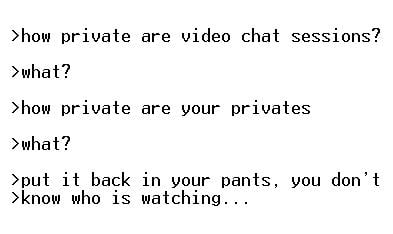 If you have ever been tempted, like so many male Chatroulette users, to show complete strangers the contents of your trousers new security research might persuade you not to join in this offensive nonsense. Video chat services such as Chatroulette enable random strangers to get virtually connected, but the lure of perceived anonymity and a somewhat ironic assumption of privacy has meant that it has attracted a somewhat unsavoury crowd of what a few years ago we would have called flashers or perhaps more correctly perverts.
If you have ever been tempted, like so many male Chatroulette users, to show complete strangers the contents of your trousers new security research might persuade you not to join in this offensive nonsense. Video chat services such as Chatroulette enable random strangers to get virtually connected, but the lure of perceived anonymity and a somewhat ironic assumption of privacy has meant that it has attracted a somewhat unsavoury crowd of what a few years ago we would have called flashers or perhaps more correctly perverts.  The latest
The latest  As the new
As the new  According to a recent analysis by
According to a recent analysis by  Hennessey is the audio and telecomms buyer for UK retailer John Lewis, and during an event in London where he presented a sneak preview look at what the retail chain would be stocking this Christmas he included a slide entitled 'Apple iPod refresh in September' complete with photos and feature descriptions. You can see that slide featuring
Hennessey is the audio and telecomms buyer for UK retailer John Lewis, and during an event in London where he presented a sneak preview look at what the retail chain would be stocking this Christmas he included a slide entitled 'Apple iPod refresh in September' complete with photos and feature descriptions. You can see that slide featuring  Get Safe Online and ABTA, the UK travel industry association, are now warning holidaymakers not to ignore basic online fraud-prevention measures when looking for a holiday bargain on the Web and suggesting that some might be handing over hard-earned cash for dream holidays that simply do not exist.
Get Safe Online and ABTA, the UK travel industry association, are now warning holidaymakers not to ignore basic online fraud-prevention measures when looking for a holiday bargain on the Web and suggesting that some might be handing over hard-earned cash for dream holidays that simply do not exist.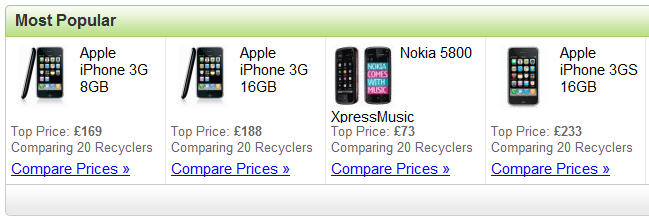 I was recently checking out what kind of recycling value
I was recently checking out what kind of recycling value  Was it really over three years ago now that I penned a story here on DaniWeb entitled
Was it really over three years ago now that I penned a story here on DaniWeb entitled  As well as using Justin Bieber video clips as the bait for the attack, the hackers also took the opportunity to leave abusive and obscene comments about the popular teen idol singer. A number of banner messages even appeared beneath the most popular Bieber videos proclaiming that he was dead.
As well as using Justin Bieber video clips as the bait for the attack, the hackers also took the opportunity to leave abusive and obscene comments about the popular teen idol singer. A number of banner messages even appeared beneath the most popular Bieber videos proclaiming that he was dead. 


 Insisting that he will take the reader on the fastest and easiest route to releasing software, even if they have never written a single line of code before, Tim is obviously not scared of making bold promises. Thankfully, by adopting a 'code as you learn' approach to teaching, he is more than capable of walking the programming tutorial walk. Indeed, by just the second chapter of the book the reader starts to develop their very first program. "We’ll be jumping headfirst into creating applications on the Mac that look and behave like the other Mac applications you’re used to" Isted says, adding that as well as learning general programming principles the reader will put them "into practice in real-world situations, right from the start".
Insisting that he will take the reader on the fastest and easiest route to releasing software, even if they have never written a single line of code before, Tim is obviously not scared of making bold promises. Thankfully, by adopting a 'code as you learn' approach to teaching, he is more than capable of walking the programming tutorial walk. Indeed, by just the second chapter of the book the reader starts to develop their very first program. "We’ll be jumping headfirst into creating applications on the Mac that look and behave like the other Mac applications you’re used to" Isted says, adding that as well as learning general programming principles the reader will put them "into practice in real-world situations, right from the start".  Monica Basso, research vice president at Gartner, points to how the productivity gains achieved with using wireless e-mail are driving adoption beyond the purely executive reach and reveals that "in 2010, enterprise wireless e-mail is still a priority for organizations, whose mobile workforces are up to 40 per cent of the total employee base. Most midsize and large organizations in North America and Europe have deployed enterprise wireless e-mail already, but on average, for less than five percent of the workforce."
Monica Basso, research vice president at Gartner, points to how the productivity gains achieved with using wireless e-mail are driving adoption beyond the purely executive reach and reveals that "in 2010, enterprise wireless e-mail is still a priority for organizations, whose mobile workforces are up to 40 per cent of the total employee base. Most midsize and large organizations in North America and Europe have deployed enterprise wireless e-mail already, but on average, for less than five percent of the workforce."