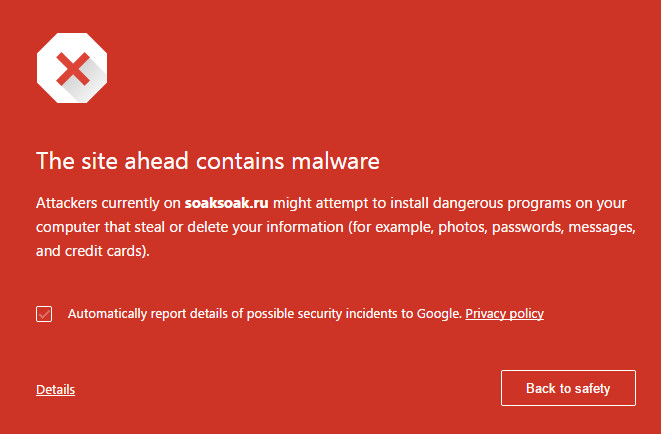
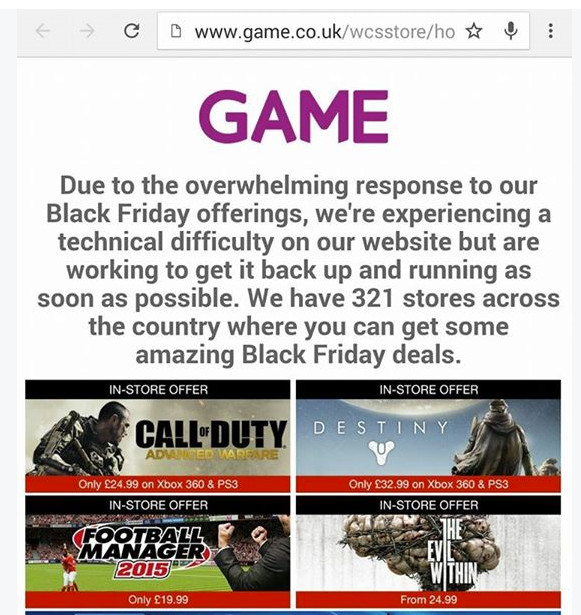
I'm seeing 'Nearly a Posting Maven' here.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Dani commented: Feel better :) +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
ChrisHunter commented: I think it and you post it! +7
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Stuugie commented: Interesting and thanks for sharing. +6
stultuske commented: yup :) +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster