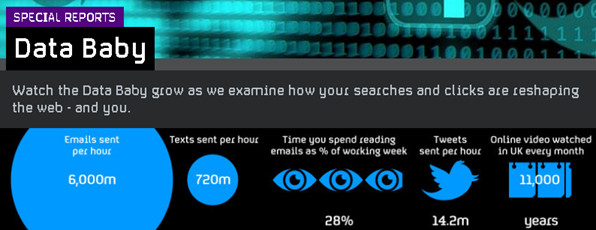
Discount coupons are OK, but consumers consider drive-by location marketing an invasion of privacy. That's the warning message that research across four countries (US, UK, Mexico and India) by ISACA would appear to be flagging loud and clear to retailers wanting to maximise the marketing potential of customers with smartphones.

ISACA, which specialises in helping business get the most value while managing risk related to information and technology, asked more than 4,000 consumers about their holiday season shopping habits and their opinions on privacy. This revealed that shoppers in India and the UK were the most resistant to location-based marketing on smartphones, with more than 70% declaring tactics such as sending unrequested special offer messages when they walk past the store concerned would be considered invasive.
The 2013 ISACA IT Risk/Reward Barometer suggests that receiving a text message from a store as they walk by is almost as invasive for people as if they were to go inside and be greeted by name by the clerk despite never having met them before. In the UK, 69% of consumers said they would, however, be happy to be sent a discount coupon on their mobile device. Indeed, across all four countries surveyed people were generally more receptive to the idea of targeted discount codes by text rather than special offers arriving as they walk by that may not be relevant to them.
Mexicans were the most welcoming to the location-based SMS marketing, with more than …