The Serious Organised Crime Agency (SOCA) website remains offline after being hit by a Distributed Denial of Service (DDoS) attack for the second time in the space of a year. Last June it was the hacktivist group LulzSec which claimed responsibility; this time nobody has yet come forward to admit they did it and explain why. However, it seems likely that hacking collective Anonymous could be behind the strike in protest over the decision of the UK's High Court to order all Internet Service Providers to block access to The Pirate Bay.
 The SOCA website has been unavailable since late on Wednesday night by the attack which apparently continues unabated. The decision to take the website offline was taken in order to "limit the impact" of the DDoS attack according to a SOCA spokesperson. It has to be said that as the whole point of a DDoS attack is to take down a website by making it impossible to access, the impact of thr attack would appear to be pretty complete. Of course, I understand that there are implications beyond the site in question, and other sites hosted with the same service provider could be impacted by an ongoing attack.
The SOCA website has been unavailable since late on Wednesday night by the attack which apparently continues unabated. The decision to take the website offline was taken in order to "limit the impact" of the DDoS attack according to a SOCA spokesperson. It has to be said that as the whole point of a DDoS attack is to take down a website by making it impossible to access, the impact of thr attack would appear to be pretty complete. Of course, I understand that there are implications beyond the site in question, and other sites hosted with the same service provider could be impacted by an ongoing attack.
While most commentators and security experts were pointing the finger at 'groups unknown' initially, and suggesting that the recent takedown of some 36 websites selling stolen credit card data could be behind the attack, I'm not so sure this is the case. Cybercriminals …

 As a journalist who has spent the largest part of the last 20 years online, not a great deal makes me sit up and my jaw drop with disbelief anymore. However, when a chap called Mike Hall copied me in on a support conversation he had with eBay, I have to admit I was rather in danger of spitting my coffee all over the keyboard.
As a journalist who has spent the largest part of the last 20 years online, not a great deal makes me sit up and my jaw drop with disbelief anymore. However, when a chap called Mike Hall copied me in on a support conversation he had with eBay, I have to admit I was rather in danger of spitting my coffee all over the keyboard.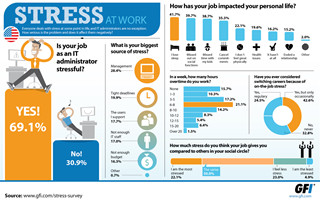 Asking 201 UK-based IT Administrators working at businesses of between 10 and 500 employees, the survey found that 66% of those questioned considered their jobs just as stressful, or more stressful, when compared to others in their immediate social circle. The amount of stress would seem to vary according to the size of the company concerned, with 56% claiming to be stressed where between 10 and 49 staff are employed but 84% where that figure is between 50 and 99.
Asking 201 UK-based IT Administrators working at businesses of between 10 and 500 employees, the survey found that 66% of those questioned considered their jobs just as stressful, or more stressful, when compared to others in their immediate social circle. The amount of stress would seem to vary according to the size of the company concerned, with 56% claiming to be stressed where between 10 and 49 staff are employed but 84% where that figure is between 50 and 99. The Hacker Intelligence 'Automation of Attacks'
The Hacker Intelligence 'Automation of Attacks'  The report took into account various factors such as income, stress, physical demands and career outlook in order to compile the listings. Report publisher Tony Lee explains that the top-rated jobs all have "few physical demands, minimal stress, a good working environment and a strong hiring outlook".
The report took into account various factors such as income, stress, physical demands and career outlook in order to compile the listings. Report publisher Tony Lee explains that the top-rated jobs all have "few physical demands, minimal stress, a good working environment and a strong hiring outlook". The data analysed came from more than two years worth of social media streams in both the USA and Ireland, and was checked for any references to unemployment and how people hit by it were coping. By using a process of mood scores and conversation volume comparison to the official unemployment statistics in both countries, SAS and the UN Global Pulse researchers were able to determine that increased chatter about 'cutting back' and 'public transportation usage' as well as 'downgrading the car' were positive indicators in predicting an unemployment spike.
The data analysed came from more than two years worth of social media streams in both the USA and Ireland, and was checked for any references to unemployment and how people hit by it were coping. By using a process of mood scores and conversation volume comparison to the official unemployment statistics in both countries, SAS and the UN Global Pulse researchers were able to determine that increased chatter about 'cutting back' and 'public transportation usage' as well as 'downgrading the car' were positive indicators in predicting an unemployment spike. The research labs team has documented a high number of spam and malware distribution campaigns during the month of March which have successfully infiltrated users' systems disguised as communications from well-known companies or pretending to be promotions for their services and products.
The research labs team has documented a high number of spam and malware distribution campaigns during the month of March which have successfully infiltrated users' systems disguised as communications from well-known companies or pretending to be promotions for their services and products.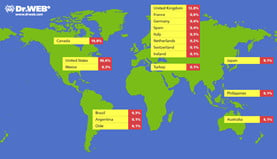 Dr Web
Dr Web  The researchers suspect that the attack stems from the same anti-Tibetan, pro-Chinese, hacking group that has been
The researchers suspect that the attack stems from the same anti-Tibetan, pro-Chinese, hacking group that has been 





 I still have my Compaq Concerto from 1992, which is generally accepted as the first ever mainstream Tablet PC. It ran Windows for PEN Computing Version 1, which was actually just Windows 3.1 with some rather rudimentary pen input add-ons included. Although I have sentimental reasons for hanging on to the world's first real commercial tablet, I will readily admit that it sucked elephants through a straw and the reason why was that damn-awful PEN Windows OS abomination.
I still have my Compaq Concerto from 1992, which is generally accepted as the first ever mainstream Tablet PC. It ran Windows for PEN Computing Version 1, which was actually just Windows 3.1 with some rather rudimentary pen input add-ons included. Although I have sentimental reasons for hanging on to the world's first real commercial tablet, I will readily admit that it sucked elephants through a straw and the reason why was that damn-awful PEN Windows OS abomination. INTERPOL unleashed
INTERPOL unleashed  Of the people interviewed, some 41 percent actually have two or more mobile phones in order to ensure such a lack of connectivity never strikes. Women are more likely (70 percent) to be scared of cellphone loss than men (61 percent), while men (47 percent) are more likely to have two phone than women (36 percent). "I’d be inclined to draw the conclusion that, perhaps because more men have two phones, they’re less likely to misplace both and therefore be left phone-less" said Andy Kemshall
Of the people interviewed, some 41 percent actually have two or more mobile phones in order to ensure such a lack of connectivity never strikes. Women are more likely (70 percent) to be scared of cellphone loss than men (61 percent), while men (47 percent) are more likely to have two phone than women (36 percent). "I’d be inclined to draw the conclusion that, perhaps because more men have two phones, they’re less likely to misplace both and therefore be left phone-less" said Andy Kemshall  The press release exclaimed that the Apple iPad was failing to be used by online shoppers and went on to reveal that a nationwide study of consumer habits in the UK had shown that Brits are not embracing tablets for online shopping and claimed that "only 4 percent of Brits are using a tablet for online shopping".
The press release exclaimed that the Apple iPad was failing to be used by online shoppers and went on to reveal that a nationwide study of consumer habits in the UK had shown that Brits are not embracing tablets for online shopping and claimed that "only 4 percent of Brits are using a tablet for online shopping".
 The lawsuit was filed by Liberty Media Holdings, a producer of adult movie content based in San Diego, and accuses in excess of 50 people in Massachusetts (where the lawsuit has been filed) of downloading and consequently sharing a gay porn movie illegally via BitTorrent. The complaint itself makes a point of claiming that the defendants either have direct responsibility as they downloaded the movie themselves or, importantly, that they contributed to the act of piracy by way of their negligence in not securing the wireless network concerned. In other words, whether they downloaded it themselves or not doesn't matter, they are being held responsible for the controlling, or rather not controlling in this case, access to the Internet which was then used to infringe copyright.
The lawsuit was filed by Liberty Media Holdings, a producer of adult movie content based in San Diego, and accuses in excess of 50 people in Massachusetts (where the lawsuit has been filed) of downloading and consequently sharing a gay porn movie illegally via BitTorrent. The complaint itself makes a point of claiming that the defendants either have direct responsibility as they downloaded the movie themselves or, importantly, that they contributed to the act of piracy by way of their negligence in not securing the wireless network concerned. In other words, whether they downloaded it themselves or not doesn't matter, they are being held responsible for the controlling, or rather not controlling in this case, access to the Internet which was then used to infringe copyright.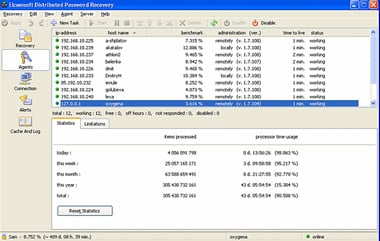 Elcomsoft CTO Andy Malyshev says that as Apple iWork is sold at consumer market price points it is less likely that the average user will have a security policy that enforces a long and complex password, making the distributed attack methodology and its 500 attempts per second barrier worthwhile. What's more he
Elcomsoft CTO Andy Malyshev says that as Apple iWork is sold at consumer market price points it is less likely that the average user will have a security policy that enforces a long and complex password, making the distributed attack methodology and its 500 attempts per second barrier worthwhile. What's more he  Prolexic Technologies, which specialises in Distributed Denial of Service (DDoS) mitigation services, has today issued an in-depth threat advisory for Dirt Jumper together with a custom-developed scanning tool that can be used to detect Dirt Jumper command and control servers. Neal Quinn, vice president of operations at Prolexic, warns that his company is "seeing this tool used against clients worldwide and it is likely to become more widespread and effective as distribution spreads."
Prolexic Technologies, which specialises in Distributed Denial of Service (DDoS) mitigation services, has today issued an in-depth threat advisory for Dirt Jumper together with a custom-developed scanning tool that can be used to detect Dirt Jumper command and control servers. Neal Quinn, vice president of operations at Prolexic, warns that his company is "seeing this tool used against clients worldwide and it is likely to become more widespread and effective as distribution spreads." Of course, there was no iPad. The Lady Gaga Twitter account had been hacked and if you clicked on that link it would take you to a number of different sites via redirects and then dump you at a survey designed to scam you out of valuable personal information. Equally 'of course' as soon as the tweet appeared it was retweeted by thousands of innocent fans keen to spread the apparent good news, meaning the scope of this particular scam is truly epic. Even though the first link in the chain has now been suspended by Bit.ly for being suspicious, the chances are that other links will be out there and still live so don't be sucked into the scam yourself. Even at this time of year, especially at this time of year, there's no such thing as a free iPad.
Of course, there was no iPad. The Lady Gaga Twitter account had been hacked and if you clicked on that link it would take you to a number of different sites via redirects and then dump you at a survey designed to scam you out of valuable personal information. Equally 'of course' as soon as the tweet appeared it was retweeted by thousands of innocent fans keen to spread the apparent good news, meaning the scope of this particular scam is truly epic. Even though the first link in the chain has now been suspended by Bit.ly for being suspicious, the chances are that other links will be out there and still live so don't be sucked into the scam yourself. Even at this time of year, especially at this time of year, there's no such thing as a free iPad. Although the SmartControl Motion we have been playing with did not come with the Sony PS3 adapter that allowed the previously reviewed gizmo to control your PlayStation as well along with the rest of your home entertainment kit, the truth is that the two remote controls are essentially the same. So they both have the same 'smart' learning facility which makes programming the thing for your TV, DVD or Blu-ray player, stereo, set top box and the like a doddle for a start. In fact, the SmartControl Motion was a real delight in this regard, taking the concept even further than before to become a very refined process involving nothing more than pressing a learn button and a single digit for all but the most obscure of electronics brands. Once the remote has been programmed for use with your personal selection of home entertainment kit, it functions the same as before.
Although the SmartControl Motion we have been playing with did not come with the Sony PS3 adapter that allowed the previously reviewed gizmo to control your PlayStation as well along with the rest of your home entertainment kit, the truth is that the two remote controls are essentially the same. So they both have the same 'smart' learning facility which makes programming the thing for your TV, DVD or Blu-ray player, stereo, set top box and the like a doddle for a start. In fact, the SmartControl Motion was a real delight in this regard, taking the concept even further than before to become a very refined process involving nothing more than pressing a learn button and a single digit for all but the most obscure of electronics brands. Once the remote has been programmed for use with your personal selection of home entertainment kit, it functions the same as before.

