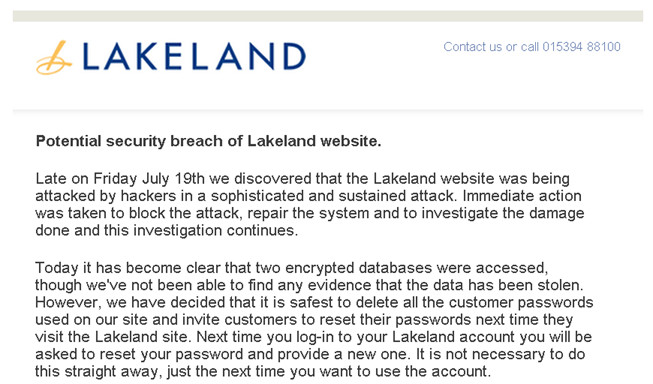
A successful tournament poker player from Japan, with earnings estimated at $1.5 million from his prowess at bluffing and holding his nerve under pressure, has been arrested and charged with being behind an Android malware distribution operation that netted even more: $3.9 million according to Symantec.
The Chiba Prefectural Police in Japan arrested a total of nine people in connection with distributing spam emails with download links to the Android.Enesoluty malware. Symantec reports that one of these was 50 year old Masaaki Kagawa, president of an IT firm from Shibuya, Tokyo. "His passion for taking chances and risks has paid off in the game of Poker" says Symantec employee Joji Hamada, who continues "but it’s not looking good for his gambling with Android malware."
It would appear that the Android malware operation was running between September 2012 and April 2013, with some 150 domains registered to the malicious apps which managed to collect more than 37 million email addresses from over 800,000 Android devices. This address list was then used to spam people in order to lure them to a fake online dating service, which in turn was where the profits of 390 million Yen are thought to have been made.

 Reports are emerging that conmen claiming to represent 'The Start-ups Loan Company' amongst other loan providers, are scamming people out of their Ukash codes. “The official Start-Up Loans Company is a government backed organisation and is not associated with providing loans to individuals, but is one of the names criminals are using to conduct this scam,” warns Miranda McLean, a director of Ukash. “The criminals have access to personal information provided to loan broker websites and claim to have approved a loan, but need a fee to be paid in advance."
Reports are emerging that conmen claiming to represent 'The Start-ups Loan Company' amongst other loan providers, are scamming people out of their Ukash codes. “The official Start-Up Loans Company is a government backed organisation and is not associated with providing loans to individuals, but is one of the names criminals are using to conduct this scam,” warns Miranda McLean, a director of Ukash. “The criminals have access to personal information provided to loan broker websites and claim to have approved a loan, but need a fee to be paid in advance."



 However, as a more eco-friendly alternative to traditional portable battery backups the SolarBank ticks all the right boxes except one for me. So I'll start with the one that remains un-ticked: price. At £32.99 this is not a cheap way of ensuring your iPhone never runs out of juice. Especially when you look at the marketplace out there dealing in …
However, as a more eco-friendly alternative to traditional portable battery backups the SolarBank ticks all the right boxes except one for me. So I'll start with the one that remains un-ticked: price. At £32.99 this is not a cheap way of ensuring your iPhone never runs out of juice. Especially when you look at the marketplace out there dealing in …