Research published today by data governance software developer Varonis reveals that, when it comes to the virtualized environment, security awareness appears to be something of a black hole.
The study found that data security in these virtualized environments can all too often be totally neglected, and some 48% of IT organisations reported or suspected there had been unauthorised access to files kept on virtual servers. The findings suggest that when it comes to awareness of security matters regarding virtualized servers and the data stored upon them, the harsh truth of the matter is that there is very little. Indeed, the survey found that 70% of those questioned had 'little or no' auditing in place for example.
When you consider that Gartner reckons there are now in excess of 50 million Virtual Machines installed on servers, it should come as no surprise to discover that 87% of respondents to the Varonis study said their application servers were already virtualized. The reasons for this virtualization being mainly a combination of deployment speed (76%) and disaster recovery potential (74%). Yet file security appears to be neglected almost across the board.
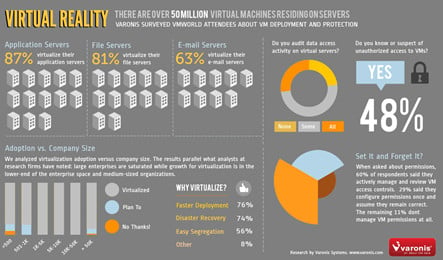
Sure, nearly 60% did claim to be "very careful about setting permissions and controlling subsequent updates" there's no escaping from the fact that 70% had implemented little or no auditing regardless of the company size. A statistic made all the more surprising by the revelation that in enterprises of more than 5,000 employees some 20% admitted …
 The
The  At a round-table discussion, hosted by cloud provider UKFast, Sam Allcock, CEO of Custard Media, stated that the key to successful audience growth was traffic stream diversification rather than a reliance upon Google-led SEO strategies. "Businesses must investigate every alternative method of traffic, including Facebook and Twitter. It just so happens now the easiest way to attract traffic is through Google but will this be the case in five years?” Allcock said.
At a round-table discussion, hosted by cloud provider UKFast, Sam Allcock, CEO of Custard Media, stated that the key to successful audience growth was traffic stream diversification rather than a reliance upon Google-led SEO strategies. "Businesses must investigate every alternative method of traffic, including Facebook and Twitter. It just so happens now the easiest way to attract traffic is through Google but will this be the case in five years?” Allcock said. AlienVault's Head of Labs, Jaime Blasco, reproduced the latest exploit in a previously fully patched Java installation and found that the exploit was probably "bypassing certain security checks tricking the permissions of certain Java classes as we saw in CVE-2012-4681". In fact, according to Blasco, the exploit is the "same as the zero day vulnerabilities we have been seeing in the past year in IE, Java and Flash".
AlienVault's Head of Labs, Jaime Blasco, reproduced the latest exploit in a previously fully patched Java installation and found that the exploit was probably "bypassing certain security checks tricking the permissions of certain Java classes as we saw in CVE-2012-4681". In fact, according to Blasco, the exploit is the "same as the zero day vulnerabilities we have been seeing in the past year in IE, Java and Flash". It's also more than just a collection of lists though, the 2013 edition has a number of really rather well presented and very in-depth feature spreads covering games such as Call of Duty, Grand Theft Auto and Forza. There are even some more unexpected features like the one that looks at the relationship between the mediums of comic books and gaming, or another that delves into the top 50 videogame villains of all time.
It's also more than just a collection of lists though, the 2013 edition has a number of really rather well presented and very in-depth feature spreads covering games such as Call of Duty, Grand Theft Auto and Forza. There are even some more unexpected features like the one that looks at the relationship between the mediums of comic books and gaming, or another that delves into the top 50 videogame villains of all time.

 Brian Tokuyoshi from Palo Alto Networks predicts that social media, data decryption and virtualised network security will be high on the agenda in the year to come.
Brian Tokuyoshi from Palo Alto Networks predicts that social media, data decryption and virtualised network security will be high on the agenda in the year to come.