I'm not saying it is true, but...
Ah, enough said. File under conspiracy theory nutjobs.
I'm not saying it is true, but...
Ah, enough said. File under conspiracy theory nutjobs.
Comment from Dave Larson, CTO at Corero Network Security:
These types of frequent and sub-saturating DDoS attacks are typically intended to distract corporate security teams, but leave enough bandwidth available for a subsequent attack to infiltrate the victim’s network, much like the incident reported against Carphone Warehouse. This technique of DDoS as a smokescreen is becoming a more commonplace threat, especially for any Internet connected business that is housing sensitive data, such as credit card details, or other personally identifiable information. Organizations need to arm themselves with real-time DDoS protection at their Internet edge, or work to ensure that their upstream providers are offering them more sophisticated DDoS mitigation services to eliminate this challenge. Traditional approaches to DDoS defense, cannot and will not catch these sophisticated and malicious attacks.
Comment from Tim Erlin, Director of Security and Product Management at Tripwire:
Unlike some of the other retail breaches of late, this one was discovered internally by Carphone Warehouse, and disclosed publically only a few days after discovery. That’s an improvement over breaches that were discovered through credit card fraud and kept undisclosed for longer periods of time.It appears that 90,000 of the 2.4 million affected customers may have had their credit card data accessed, though it was encrypted. The limited number of credit cards affected should also limit the impact of the breach itself.
Cooment from David Emm, Principal Security Researcher at Kaspersky Lab:
The recent cyber-attack on Carphone Warehouse highlights the importance of online security for both organisations and consumers. Companies holding consumer data have a responsibility to keep it safe, and make sure it doesn’t fall into the wrong hands. The fact that 2.4 million people’s personal details have been compromised will undoubtedly be a huge cause of concern for customers; and it’s hardly surprising that many have publicly expressed their dismay at the fact that it took Carphone Warehouse so long to notify them of the breach. Presumably it took Carphone Warehouse time to quantify the extent of the breach and assess its impact before taking steps to notify customers. Carphone Warehouse has said that it has contacted all those affected. However, I would recommend that all Carphone Warehouse customers take the opportunity to change their passwords - including changing them on any other sites where they have used the same password (it’s never a good idea to re-use the same password across multiple accounts). They should also be cautious about any e-mails they receive. The hackers behind the attack may already have been able to formulate phishing emails, so consumers must think carefully about whether the emails they receive are legitimate. I would caution against clicking links in e-mails – it’s always better to type the website address manually, to avoid the risk of being redirected to a phishing site. Finally, they should keep a close check on bank …
Comment from Luke Brown at Digital Guardian:
2.4 million is a big number. When this is how many customers have been affected by a data breach, you’ve got to take a good hard look at existing security measures and question if they are even remotely adequate for the task at hand. Carphone Warehouse claims 'only' 90,000 sets of credit card details were accessed. But while a credit card can be cancelled (at much inconvenience to the cardholders affected), it’s a lot more difficult to change a name, address or date of birth. Sadly this is the issue facing the full 2.4 million customers whose personal details are now in the hands of criminals likely to use this information for phishing and fraudulent activities. With the implementation of the General Data Protection Regulation on the horizon and potentially ruinous fines levied against this kind of breach in the near future, businesses need to wake up to the fact that a more date-centric approach to security is the only way to effectively protect against this kind of breach in the future. The days of perimeter based security are numbered and with trust being the most important factor in any customer/business relationship, why wait until it has been irreparably damaged before switching to a data security protocol that is able to protect against the security threats of today, not yesterday.
Comment from Mark James, Security Specialist at IT Security Firm ESET:
Data from this breach may well be used in an attempt to directly log into other financially related systems as some people still fail to have unique passwords for different online accounts. This data may also be used in targeted phishing attacks to get more useful data that could also be used for identify theft or other malicious purposes. We all know how to handle that random caller or email that tries to scam us with a half-hearted attempt at gaining our trust but if they are armed with some kind of information that is true along with some knowledge of our explicit data ( names, addresses) that trust could be the stepping stone to a successful scam being completed. Almost certainly data will be circulated and used elsewhere for ongoing spam or malware campaigns, all data has a value and we need to understand that any information can be used for malicious reasons. Customers should be vigilant against people calling or emailing with sporadic bits of information in an attempt to gain more data. Change your passwords NOW, also remember that you can use different bits of information when filling out forms or applying for web page access. You don’t need to tell the truth about your favourite colour or your first dog’s name. Speak to your bank or financial organisation so they are aware and if still concerned sign up for a reputable credit checking organisation …
Comment from Amichai Shulman, CTO of Imperva:
I think that this is a good example of how media and “normal” people sometimes overlook what attackers are extremely fast to understand. How can someone even bother to mention 90,000 credit card numbers (which seem to be encrypted) when 2.4 Million records, that include bank account numbers as well as personal details, have been stolen. Credit card numbers are replaced in a jiffy. Bank accounts are a mess to replace and no one would change their phone number or address as a consequence of a breach. So basically attackers now have “immutable” information about millions of individuals. This is something to worry about.
Comment from Philip Lieberman, CEO of Lieberman Software:
This is an excellent example of where the CEO of the company now needs to step in and evaluate whether his leadership of his information technology department yielded what he and his board of directors view as an acceptable loss. The CEO’s role today must be as the commander-and-chief of cyber-defense, rather than simply complying with the minimal requirements of auditors. The CEO should consider a review of their existing security technologies and processes in place to minimize these losses in the future. Many companies are being hit with these types of attacks and only the CEO can provide the leadership and investments necessary to mitigate these types of bad outcomes. We would strongly suggest that the CEO and Board of Directors reevaluate their security vendor choices and internal processes going forward. As we can all see, perimeter protections failed and leadership needs to come to a hard realization that their interior protections were inadequate for today’s modern attacks. Appropriate privileged identity management (PIM) solutions coupled with hygienic automated management of identities might have reduced this intrusion to a non-event.
So I was recently at the big Motorola launch event which spanned New York City, Mexico City, Sao Paulo and London where I was part of the media herd waiting to see exactly what new handsets were about to be revealed. The answer came in triplicate: the Moto X Style, Moto X Play and the new third generation Moto G. As the latter of these was the only device to actually go on sale with immediate effect, and Motorola had review units available to take away, it's the Moto G that I am reviewing here today having put it through the ropes for the last ten days. Given that the long awaited OnePlus 2 goes on sale here in the UK this coming week (August 11th) I wanted to answer a question I had posed for myself: is the new Moto G a OnePlus 2 killer or not?

Both the Moto G and OnePlus 2 position themselves as low cost but high spec smartphones, proving that you don't have to sacrifice too much in terms of technical toys to the gods of thrift in order to own the kind of mobile phone that your friends and colleagues will be envious of. The new third generation Moto G certainly does not disappoint when you get it out of the box; this does not feel like a budget handset. In fact, even though it doesn't sport the gimmicky wrap around screen or full metal bodywork of the …
News has broken this weekend that the personal data, including bank account details, of some 2.4 million customers of the Carphone Warehouse may have been compromised following a breach that the mobile phone retail giant is calling "a sophisticated cyber-attack." The company also warns that encrypted credit card data of up to 90,000 customers may have been accessed during the breach.
Scotland Yard and the Information Commissioner's Office have both been notified, along with a security outfit specialising in forensic examination of such attacks. However, the statement from Carphone Warehouse, released on Saturday, and revealing that the compromised personal details also include names, addresses and dates of birth also reveals that disocvery of the attack took place on Wednesday: "On 5 August 2015 we discovered that the IT systems of three of our online UK businesses had been subject to a sophisticated cyber attack." This will no doubt leave many customers whose data has been exposed wondering why it took a further three days for the breach to be disclosed.
Customers, it should be said, that extend further than just Carphone Warehouse itself. The official disclosure statement continues: "The three websites affected are onestopphoneshop.com, e2save.com and mobiles.co.uk. These websites also provide a number of services related to mobile phone contracts to iD mobile, TalkTalk mobile, Talk mobile and Carphone Warehouse." Now, bear in mind that this means a further 480,000 TalkTalk Mobile customers could be impacted and I expect reports of the total number of potential victims here to rise …
Your task is to show some effort, show us your code and then ask us a question we can answer.
they will tend to kill people in the real society. Because, they will consider that killing is legal.
And can you provide any evidence at all to back up that wild statement? Violent video games have been around for decades now, yet as far as I can see there are not hoardes of kids running around killing people as a direct result in every town in every city.
Try engaging brain before operating mouth (or, in this case, keyboard)
Ye bloody gods!!! VFS Global are at it again, with the exact same bloody vulnerability on visa application services. See my exclusive investigation report at SC Magazine for more details.
Your task is to do your own bloody homework.
Closing this thread - please refer to other thread on same subject if you wish to reply.
And have another welcome from me :)
And welcome Zinist
Welcome Yofan
Far too little information for anyone to be able to help you there. Be a little more specific with your requirments, and the problems you have encountered trying to meet them, WITHOUT plugging your site please as this really isn't necessary and just makes your post smell of spam.
Dianne. What?
Degaussing doesn't guarantee erasure. Degaussing in combination with a crusher aftwerwards is a much more secure bet.
Either:
a) your laptop has been haunted by the ghost of Roger Whittaker
b) your harddrive is about to die and burn
c) your heatsink fan (most likely) bearings are shot
I'd work from c backwards myself...
Hello, G'Morning, and welcome
Well, according to his profile: "AMWebCreation is website design, development, SEO, SMO, CMS, Ecommerce, clipping path, logo design; IT training center" so all I can suggest is that if he has to come to us to get advice on what the stuff he is charging other people to train them on is, then probably best to avoid him altogether.
Unless, of course, he is just here to spam.
Action video camera vendor GoPro has announced that it is riding into the Tour de France with a promotional video to celebrate being named the official camera of the world's largest annual sporting event with a worldwide television audience of some 4 billion people, but not before the BBC reported how GoPro cameras could be used to spy on their owners.
According to security company Pen Test Partners, it is way too easy to take control of GoPro cameras and one of the partners at the outfit, Ken Munro, showed demonstrated how. He showed the BBC how a GoPro Hero4 could be used to eavesdrop on users, or to view existing video footage and delete it if desired, despite appearing to be switched off. The problem stems from users who had set the device up with simple passwords, then when the camera was put into sleep mode it could still be accessed via a wireless connection and that simple password cracked to give the attacker control.
Of course, as with all such things, it's not quite as black and white as that paragraph might suggest. The user would first have to be using a pretty lame Wi-Fi password which would be set up when the camera was connected to a mobile device such as a smartphone. Secondly, the attacker would have to intercept this encrypted key, and crack it, a standard man-in-the-middle affair but not a typical attack scenario for your average action camera user I …
Hello Micronet Computer, are you related to Eliza?
Welcome
Welcome
It is 2015 you know... Seriously, ask yourself under what circumstances you would require the use of disk-based media (either to load or to store data) for your business and then you have your answer. An answer that is likely to be different for different folk, but in the age of cloud a 'diskless' office is certainly possible.
And welcome from me...
Earlier this month, security outfit FireEye’s 'FireEye as a Service' researchers out in Singapore discovered and reported on a phishing campaign that was found to be exploiting a zero-day in Adobe Flash Player vulnerability (CVE-2015-3113). That campaign has been well and truly active for a while now, with attacking emails including links to compromised sites serving up benign content if you are lucky and a malicious version of the Adobe Flash Player complete with the exploit code if you are not.
Adobe has now responded with a security update with the following recommendations:
Users of the Adobe Flash Player Desktop Runtime for Windows and Macintosh should update to Adobe Flash Player 18.0.0.194.
Users of the Adobe Flash Player Extended Support Release should update to Adobe Flash Player 13.0.0.296.
Users of Adobe Flash Player for Linux should update to Adobe Flash Player 11.2.202.468.
Adobe Flash Player installed with Google Chrome and Adobe Flash Player installed with Internet Explorer on Windows 8.x will automatically update to version 18.0.0.194.
Here are the affected software versions:
Adobe Flash Player 18.0.0.161 and earlier versions for Windows and Macintosh
Adobe Flash Player Extended Support Release version 13.0.0.292 and earlier 13.x versions for Windows and Macintosh
Adobe Flash Player 11.2.202.466 and earlier 11.x versions for Linux
Craig Young, Security Researcher at Tripwire, reckons that "Flash, along with ActiveX and Java are remnants of the 1990s 'Web 2.0’ technology boom. The nature of these technologies allows attackers to run code directly on remote computers …
A couple of decades ago, in another life, I wrote a little script which would capture keystrokes and then store that data within the 'white space' of an image file. It was pretty crude, but it was also twenty years ago and to be honest nobody was really looking for stuff which was effectively hidden in plain sight that way. That way being the use of something called steganography, from the Greek steganos which means covered and graphie which means writing; so literally covered writing. I used it to good effect during my period as an explorer of networks belonging to other people, most notably when sysadmins would stay at my apartment and login to their networks in order to do a bit of housekeeping and, unknown to them at the time, give me root. Things have moved on a lot since then, and steganography has become a much more complex tool being deployed by cybercriminals.
Back in March this year I reported for SC Magazine on how a variant of the Vawtrak malware family had been using steganography to hide update files in tiny 4Kb encrypted favicon graphics, these in turn being distributed using the Tor network via a proxy. Fast forward to now and the Dell SecureWorks Threat Intelligence Unit has revealed how it has tracked one such malware tool, Stegoloader, which appears top have been active since 2012 and uses digital steganography to avoid detection. Stegoloader requires a core component of the malware …
Welcome Rod
The Electronic Frontier Foundation (EFF) has released the latest version of its 'Who Has Your Back?' report and accompanying infographic, and it makes for interesting reading. Once you appreciate that what the EFF is talking about here is how good, measured as a response to a handful of yes or no questions, a bunch of leading tech companies are at protecting our data from government snooping requests. It's not about privacy in the larger scheme of things, just from that particular angle.
That said, let's look at how the EFF came to the conclusions that can be seen in the accompanying graphic. Essentially the organisations concerned were asked, on a yes or no basis remember, if they fulfilled five criteria when it comes to privacy expectations regarding government snooping in the post-Snowden era: follows industry-accepted best practice, informs users about government data access demands, discloses data retention policy, discloses government content removal requests and if it has pro-user public policy which opposes encryption back doors. Here's the broad breakdown.
When it comes to 'following industry accepted best practice relating to government demands upon data access just about every company questioned. The notable exception being Whatsapp, with the messaging app failing to be awarded a star in the EFF chart courtesy of two transgressions: it didn't require a warrant before handing user data over to the man, and it didn't publish any kind of transparency report either. Oops.
Moving on, what about how the companies fared on 'informing users …
What article?
Welcome to DaniWeb
I agree with the 'of the future' bit but disagree with the assertions of parts of the IT Security industry (read: those with a vested interest) that the threat is 'here right now' which it really is not in any meaningful way at all.
As I've already been asked: it's a Mazda Bongo (yes, really) Japanese import MPV converted into a campervan with kitchen and bed in the back. :)
Speaking to TrustedReviews this week, Alexander Moiseev, Kaspersky Europe's Managing Director, has warned that your car is at serious risk of being hacked. He is, however, wrong and I'm going to explain why.

Kaspersky Lab and Mr Moiseev may well insist that the threats to the automotive industry are very real, and very much here and now; and while I don't dispute that there are concerns I do think there is a very real element of Mandy Rice-Davies Applies about the entire debate. With the demise, albeit a long and drawn out death, of desktop AntiVirus as the golden goose of the IT security industry, it should come as no real surprise when that industry looks for alternative areas to occupy. Transport is one of the much hyped, I would argue over-hyped, areas currently doing the rounds. The more the 'threat' is talked up, the more there will be a demand from consumers for 'protection' and vehicle manufacturers will turn to vendors to supply it.
That is far from my campervan being hackable now, or ever, matter of fact.
In that TrustedReviews interview, Mr Moiseev likens IT security not being involved in the design and development process of cars to having a house with no roof and putting bars on the windows to protect from theft. He argues that we don't have to wait for the autonomous self-driving Google Car for the hacking threat to materialize, and says our cars today …
I am an old admin, and I wanted to say that one more spam/advert from you and your account will be banned.
Oh, and hello...
As news breaks that a second breach at the federal Office of Personnel Management may have seen another set of data, potentially more valuable than that accessed during the first, Philip Lieberman, President of privileged identity management specialists Lieberman Software, has been talking about what went wrong. Here's what he had to say on the matter:
The apparent US Government policy with regard to the protection of commercial enterprises attacked by nation states and others has been benign neglect (perhaps a shoulder to cry on). Current law and government policy forbid commercial enterprises to take any action against the attacker and handle the matter via the rule of law and in the appropriate jurisdiction. Since there has been little to no recourse possible, commercial enterprises have been attacked and damaged with little government assistance. We are told to build better walls and operate in a defensive mode even though both our government and governments of others have cyber weapons that commercial enterprises with no effective defence. Using technologies such as air gaps, segmented networks, encryption, privileged identity management, can reduce the damage and scope of damage caused by these weapons. So there is no real defence, only the concept of acceptable loss.
On the other hand, the US Government has been clear that an attack on its citizens and systems would result in severe response directed by the government itself (which is well within its power and rights). However, there are two issues …
It's been a year now since the Dyre malware family was first profiled, and there is no sign of infection rates slowing down. In fact, reports would seem to suggest just the opposite with infections up from 4,000 at the end of last year to 9,000 at the start of this. The lion's share being split pretty evenly between European and North American users.
So I was interested to spot this Tweet from Ronnie T @iHeartMalware who is actually Ronnie Tokazowski, a senior researcher at PhishMe, which declares: "I'm tired of dumping #Dyre configurations by hand. So I wrote a python script to do it. Enjoy folks!"
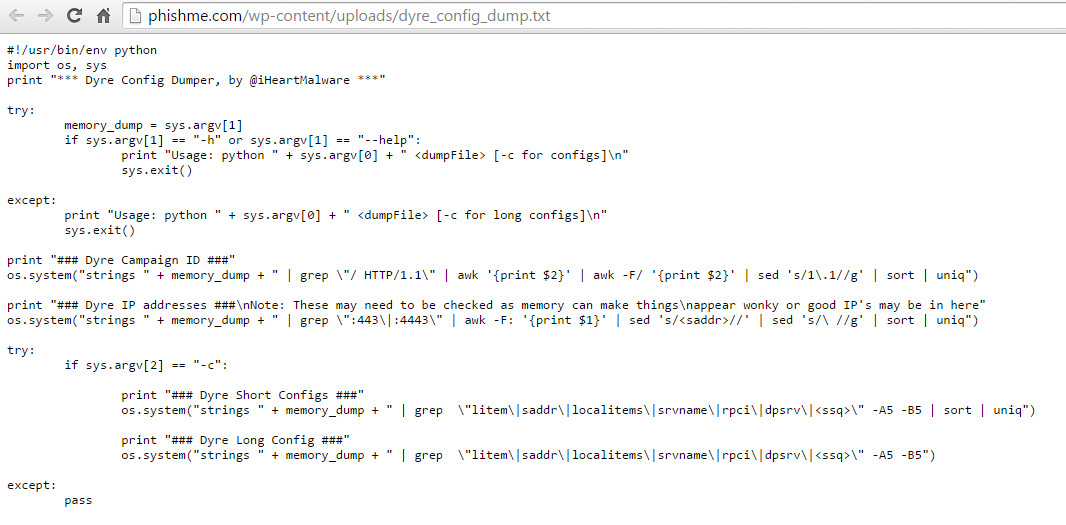
Ronnie explains "It’s been over a year since Dyre first appeared, and with a rise of infections in 2015, it doesn’t look like the attackers are stopping anytime soon. At PhishMe we’ve been hit with a number of Dyre attacks this week, so to make analysis a little easier, I tossed together a quick python script that folks can use for dumping the configurations for Dyre. To dump the memory, you can use Process Explorer to do a “full dump” on the process they inject into. (Typically the top-most svchost.exe, sometimes explorer.exe)."
Here's the script for all you Python fans to have a look at.
Researchers at security company AppRiver have issued a warning regarding a variant of the Fareit malware family which is using fake Amazon purchase confirmation emails to inject itself and steal any type of crypto currency that can be found on the target machine.
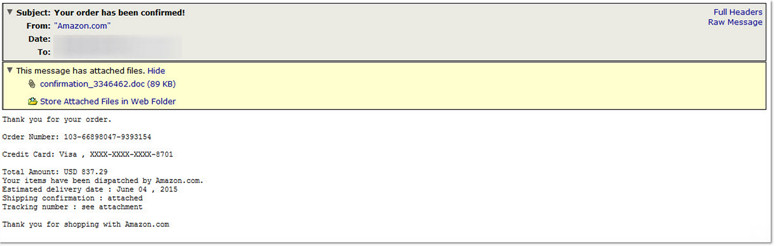
Troy Gill, manager of security research at AppRiver, details how his team have been monitoring, and blocking, what he describes as a stream of malicious emails during the last week. All posing as legitimate Amazon purchase confirmations, all stating that 'your order has been confirmed’ and all directing the reader to the attached, and infected, .doc file for the shipping and tracking details. If the recipient has macro's enabled in Microsoft Office, specifically Microsoft Word, then their machine will become infected upon opening that document. Although it has never really gone away entirely, the Word Macro threat has seen something of a resurgence in recent months and this is just the latest in a long line of examples.
"This family of malware is often distributed via Word documents with malicious macros embedded and has been known to drop multiple malware variants on the target machine" Troy Gill explains, continuing "in this particular case the malware quickly goes to work attempting to steal the Outlook password along with website passwords from various browsers such as Firefox, IE, Chrome and Opera. It then attempts to harvest account credentials for a lengthy list of FTP and multiple file storage programs."
It …
Nor here (Chrome) or (FireFox).
So rather than someone asking for a community member to do a job for them, you mean a community member (you) offering your services to people posting for help but for a fee? That sounds pretty much like spam/advertising to me, to be honest. Unless I'm still confused by what you are actually suggesting of course.
Surely a 'SEO Services Company' as your sig suggests would know this already?
Either that, or it is a crap SEO company...
As for the newsletter draft, for some reason it did end up in my spam folder. Has never done that before, have flagged it to ensure it doesn't happen again.
That's a relief. A bit of an upswing of spam along with spotting that banned badge thing made me wonder if the system was broken. Very glad it isn't :)