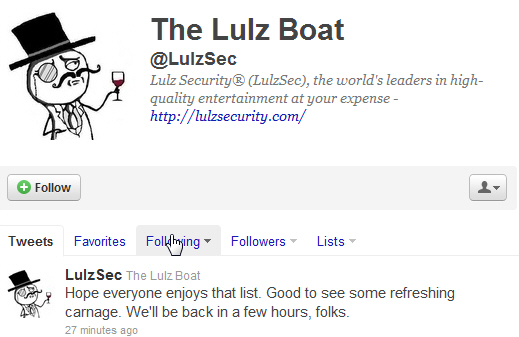
I am sorry to say that DaniWeb is once again under concerted attack by Chinese and Russian spammers. The admin and moderator teams have been working around the clock these last 48 hours to delete spam postings and remove the offending accounts, and will continue to do so until the attackers have been defeated.
However, we are only human and some spam may slip through unnoticed - which is where you come in. Can we please ask the DaniWeb community to be extra vigilant at the moment and use the flag bad post facility to report any postings which are spam so that we can then deal with the accounts in question.
All spam accounts are being banned on the spot, no warnings will be given during this period of sustained attack.
 Three and a half years ago, DaniWeb was reporting how
Three and a half years ago, DaniWeb was reporting how 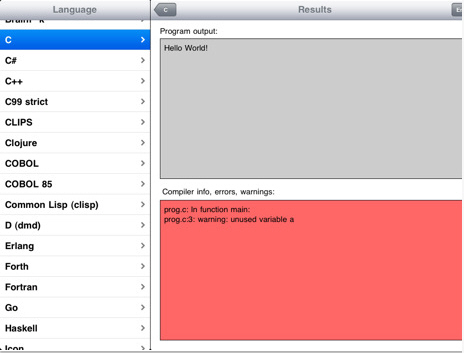 CodeToGo is, essentially, an API wrapper around the Ideone.com online compiler and debugger that enables you to use it to compile and run code in around 50 different programming languages on your iPhone or iPad. It has been around for a while but has always been somewhat tarnished with the 'toy' label courtesy of a total inability to load or save code snippets, requiring you to type them in manually. Actually that wasn't quite the case either, although many thought it to be, as you could always use the ideone.com site to email the code snippets. However, this latest app update pretty much resolves the load/save issue by adding the ability to import and export files using Dropbox to the existing functionality which automatically saves the current code you are working on for any given language. You can now also save and load different files for each language. The Dropbox solution works well in practise, simply touch "Save" whilst editing and then go for the pretty obvious "Save to Dropbox" option. To load then, as I'm sure you have worked out by now, you do the same thing but use the "Load from Dropbox" option instead. It's a much neater solution than importing and exporting files by syncing to iTunes from your computer using the file sharing option.
CodeToGo is, essentially, an API wrapper around the Ideone.com online compiler and debugger that enables you to use it to compile and run code in around 50 different programming languages on your iPhone or iPad. It has been around for a while but has always been somewhat tarnished with the 'toy' label courtesy of a total inability to load or save code snippets, requiring you to type them in manually. Actually that wasn't quite the case either, although many thought it to be, as you could always use the ideone.com site to email the code snippets. However, this latest app update pretty much resolves the load/save issue by adding the ability to import and export files using Dropbox to the existing functionality which automatically saves the current code you are working on for any given language. You can now also save and load different files for each language. The Dropbox solution works well in practise, simply touch "Save" whilst editing and then go for the pretty obvious "Save to Dropbox" option. To load then, as I'm sure you have worked out by now, you do the same thing but use the "Load from Dropbox" option instead. It's a much neater solution than importing and exporting files by syncing to iTunes from your computer using the file sharing option. 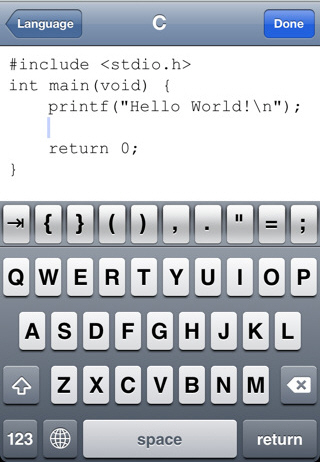 Just as ideone.com describes itself as 'more than a pastebin' so the same is true of CodeToGo. You can write your code and …
Just as ideone.com describes itself as 'more than a pastebin' so the same is true of CodeToGo. You can write your code and …

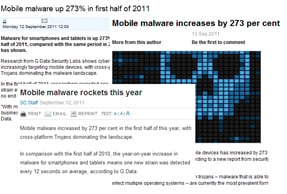 Mobile phone security threats used to be mocked by everyone outside of vendors with mobile antivirus software to sell. That has changed, and how. The online media headlines have been full to bursting with reports that 'mobile malware' had grown by a staggering 273 percent in the first half of 2011 when compared to the same period for the year before. But can that be true? The answer, it would seem, is no. It's actually much, much worse. Maybe.
Mobile phone security threats used to be mocked by everyone outside of vendors with mobile antivirus software to sell. That has changed, and how. The online media headlines have been full to bursting with reports that 'mobile malware' had grown by a staggering 273 percent in the first half of 2011 when compared to the same period for the year before. But can that be true? The answer, it would seem, is no. It's actually much, much worse. Maybe. 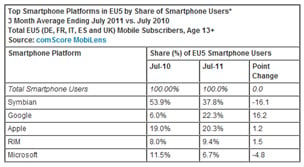 It's official: Android now has a greater market share than iPhone across the EU5 countries of France, Germany, Italy, Spain and the UK. According to newly published data from the
It's official: Android now has a greater market share than iPhone across the EU5 countries of France, Germany, Italy, Spain and the UK. According to newly published data from the  Ever wondered just how many domain names there are on the Internet? DaniWeb has, and can reveal the answer as being an almost astonishing 215 million worldwide.
Ever wondered just how many domain names there are on the Internet? DaniWeb has, and can reveal the answer as being an almost astonishing 215 million worldwide.  It would appear that a Florida bank has been the victim of a $13 million ATM heist, but just how did the cyber-robbers pull it off?
It would appear that a Florida bank has been the victim of a $13 million ATM heist, but just how did the cyber-robbers pull it off? In an unusual take on the usual 'my smartphone is better than your smartphone' debate, a new survey has revealed that when it comes to the amount of time we spend using our handset of choice, iPhone users are the biggest addicts. So addicted, in fact, that many iPhone users cannot bear to be parted from their smartphone no matter where they are: and that includes the loo.
In an unusual take on the usual 'my smartphone is better than your smartphone' debate, a new survey has revealed that when it comes to the amount of time we spend using our handset of choice, iPhone users are the biggest addicts. So addicted, in fact, that many iPhone users cannot bear to be parted from their smartphone no matter where they are: and that includes the loo.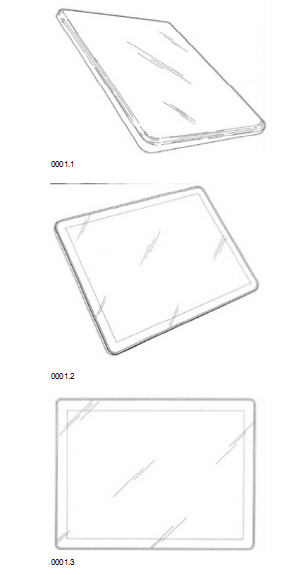 OK, so Apple has successfully
OK, so Apple has successfully 
 Users of the iPhone have stood accused of many things, from being more interested in form than function through to having more money than sense. However, the iPhone bashing has taken an unexpected turn as new research suggests that smartphone users are becoming increasingly rude both at home and in the workplace.
Users of the iPhone have stood accused of many things, from being more interested in form than function through to having more money than sense. However, the iPhone bashing has taken an unexpected turn as new research suggests that smartphone users are becoming increasingly rude both at home and in the workplace.
 The British website for pop sensation Lady Gaga has been hacked, it's official. The website was targeted by the US SwagSec hacking group it would appear, a group which has a track record (if you'll excuse the pun) of hacking the official websites of pop stars having already hit Justin Bieber and Amy Winehouse to name but two. Universal Music has now confirmed that part of a database was copied and the names and email address records of Lady Gaga fans accessed. The record label was at pains to point out that no passwords or credit card data was stolen. Although precise numbers are not known, it is thought that thousands of fans have had their personal information accessed by the hackers. SwagSec hackers also, according to a number of reports, issued a death threat against Lady Gaga.
The British website for pop sensation Lady Gaga has been hacked, it's official. The website was targeted by the US SwagSec hacking group it would appear, a group which has a track record (if you'll excuse the pun) of hacking the official websites of pop stars having already hit Justin Bieber and Amy Winehouse to name but two. Universal Music has now confirmed that part of a database was copied and the names and email address records of Lady Gaga fans accessed. The record label was at pains to point out that no passwords or credit card data was stolen. Although precise numbers are not known, it is thought that thousands of fans have had their personal information accessed by the hackers. SwagSec hackers also, according to a number of reports, issued a death threat against Lady Gaga. Earlier this week a hacker group called Dev-Team launched a revamped website service that enables owners of the iPhone 4 and iPad 2 (amongst a myriad other iOS-powered devices) to jailbreak them in next to no time, for free, online. The
Earlier this week a hacker group called Dev-Team launched a revamped website service that enables owners of the iPhone 4 and iPad 2 (amongst a myriad other iOS-powered devices) to jailbreak them in next to no time, for free, online. The  Imagine lining up 57.5 billion Apple iPads to build a wall measuring about 4000 miles long and 60 feet high. To put that into perspective, think of the Great Wall of China cloned and stacked on one top of the other, that's how big we are talking here folks. Now imagine all of those iPads stuffed choc-a-bloc with data. 1.8 zettabytes (or 1 billion terabytes if you prefer) of it to be precise.
Imagine lining up 57.5 billion Apple iPads to build a wall measuring about 4000 miles long and 60 feet high. To put that into perspective, think of the Great Wall of China cloned and stacked on one top of the other, that's how big we are talking here folks. Now imagine all of those iPads stuffed choc-a-bloc with data. 1.8 zettabytes (or 1 billion terabytes if you prefer) of it to be precise. Penetration testing by the US Department of Homeland Security which involved dropping USB thumb drives and various data discs around the car parks of government agency buildings has revealed a not-so-shocking truth: just like most folk, government workers allow curiosity to trump security when faced with the opportunity to have a nosey at something they think they shouldn't be looking at.
Penetration testing by the US Department of Homeland Security which involved dropping USB thumb drives and various data discs around the car parks of government agency buildings has revealed a not-so-shocking truth: just like most folk, government workers allow curiosity to trump security when faced with the opportunity to have a nosey at something they think they shouldn't be looking at.