happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Ketsuekiame commented: Damn that 70mph limit! :) +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
nitin1 commented: yoo!! you must be here so early. you are very strict!! your words are always nice, respectable. i will not be here more on this thread.. thanks :-) +0
diafol commented: Good wrap-up +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Octet commented: A very informative, and interesting post! +4
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
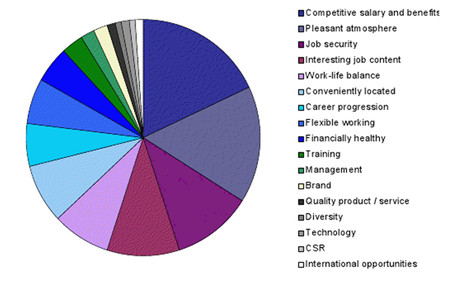
gulzaifaqeeri commented: The Power of Soft Skills: How They Can Boost Your Job Search +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
ChrisHunter commented: Viewed this purly for the name, amazing! +7
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
<M/> commented: bum bum bum! +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
aVar++ commented: Very interesting. +2
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
<M/> commented: it does... doesn't it :D +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster




 However, as a more eco-friendly alternative to traditional portable battery backups the SolarBank ticks all the right boxes except one for me. So I'll start with the one that remains un-ticked: price. At £32.99 this is not a cheap way of ensuring your iPhone never runs out of juice. Especially when you look at the marketplace out there dealing in …
However, as a more eco-friendly alternative to traditional portable battery backups the SolarBank ticks all the right boxes except one for me. So I'll start with the one that remains un-ticked: price. At £32.99 this is not a cheap way of ensuring your iPhone never runs out of juice. Especially when you look at the marketplace out there dealing in …

 While anything that makes search better for the user has to be a good thing generally speaking, when you get down to the specifics of Panda there has been a lot of collateral damage to sites such as DaniWeb. There's not a lot of point covering old ground here in too much detail, save to say that a couple of years ago DaniWeb founder and CEO Dani Horowitz became something of a poster girl for the SEO world when she managed to
While anything that makes search better for the user has to be a good thing generally speaking, when you get down to the specifics of Panda there has been a lot of collateral damage to sites such as DaniWeb. There's not a lot of point covering old ground here in too much detail, save to say that a couple of years ago DaniWeb founder and CEO Dani Horowitz became something of a poster girl for the SEO world when she managed to 



 On the afternoon of 8th May, a game spokesperson revealed that "the current Battlefield 3 outages are a result of activity that appears to be aimed at overwhelming our back-end infrastructure. We are working on a variety of solutions to address this problem and are focused on resolution as quickly as possible... We are incredibly disappointed by these activities and the impact they are having on all of our ability to enjoy BF3, thank you for your patience as we work to resolve these issues."
On the afternoon of 8th May, a game spokesperson revealed that "the current Battlefield 3 outages are a result of activity that appears to be aimed at overwhelming our back-end infrastructure. We are working on a variety of solutions to address this problem and are focused on resolution as quickly as possible... We are incredibly disappointed by these activities and the impact they are having on all of our ability to enjoy BF3, thank you for your patience as we work to resolve these issues." Collecting nearly a decade's worth of quotations from Zuckerberg's speeches, interviews and writings on subjects including online social engagement, education, hacking culture, personal business strategies and even his views on that movie, this book is a triumph of the editor's art. I say that as a writer and editor, in the technology sector, with two decades of graft behind me. …
Collecting nearly a decade's worth of quotations from Zuckerberg's speeches, interviews and writings on subjects including online social engagement, education, hacking culture, personal business strategies and even his views on that movie, this book is a triumph of the editor's art. I say that as a writer and editor, in the technology sector, with two decades of graft behind me. …

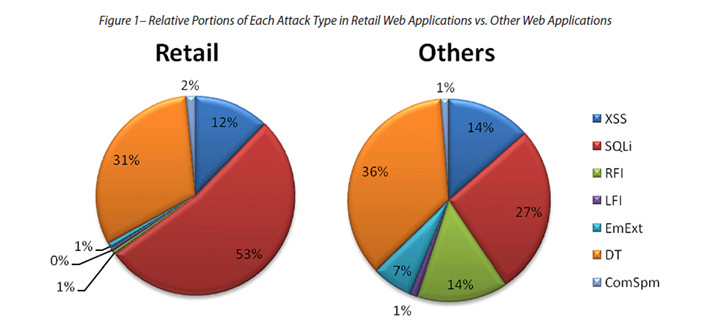
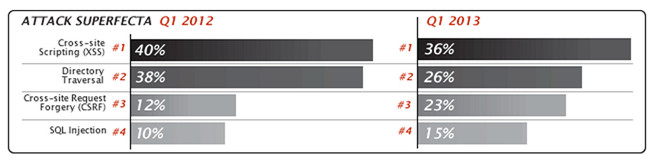 The volume of Cross-Site Request Forgery (CSRF) attacks was up by an astonishing 132% by the end of the quarter, compared to the same period during …
The volume of Cross-Site Request Forgery (CSRF) attacks was up by an astonishing 132% by the end of the quarter, compared to the same period during …