Bradley Davies should hang his head in shame, deserved a red - hope gets a ban for that. Not needed at all. Almost cost Wales the match as well....
Very deserved win though, Wales look unstoppable at the moment.
Bradley Davies should hang his head in shame, deserved a red - hope gets a ban for that. Not needed at all. Almost cost Wales the match as well....
Very deserved win though, Wales look unstoppable at the moment.
A couple of flaws with that argument:
1. Both ardav and myself are in the UK where nobody cares about the Super Bowl
2. I work for myself, and there's no water cooler in my office - just an espresso machine
:)
As for the Super Bowl, who wants to watch a bunch of girls in padded shirts flouncing around for a few hours. Seriously, what an overrated and boring game that is. I'd rather watch paint dry... ;) (runs and hides)
England stand no chance after that dire performance against an even more dire Scottish side yesterday.
Italy were their normal hard working and enthusiastic but ultimately pretty crap side, while France plodded on to the inevitable result.
I voted Wales, despite being English, as on their World Cup performance they looked like a side that could beat anyone else if they didn't have the assistance of a completely shite ref and, assuming Wales have not lost that edge, will be very hard to beat in the 6N.
I have NO PROBLEM with people responding to old threads as long as:
1. A relevant answer is provided which had not been before
2. The response is not an 'is that job still going' when the OP is 9 years old
3. The response is not a new question hijacking that old thread
4. The response is not just a 'me too' spam in order to get visibility for some links in a signature
PS. I have moved this thread to the Community Feedback forum as it is more appropriate here methinks...
And the most common way to ask for help with a VB6 problem is to ask in the, erm, oh I don't know, how about the VB6 forum?
Moving this thread now...
All right stop, collaborate, and listen. A new variant of the ZeuS financial malware platform known as Ice. This baby Trojan spawned from the original Ice IX is targeting bank customers on both sides of the pond. Here in the UK the 'big three' telecommunications providers are where it is flowing like a harpoon, daily and nightly. One thing is for sure, this ain't no vanilla ice attack.
 OK, rubbish pop rap references apart, this is actually quite a serious deal. The new Ice TX configurations are apparently not only stealing bank account data, as if that weren't bad enough. but also actively capturing telephone account information about BT, Sky and TalkTalk customers as well.
OK, rubbish pop rap references apart, this is actually quite a serious deal. The new Ice TX configurations are apparently not only stealing bank account data, as if that weren't bad enough. but also actively capturing telephone account information about BT, Sky and TalkTalk customers as well.
Why is this such a big deal? I will let Amit Klein, CTRO at banking security vendor Trusteer, explain: "This allows attackers to divert calls from the bank intended for their customer to attacker controlled phone numbers. I believe the fraudsters are executing fraudulent transactions using the stolen credentials and redirecting the bank's post-transaction verification phone calls to professional criminal caller services (discussed in a previous Trusteer blog) that approve the transactions."
Indeed, in one Ice TX attack intercepted by Trusteer, security researchers were able to see how the Trojan first steals the user ID and password of the victim, followed by memorable information and date of birth before then grabbing the account balance of the by now compromised bank account.
What happens next is the interesting, and worrying, …
Pah. I'm just glad I work for myself. I'm a really laid back employer :)
I have full sleeves on both arms, a full chest piece, a full back piece that rises up above the shirt/collar line onto the neck. I also have facial piercings - just a few in my ears now, but when I was first carving out a career (as an IT consultant and freelance journalist) I had twenty piercings in one ear, ten in the other, three eyebrow piercings and two nose ones (not to mention the bits you couldn't see). This was at the very start of the 90's and I worked as a consultant for some very large companies such as Microsoft, Royal Mail etc. My appearance did not matter, my ability to solve the problems these companies were looking to deal with did.
Attitudes have changed dramatically since then, and with tattoos etc much more mainstream these days, I think that the kind of employer who thinks it is a problem is the kind of <insert expletive here> you probably don't want to work for anyway...
I should point out that I'm based in the UK so my experiences reflect that.
What he said.
<an admin>
Women or computers? >;-)
(hiding now, in case my other half is reading...)
The biggest heroes and villains in IT history have been revealed as the results of a new poll are published. Perhaps rather surprisingly, Steve Jobs is just as hated as Bill Gates and Facebook founder Mark Zuckerberg is more hated than both of them. But that's just where the shock results from this particular survey start: wait until you see how people voted in the 'greatest computing hero of all time' section.
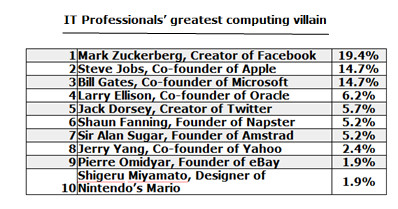 The poll, conducted by IT and Telecoms recruitment specialists Greythorn, asked IT professionals in the United Kingdom who they thought the most unpopular person ever in the history of IT was and the resounding conclusion was Facebook CEO Mark Zuckerberg with a pretty convincing 19.4% share of the vote. Amazingly, given his recent death and hero status amongst many geeks the world over, Apple founder Steve Jobs managed to get exactly the same 14.7% of thumbs down votes as the traditional computer world hate figure of Microsoft founder Bill Gates to come joint second on the list.
The poll, conducted by IT and Telecoms recruitment specialists Greythorn, asked IT professionals in the United Kingdom who they thought the most unpopular person ever in the history of IT was and the resounding conclusion was Facebook CEO Mark Zuckerberg with a pretty convincing 19.4% share of the vote. Amazingly, given his recent death and hero status amongst many geeks the world over, Apple founder Steve Jobs managed to get exactly the same 14.7% of thumbs down votes as the traditional computer world hate figure of Microsoft founder Bill Gates to come joint second on the list.
Just behind them were the flamboyant Larry Ellison (co-founder of Oracle), Jack Dorsey (founder of Twitter), Shaun Fanning (founder of Napster), Sir Alan Sugar (founder of Amstrad), Jerry Yang (founder of Yahoo), Pierre Omidyar (founder of eBay) and totally bafflingly Shigeru Miyamato (designer of Nintendo's Mario).
The whole list is, to be honest, rather confusing. I can understand people having a beef with the Facebook and Twitter creators over privacy issues perhaps, and the Mac vs PC …
Erm, no, of course not. If you made the mistake then you should correct it free of charge and not expect your client to pay for your ineptitude.
But both your links which have been deleted, covering very different subjects, pointed to the same site. I would hazard a guess one which you are involved with. Now that's advertising/self promotion however you want to spin it and as such it is against the rules here.
At least you didn't include a spam link this time...
I think you have a good point there, not least as I currently have an iPhone 4 (couple of months left on contract) and an iPhone 4S. Erm, guilty as charged methinks :)
Welcome aboard squire :)
Is Apple really 'closing the gap' on Android as far as smartphone market share is concerned, or is there more to the battle of the mobile handsets than the latest set of headline figures suggest?
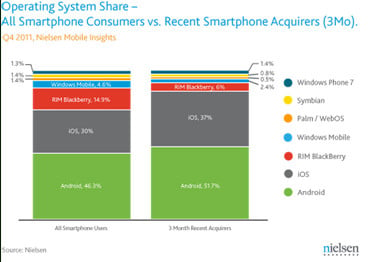 Certainly if you take the research, and associated press releases surrounding it, from Nielsen regarding smartphone sales then you might be forgiven for thinking that Android handsets are in danger of being overtaken by iPhones in terms of handsets in, well, hands. The NeilsenWire release in question doesn't help by loudly proclaiming "More US Consumers Choosing Smartphones as Apple Closes the Gap on Android" - a headline which has been copied by news media outlets pretty much word for word in many cases, although some have opted to leave the 'consumer' bit out, and a sentiment which has certainly been echoed as if Gospel in the vast majority of those news stories which I have bothered to read.
Certainly if you take the research, and associated press releases surrounding it, from Nielsen regarding smartphone sales then you might be forgiven for thinking that Android handsets are in danger of being overtaken by iPhones in terms of handsets in, well, hands. The NeilsenWire release in question doesn't help by loudly proclaiming "More US Consumers Choosing Smartphones as Apple Closes the Gap on Android" - a headline which has been copied by news media outlets pretty much word for word in many cases, although some have opted to leave the 'consumer' bit out, and a sentiment which has certainly been echoed as if Gospel in the vast majority of those news stories which I have bothered to read.
The Nielsen research points at the launch of the iPhone 4S in the back half of last year as the driver for this apparent 'surge' in Apple smartphone popularity, which is hardly surprising in my opinion. After all, just look at the media feeding frenzy whenever Apple throws any new product into the pool. The TV coverage bordered on the insane, especially considering that 'new' in the case of the 4S (which, I should point out before I get accused of Apple bashing, I own myself and am more than …
What's with the totally unrelated to anything title of the post?
{later}Ah I see, a failed attempt to spam - you succeeded in the networking forum sort of, but I've deleted that post and given you an infraction for it. Please read the rules if you really want to become a member of our community.
And with that, this sigspamfest of a thread is closed...
Sykipot is not a new Trojan Horse by any means, but the variation found to be attacking Department of Defense smart cards is certainly something that government agencies need to be worried about. United States government agencies, that is. It's doubtful the Chinese government will be too worried about them, considering that the Sykipot-led attacks against these US government agencies would appear to be originating from China itself.
 Security specialist AlienVault has uncovered evidence that the attacks might stretch right back as far as March 2011 and have been targeting a number of agencies which use ActivIdentity, or more specifically the smart card readers running ActivClient (the client application of ActivIdentity) and which smart cards are now standard security measures for the US Army, Navy, Air Force as well as the Department of Defense itself. The smart cards are used not only to identify military personnel but civilian employees and contractors for example.
Security specialist AlienVault has uncovered evidence that the attacks might stretch right back as far as March 2011 and have been targeting a number of agencies which use ActivIdentity, or more specifically the smart card readers running ActivClient (the client application of ActivIdentity) and which smart cards are now standard security measures for the US Army, Navy, Air Force as well as the Department of Defense itself. The smart cards are used not only to identify military personnel but civilian employees and contractors for example.
Jaime Blasco, AlienVault's Research Lab Manager, reckons this is the "first report of Sykipot being used to compromise smart cards" although he does admit that a year ago another security vendor wrote about smart card proxy attacks "although the report did not provide specifics on the attack methodologies being used, the term is useful in describing this latest style of attack vector." The research team have apparently so far found evidence of attacks compromising cards running on the Windows Native x509 software which is pretty commonplace, as I understand it, within …
If you are not getting your newsletter via email then yell in the general direction of Dani and she can look into it in case you have somehow fallen off the distribution list.
To quote one Ardav (whoever that may be) back in 2010 (http://www.daniweb.com/community-center/daniweb-community-feedback/threads/275655) the newsletter archive is available online thusly:
You gotta supply a year-month for the date parameter in the querystring:
e.g. http://www.daniweb.com/newsletter/issue.php?date=2010-05
@Ardav
The newsletters are still going out each month, complete with the Member of the Month interview/profile feature.
And how, exactly, would you suggest 'work the most' is measured? Time spent online, number of spammers banned, number of PMs read and replied to, yada yada yada.
Seriously, we've been down this road before with threads suggesting some kind of 'best mod' competition or vote and it always ends up the same way, concluding that it's not something that can be done in any meaningful way.
At the end of the day every single mod is an asset to DaniWeb whether they spend an hour a week here or many hours a day. They all devote as much time as they can, free of charge, to help keep the forums running smoothly.
As far as I am concerned they are all number one...
Man-in-the-Middle (MITM) attacks are, sadly, not news these days; they are a fact of online life. But word of how the latest SpyEye Trojan-driven MITM attacks are using clever post transaction fraud systems to effectively erase the evidence of the crime from the victims' view certainly deserve to be.
Attacking online bank accounts in both the US and UK, the attacks were first spotted just before the seasonal holidays took hold by researchers at Trusteer, a security company which works with banks to protect customers from just such threats as MITM attacks. What is a MITM attack exactly? Well, simply put, think of it as when a bad guy manages to intercept your online communication with the bank and sit in the middle, between you and your bank. You think you have logged into your online bank account but have actually logged into a fake version of that page which is operated by the 'man in the middle' who grabs your login information and while an automated process is telling you that your password and username didn't match and asks you to repeat the login the bad guy is logging into your real bank account and making a transfer. When he's done, you get dropped back at the real bank site for another login attempt which will, of course, now work.
These kinds of attack have one flaw, and that is how easy and quickly the victim can spot the fraud: if they view …
And while people are at it perhaps they could tell me how long this piece of string is? :)
Yep, currently on -4 rep so unable to impact on anyone else's rep as a result
Yes. But problem fixed now...
How will Microsoft differentiate Windows 8 in an already crowded Windows OS user space? How about, for one, with the use of a photographic gesture security system for logging in? The idea of using a photo to identify and authenticate the user is not without some pretty obvious problems (ambient lighting, bad hair day, forgetting to shave could all screw up your chances of using the computer that day) which is why Microsoft developers have thought outside of the box on this one.
 The important part of the 'photographic gesture security system' can be found in the gesture bit. Instead of using a photo of the user, the user instead chooses any photo they like and then selects parts of the image itself to use instead of a password. So, for example, you could tap on your face in a group photo, or draw a circle around the monkey in the top left corner of a wildlife image, or drag a line to connect two people in a photo. The gestures themselves act as your password, whether created using a touchscreen and your finger or a mouse it makes no difference: it is the act of tapping, drawing or dragging within a specific location of the screen that allows you access to the computer.
The important part of the 'photographic gesture security system' can be found in the gesture bit. Instead of using a photo of the user, the user instead chooses any photo they like and then selects parts of the image itself to use instead of a password. So, for example, you could tap on your face in a group photo, or draw a circle around the monkey in the top left corner of a wildlife image, or drag a line to connect two people in a photo. The gestures themselves act as your password, whether created using a touchscreen and your finger or a mouse it makes no difference: it is the act of tapping, drawing or dragging within a specific location of the screen that allows you access to the computer.
Now you may think that this is inherently insecure, after all the chances are that the bit of a group photo chosen to be the picture password will be the user him …
That would be very helpful indeed, but I suspect the amount of coding/tweaking to the already highly customized vBulletin implementation that DaniWeb runs upon would make it something we are unlikely to see implemented any time soon :(
And what has that got to do with ecommerce exactly?
There is some benefit to the spammers appearing in the activity lists though, namely that we catch some that otherwise might have slipped past unnoticed. Some fiddle with their profiles enough to make the list and the username itself arouses suspicion, others post spam in enough volume to make the list before they get flagged as such.
It's either a phishing scam (the old dating game one two - he/she sends photos of someone, builds a rapport, asks for money...) or a malware exercise where the photos are actually infected executables.
One thing is for sure, nothing good would come from it and DaniWeb bans all such scammers as soon as they are brought to our attention.
What he said :)
You might not have heard about Dirt Jumper yet, but the bad guys have. In fact, the high-risk and highly-effective DDoS toolkit is probably the most aggressive of the malware tools being employed by DDoS attackers at the moment, and the situation is set to get much worse very quickly as versions of Dirt Jumper are now appearing for sale at underground Web marketplaces for as little as $150 a time.
 Prolexic Technologies, which specialises in Distributed Denial of Service (DDoS) mitigation services, has today issued an in-depth threat advisory for Dirt Jumper together with a custom-developed scanning tool that can be used to detect Dirt Jumper command and control servers. Neal Quinn, vice president of operations at Prolexic, warns that his company is "seeing this tool used against clients worldwide and it is likely to become more widespread and effective as distribution spreads."
Prolexic Technologies, which specialises in Distributed Denial of Service (DDoS) mitigation services, has today issued an in-depth threat advisory for Dirt Jumper together with a custom-developed scanning tool that can be used to detect Dirt Jumper command and control servers. Neal Quinn, vice president of operations at Prolexic, warns that his company is "seeing this tool used against clients worldwide and it is likely to become more widespread and effective as distribution spreads."
The Prolexic Security Engineering and Response Team (PLXSERT) has certified the toolkit as a high-risk threat following extensive analysis of Dirt Jumper v3. The newest variant, Dirt Jumper September, which comes with an enhanced control panel making it even easier for attackers to use, has been painstakingly analysed and the threat advisory itself includes full details of the payload as well as a detailed breakdown of attack signatures by attack type.
Most interestingly though, PLXSERT has developed a custom tool to scan for suspected HTTP command and control servers utilizing Dirt Jumper strains. Dirt Dozer is being released as a free …
Why should anyone here do your homework for you?
Show us what you have already done (including the code you have so far) and where you are getting stuck, then people will be more inclined to take you seriously and offer their time to help you out.
Oh and read the rules, especially this one: "Do provide evidence of having done some work yourself if posting questions from school or work assignments"
Link deleted
Username now changed...
Tell us what you want to change it (provide a couple of alternatives in case your preferred name is already taken) and myself or Narue will change it for you when we get a few spare minutes from killing spammers.
Done
It's the festive season but would you really expect Lady Gaga to give you a free iPad 2? That was the exact message being broadcast from Lady Gaga's Twitter account earlier, promising each and every one of her 17 million followers an iPad 2 and all they had to do was click the link for details.
 Of course, there was no iPad. The Lady Gaga Twitter account had been hacked and if you clicked on that link it would take you to a number of different sites via redirects and then dump you at a survey designed to scam you out of valuable personal information. Equally 'of course' as soon as the tweet appeared it was retweeted by thousands of innocent fans keen to spread the apparent good news, meaning the scope of this particular scam is truly epic. Even though the first link in the chain has now been suspended by Bit.ly for being suspicious, the chances are that other links will be out there and still live so don't be sucked into the scam yourself. Even at this time of year, especially at this time of year, there's no such thing as a free iPad.
Of course, there was no iPad. The Lady Gaga Twitter account had been hacked and if you clicked on that link it would take you to a number of different sites via redirects and then dump you at a survey designed to scam you out of valuable personal information. Equally 'of course' as soon as the tweet appeared it was retweeted by thousands of innocent fans keen to spread the apparent good news, meaning the scope of this particular scam is truly epic. Even though the first link in the chain has now been suspended by Bit.ly for being suspicious, the chances are that other links will be out there and still live so don't be sucked into the scam yourself. Even at this time of year, especially at this time of year, there's no such thing as a free iPad.
Lady Gaga was quick to acknowledge the attack and inform her fans "the hacking is over" but the damage has already been done and many will now be wondering if they can trust the Lady Gaga Twitter feed at all.
If that wasn't bad enough, another Free iPad 2 …
Preempted that now and edited name... :)
The original [post was NEARLY TWO YEARS AGO so I imagine he's sold it. THREAD CLOSED!
Sorry, DaniWeb does not deleted threads (old or new) which are not in breach of the rules.
Of late, and in regards to the spammers specifically, updating profile (changing signatures etc) seems to account for much of the activity - especially when the account has been banned from posting.
You might think that there's not much further for a high-end low budget home entertainment remote control unit to go than the One For All SmartControl that DaniWeb reviewed just over a year ago now. However, One For All does not seem to agree as it has just launched the SmartControl Motion in the UK in time for Xmas, complete with the iPhone inspired gesture controls which provide the difference as well as the 'motion' in the name of the device.
 Although the SmartControl Motion we have been playing with did not come with the Sony PS3 adapter that allowed the previously reviewed gizmo to control your PlayStation as well along with the rest of your home entertainment kit, the truth is that the two remote controls are essentially the same. So they both have the same 'smart' learning facility which makes programming the thing for your TV, DVD or Blu-ray player, stereo, set top box and the like a doddle for a start. In fact, the SmartControl Motion was a real delight in this regard, taking the concept even further than before to become a very refined process involving nothing more than pressing a learn button and a single digit for all but the most obscure of electronics brands. Once the remote has been programmed for use with your personal selection of home entertainment kit, it functions the same as before.
Although the SmartControl Motion we have been playing with did not come with the Sony PS3 adapter that allowed the previously reviewed gizmo to control your PlayStation as well along with the rest of your home entertainment kit, the truth is that the two remote controls are essentially the same. So they both have the same 'smart' learning facility which makes programming the thing for your TV, DVD or Blu-ray player, stereo, set top box and the like a doddle for a start. In fact, the SmartControl Motion was a real delight in this regard, taking the concept even further than before to become a very refined process involving nothing more than pressing a learn button and a single digit for all but the most obscure of electronics brands. Once the remote has been programmed for use with your personal selection of home entertainment kit, it functions the same as before.
This does mean that while the One For All title is pretty …
The sound of spammers dying in my head
With the recent announcement of an easy way to gain root access for Android phones running 2.3.4, to add to the list of similar exploits for earlier versions and 3.0 and beyond, it should come as no real surprise that the bad guys are taking advantage of the relative weakness of the Android OS when compared to iOS devices.
 According to the latest FortiGuard Labs report looking at the top five Android Malware Families, there are approximately five times the number of malicious families on the Android OS as compared Apple's iOS. Of course, some of this will be down to market share considerations as Android devices now accounts for 52.2% of global smartphone OS market share whereas iOS on 18% is in third place behind Symbian.
According to the latest FortiGuard Labs report looking at the top five Android Malware Families, there are approximately five times the number of malicious families on the Android OS as compared Apple's iOS. Of course, some of this will be down to market share considerations as Android devices now accounts for 52.2% of global smartphone OS market share whereas iOS on 18% is in third place behind Symbian.
But it does not account for the sheer scale of the Android malware explosion which, according to Axelle Apvrille who is a senior mobile anti-virus researcher at Fortinet, can be attributed to "the way Apple handles iOS application development and distribution. Unlike Android, which makes it fairly easy to place applications for people to download, iOS requires developers to undergo some strict screening from Apple before the application can make it to the Apple Store. That's not to say that Apple is totally immune from being infiltrated by malware - the Eeki banking worm proves that - but it is a testament to why we're seeing so little activity on the iOS platform".
Comparing 2011 to 2010, …