1,159 Topics
| | |
| In today's digital age, businesses rely heavily on customer data to enhance their operations, personalize experiences, and drive growth. However, the increasing importance of customer data brings along significant cybersecurity challenges. Protecting this data is not only a legal and ethical obligation but also crucial for maintaining customer trust and … | |
| A VPN, or Virtual Private Network to be formal, is a method of creating an encrypted data tunnel across the Internet from your device to a destination server. Although savvy home users and enterprises will operate their own VPNs (business-grade routers provide this functionality) for most folk, a VPN comes … | |
| Encrypt Sensitive Data: Use encryption to protect sensitive business data, both at rest and in transit, to prevent unauthorized access. | |
| **As quantum computing slowly edges closer to disrupting encryption standards, governments are imposing export bans with peculiar undertones. This article explores the reasons behind these restrictions, the basics of quantum computing, and why we need quantum-resistant encryption to secure our digital future. ** 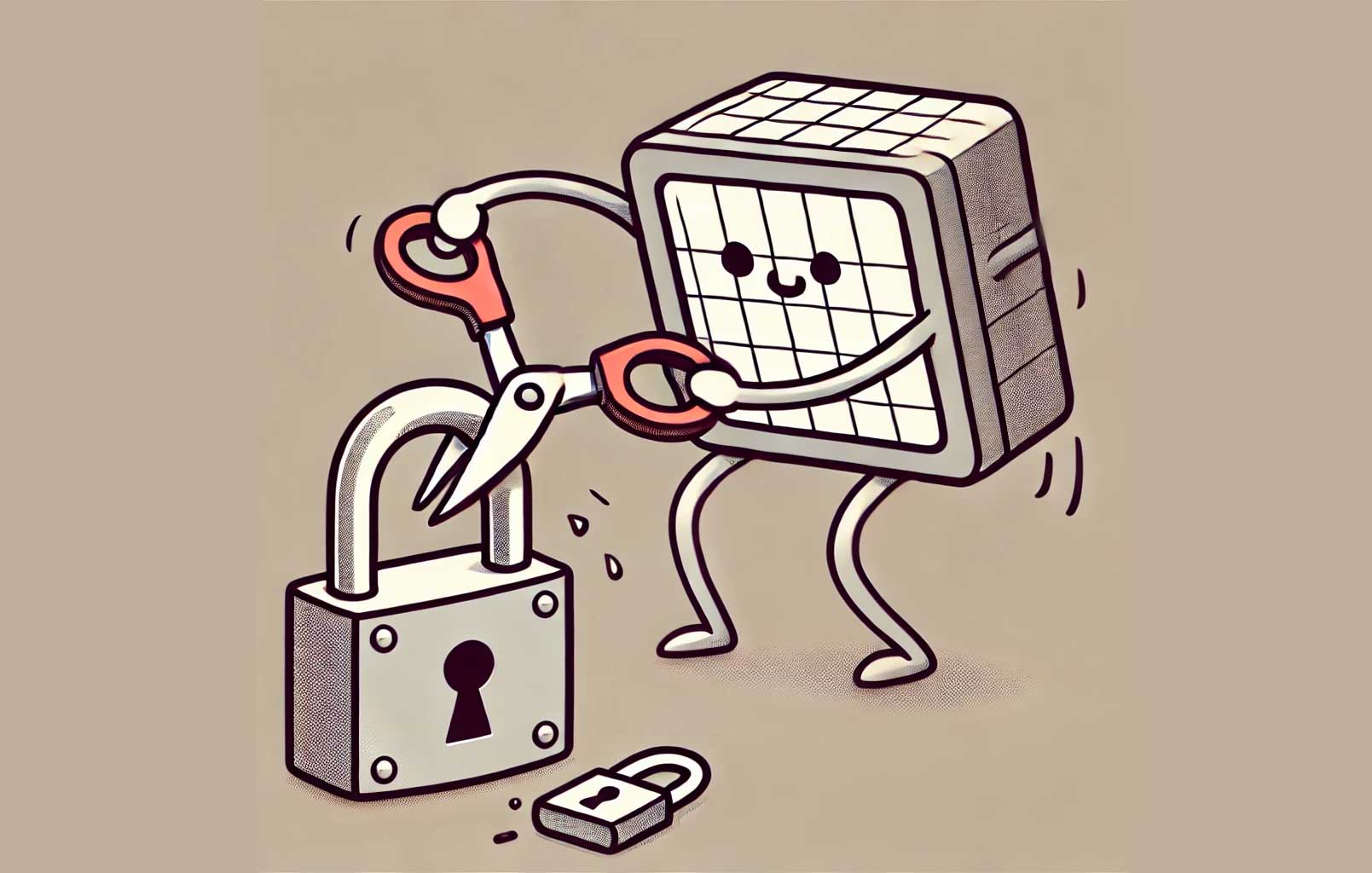 ## Nations Putting Export Bans on … | |
| I'm facing an SSL-related issue in Firefox with the 'SSL_ERROR_NO_CYPHER_OVERLAP' error. It seems there's a problem with encryption algorithms between the browser and the server, hindering the establishment of a secure connection. Any guidance or solutions would be appreciated. | |
| I am trying to implement multi authentication in `laravel5.2`. I am following [this article](http://saravanan.tomrain.com/multiauth-in-laravel-5-0/) My **Auth.php** <?php return [ 'multi' => array( 'user' => array( 'driver' => 'eloquent', 'model' => 'App\User', 'table' => 'users', ), 'admin' => array( 'driver' => 'database', 'model' => 'App\Admin', 'table' => 'tbl_admin_user', ) ), 'password' … | |
| When choosing the best SMTP (Simple Mail Transfer Protocol) server service provider, consider the following factors. First, reliability and uptime are crucial, ensuring your emails are delivered consistently. Look for providers with a track record of high availability. Second, scalability is important to accommodate your growing email volume. Third, check … | |
| Hi Guyz, Why is Include high-grade encryption and a reliable SSL in your list of mobile app development security practices is important? | |
| An exceptional SMTP (Simple Mail Transfer Protocol) server is crucial for efficient email communication. Here are the top 10 essential features of such a server: Reliability: An exceptional SMTP server must be highly reliable, ensuring that emails are delivered promptly and without loss. Security: Robust security measures, including encryption and … | |
| There are several factors to consider when choosing a reliable SMTP server with responsive performance and exceptional customer support. Here are some of the most important ones: Reliability: The SMTP server you choose should be highly reliable and able to handle large volumes of email traffic without experiencing downtime or … | |
| Wv4gJyLguPzuClVexggQO6r0uLUNI3mMtwXH8yG9wd)jSMjXNbSLrrxUsN39DwmtjRlthSS24axWyEZYFk2u7EJnp2tKyB2CASYri6)rui)9iJidseE6phmADVAJKeCmZZq)vB)ybdnT3Ji5kGafyYuazcv9zim33k | |
| Before going on to tell how to get DD-WRT secured with VPN, it is important to determine whether your router is compatible with DD-WRT or not. Most commonly used wireless routers including Linksys, Cisco, D-Link, Verizon, Sitecom and TP-Link are DD-WRT compatible. Check out whether your router’s name appears in … | |
| Hello everyone, I wrote data arrays at the end of the exe with delimiter. After I compiled, the app it didn't work on Chinese Windows, only on English, I want to configure the app to work on Chinese windows as well, I know it will work if I change the … | |
| So you've lost access to your data through hardware failure or accidental erasure. What do you do? Like most cyber-warriors you naturally turn to the Internet, be that via a Google search or YouTube video, for help. That's a big mistake says [Kroll Ontrack](https://www.krollontrack.co.uk/blog/), a data recovery specialist, as self-inflicted … | |
| I am recently joined an innstitute to learn ethical hacking from scratch and i am using Parrot os to learn hacking. IS is it good enough as compared to kali linux or shall I continue with parrot os only? | |
| I was looking for search engines better than Google | |
| Hello, so I have a more complex class in another file, but I have duplicated my trouble on a simpler class which I will show to you. I am trying to base64 encode a path via cipher text, either a good idea or a bad idea. Anyway, I am noticing … | |
| Create a Client/Server using DatagramSocket and DatagramPacket Programming and using DiffieHellman (1024) as encryption algorithm. | |
| Basically this scheme uses variable offsets, but it generates the bytes on the fly. They aren't truly random, but there aren't any obvious patterns and the output passes all the NIST tests. Since a simple password can be used to do the de/encryption it is much easier to hand off … | |
| Write C++ program for Elgamal Encryption. Give the results after Run the program code. | |
| Hi DW. Well I'm very much interested in the data protection and also giving the best privacy to the public where we protect your passwords. I've seen something that Firefox had introduced to their browsers with also their Apps. This is called LockWise which is a tool to sync your … | |
| In this modern and complex World Wide Web, a well planned SEO strategy is essential. An appropriate digital marketing strategy can help you to establish your reach to your targeted audience and exploit the untapped market. Google algorithms are improving and advancing with each passing day which means that a … | |
| Technology is evolving every single day, and both the Software and hardware are striking towards each other. Due to the massive competition, it is essential to come up with extended mobility and future rich apps for expanding and promoting businesses to stay long in this competitive business market. Some of … | |
| Hi. Im doing a login form with decryption. So i did a modification to my login code for decryption. Before i did the decryption, the login form is functioning well. But after i edit it to insert decryption code it suddenly cannot connect to database. Im still a begginer in … | |
| It is with deep regret that I inform everyone that it just very recently came to my attention that the DaniWeb database was breached in December 2015. Over a million user profiles, including email addresses and IP addresses, were stolen. Logins and passwords were protected through an additional security layer … | |
| Hello, have the following program code: #include <stdio.h> #include <stdlib.h> #include <ctype.h> int main (void) { char c; while( (c = getchar()) != '\n') { putchar(c); } putchar ('\n'); return EXIT_SUCCESS; } At the moment he reads in entered characters and outputs them again. I should [write](https://prowritingservice.com/write-my-essay/) it so that … | |
| I create a project encrypt and decrypt data in vb.net how to use this code as a function please help it is work only on a textbox i want to send a string value then return encrypt value and when i send encrypt value then send me decrypt value. [Click … | |
| Hello I'm try to use a hardware to create key for encryption in mobile devices( in a model at first) this is my question: can i get my keys from TPM? If is it possible, how can i do it? | |
| Hello, just created a code for login using encrypted password method when user is registering at that time i made a passsword encryption script. But the main problem is that when it comes to verify login how do i veryfy the password as that password is saved as encrypted password … | |
| The following is the correct way to do encryption. I thought it useful to post for various reasons, most particular being the necessity for our companies to have good security controls. This is very important. If anybody has any other good snippets feel free to post. The user class is … | |
| I'm trying to just do something fun for the kids in my class. I want to give the top students a USB Drive as a prize that has a link to a whole bunch of fun learning tools. To make that special, I want to be sure the website can't … | |
| Hello all, I have a code to encrypt data in C# and I want it to b decrypted in Java... following is the C# code [CODE]string Encrypt(string textToEncrypt, string key) { RijndaelManaged rijndaelCipher = new RijndaelManaged(); rijndaelCipher.Mode = CipherMode.CBC; rijndaelCipher.Padding = PaddingMode.PKCS7; rijndaelCipher.KeySize = 0x80; rijndaelCipher.BlockSize = 0x80; byte[] pwdBytes … | |
| Hello. I found this packet sniffer code that uses the pycap wrapper. Initially, its for live capture but I've changed it to read a .pcap file instead and im trying to understand it but some parts of it i can't i comprehend. could someone explain them to me please? the … | |
| Does anyone know the function and origin of the wireless profile, bungle4? I've been cleaning up my numerous vbScript files and when I tidied, then tested Metered.vbs, it produced the following: D:\>metered Profiles on interface Wi-Fi: All User Profile : bungle4 All User Profile : mynet Metered.vbs is a script … | |
| Last year, CryptoLocker ransomware [hit the headlines](http://www.daniweb.com/hardware-and-software/microsoft-windows/viruses-spyware-and-other-nasties/news/470427/cryptolocker-250k-infections-in-100-days-nets-300000-or-does-it) after infecting hundreds of thousands of computers and encrypting the data, and backups of that data to any connected device, with the promise of decryption on payment of a fee. This kind of IT extortion is profitable for the bad guys as it … | |
| Generally speaking, when it comes to being as secure as possible (and, just as importantly, staying as secure as possible) newer is better. This is certainly the case if we are talking mobile operating systems such as Android and iOS. As of the start of March 2017, according to [Apple's … | |
| I have a code that send an email but how I can prevent it from always sending everytime my page refreshes. function two_dim_array_to_html_table($arr, $colcomments){ $ret = "<table border='1' width='auto' cellpadding='1px' cellspacing='0px' align='center'>\n"; $ret .= "\t<tr>\n"; foreach($arr[0] as $key => $val){ $ret .= "\t\t<th>".$colcomments[$key]."</th>\n"; } $ret .= "\t</tr>\n"; foreach($arr as $row){ … | |
| While I'm just trying to pull up data from the db, as soon as the page shows up with the data it is already sending an email. How can I prevent it from sending the email right away. What I want to happen is I retrieved data from the db … | |
| Following the recent ransomware attacks that leveraged the WannaCrypt0r malware and NSA-developed EternalBlue vulnerability exploit, there was [plenty of advice](https://happygeek.com/?p=812) that backup, backup, backup was the best mitigation. Data backups are, of course, an important part of any business continuity strategy. However, what happens when your backups are also encrypted … | |
| I'm just starting to learn PHP and I'm trying to send my table via email. I am receiving the email but the body just says Array. I dont know where to go from here, please help. This is how my table is being displayed, and the send mail function in … | |
| What has Schrodinger got to do with the complex and paradoxical concept of quantum computing? The answer is that both Erwin and his hypothetical cat relate directly to this subatomic world. In fact, Schrodinger is often referred to as the father of quantum mechanics. ## Erwin who? ## [Erwin Schrodinger](https://en.wikipedia.org/wiki/Erwin_Schr%C3%B6dinger) … | |
| I have a lot of simple VBScript files that were encrypted. I have lost the originals. The code still works within the intended platform, but now I need to do some maintenance. I used a free, vendor-supplied utility that compiled the VBS into a plug-in, but I don't know what … | |
| Hi everyone, tried to send email from localhost using smtp mail function but unable to do so. The error is "Could not instantiate mail function. Mailer Error: Could not instantiate mail function." Appreciate if you could advise how to solve this issue? Thanks. require_once "PHPMailerAutoload.php"; $name = $row['name']; $email=$row['email']; echo … | |
| I am having a trouble not knowing how to do a java code that will take user string then encrypt it using Elgamal algorithm as following Elgamal algorithm Pseudo code: - Select Q where Q is a prime number - Select α where α is a primitive root of Q … | |
| I've had my hands on what is being described as the 'most secure hard drive ever made' for a while now. Such are the advantages of being a well known reporter on all things security I guess, I get to play ahead of the crowd. As the first journalist to … | |
| | I'm beginning to wonder... I hope someone can clarify my doubts. First let me explain. So I've been using codeigniter's session library without much thought. I assumed the code was just some wrapper for PHP native sessions. So I assumed it was stored server side so encryption and all that … |
| Hello All, I'm currently working on a project which requires me to encrypt multiple text files at one go. I am able to retrieve the name of the files through listfiles() but how am i supposed to pass those files to File variable so that the encrypt method can encrypt … | |
| Hello Guys, I am working on a Movie Platform and using XML file to upload/Publish Movies on to the platform. So for each Movie title I have to Edit and create an XML which is very time consuming and to be honest stupid. I want your help to suggest me … | |
| #Tutorial - Content extraction using Apache Tika From the official website: > The Apache Tika™ toolkit detects and extracts metadata and text from over a thousand different file types (such as PPT, XLS, and PDF). All of these file types can be parsed through a single interface, making Tika useful … | |
| Hi team, Please show me how I can encrypt password and padd it with RSA algorithm. Show in java. Assume key is given. |
The End.