Warnings have been issued today not to complete a customer satisfaction survey that appears to come from McDonald's and promises cash for your answers. A bit like fast food itself, something that looks appetising and promises a quick fix is often not actually that good for you.
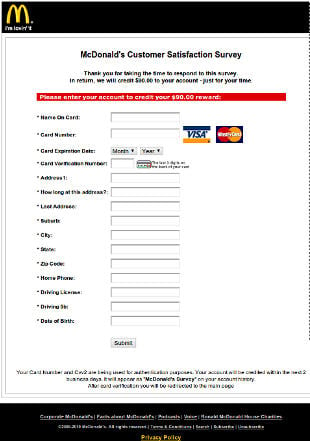 IT security and data protection company Sophos has today warned members of the public not to complete a customer satisfaction survey that promises cash in return for completing what claims to be a questionnaire about fast food originating from the McDonald's chain.
IT security and data protection company Sophos has today warned members of the public not to complete a customer satisfaction survey that promises cash in return for completing what claims to be a questionnaire about fast food originating from the McDonald's chain.
The survey is being spread by an email spam campaign of some considerable size, and purporting to come from the 'McDonald's Survey Department' using a subject line of 'McDonald's Customer Survey'. The full text of the email reads : "Dear customer, Please give us only 5 minutes of your valuable time to ask you some questions about our products. Please be aware that we will not ask you about any personal information. In return, we will credit $90.00 to your account - just for your time. If you want to answer our simply 8 questions, please click the link below. Thank you for helping us to become better. Sincerely, McDonald's Survey Department. Please do not reply to this email. This mailbox is not monitored and you will not receive a response."
If someone opts to take the survey, they are then asked to provide a bunch of personal information as well as their credit card …
 What Dane-Elec has managed to achieve with the newly launched myDitto Server is quite remarkable: this is a truly beginner level, three-step, plug and play NAS device. Seriously folks, not only do you not need to be a network engineer to set it up but you don't need to have one as a close friend you can call for when things go pear shaped either. The amount of technical know-how required to set up the myDitto is approaching a big fat zero, and just requires three basic steps as follows:Plug the myDitto Server into your router and power it up. Now plug one of the supplied myDitto USB keys into your PC (or Mac for that matter) and run …
What Dane-Elec has managed to achieve with the newly launched myDitto Server is quite remarkable: this is a truly beginner level, three-step, plug and play NAS device. Seriously folks, not only do you not need to be a network engineer to set it up but you don't need to have one as a close friend you can call for when things go pear shaped either. The amount of technical know-how required to set up the myDitto is approaching a big fat zero, and just requires three basic steps as follows:Plug the myDitto Server into your router and power it up. Now plug one of the supplied myDitto USB keys into your PC (or Mac for that matter) and run …

 The provocatively named Android Police site last week claimed that
The provocatively named Android Police site last week claimed that 
 Security researchers at
Security researchers at  According to a
According to a  The incident occurred when an unencrypted back-up tape containing those 46,000 customer records disappeared in transit between two sites in South Africa in 2008, although apparently it took the best part of a year before Zurich UK heard about the data loss.
The incident occurred when an unencrypted back-up tape containing those 46,000 customer records disappeared in transit between two sites in South Africa in 2008, although apparently it took the best part of a year before Zurich UK heard about the data loss.  In a truly bizarre attack on some of the most successful and popular providers of email across the planet, Michael Reagan insists that every time someone with conservative political views uses their email from these companies they are "helping the liberals".
In a truly bizarre attack on some of the most successful and popular providers of email across the planet, Michael Reagan insists that every time someone with conservative political views uses their email from these companies they are "helping the liberals".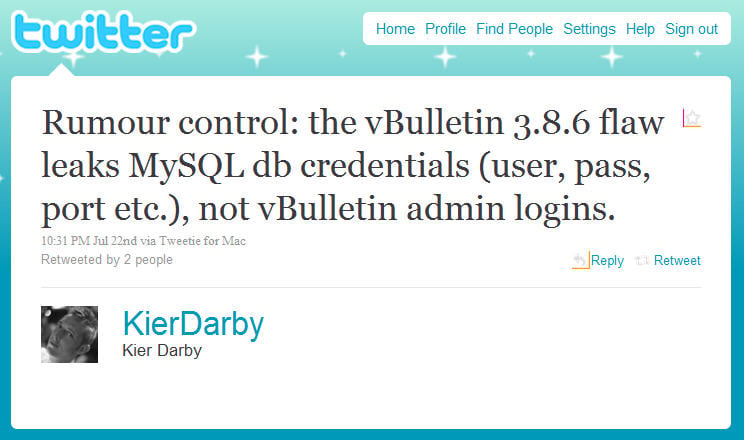 Let's answer the most important question first: No, DaniWeb users are not and have never been at risk from this security flaw as it only impacted upon a specific new version of vBulletin that was released on the 13th July and which DaniWeb has not upgraded to.
Let's answer the most important question first: No, DaniWeb users are not and have never been at risk from this security flaw as it only impacted upon a specific new version of vBulletin that was released on the 13th July and which DaniWeb has not upgraded to. The
The 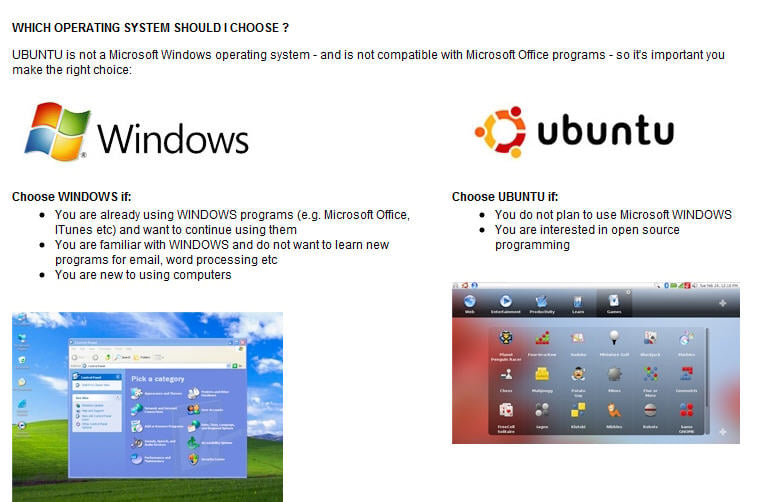 Three years ago Dell went Ubuntu bashing, making it really pretty hard to buy a Linux-loaded machine from the vendor. The Linux machines back then cost more than the Windows ones, there were warnings about it not being compatible with lots of software and to top it all the
Three years ago Dell went Ubuntu bashing, making it really pretty hard to buy a Linux-loaded machine from the vendor. The Linux machines back then cost more than the Windows ones, there were warnings about it not being compatible with lots of software and to top it all the  However, within 48 hours the inevitable weight of Bieber fans has taken its toll and the Baby video has now pulled well clear with 247,991,181 views compared to 'just' 246,609,606 views for Lady Gaga. To put this in to some kind of perspective, the third most viewed YouTube video of all time is 'Charlie bit my finger - again' featuring a cute kid and his baby brother with 210,601,397 views.
However, within 48 hours the inevitable weight of Bieber fans has taken its toll and the Baby video has now pulled well clear with 247,991,181 views compared to 'just' 246,609,606 views for Lady Gaga. To put this in to some kind of perspective, the third most viewed YouTube video of all time is 'Charlie bit my finger - again' featuring a cute kid and his baby brother with 210,601,397 views.  Security researchers at Sophos are warning that scammers have struck on Facebook with a message that is spreading fast by proclaiming "I am part of the 98.0% of people that are NEVER gonna drink Coca Cola again after this HORRIFIC video" and which includes a link.
Security researchers at Sophos are warning that scammers have struck on Facebook with a message that is spreading fast by proclaiming "I am part of the 98.0% of people that are NEVER gonna drink Coca Cola again after this HORRIFIC video" and which includes a link.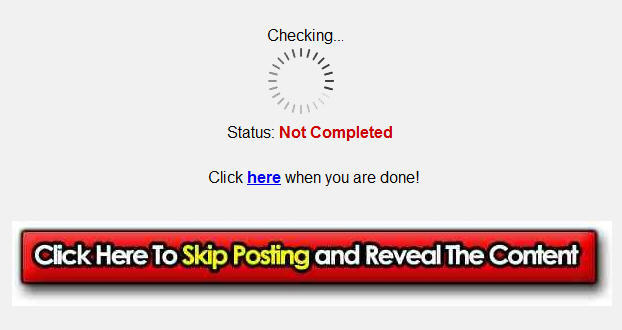 If you hit this link, you get taken to a survey section which …
If you hit this link, you get taken to a survey section which …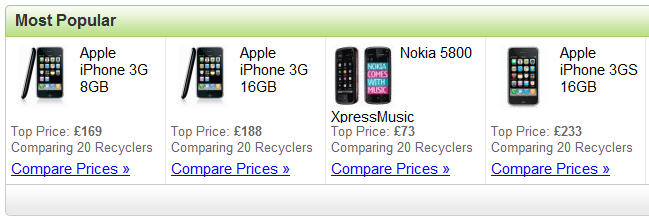 I was recently checking out what kind of recycling value
I was recently checking out what kind of recycling value  Was it really over three years ago now that I penned a story here on DaniWeb entitled
Was it really over three years ago now that I penned a story here on DaniWeb entitled 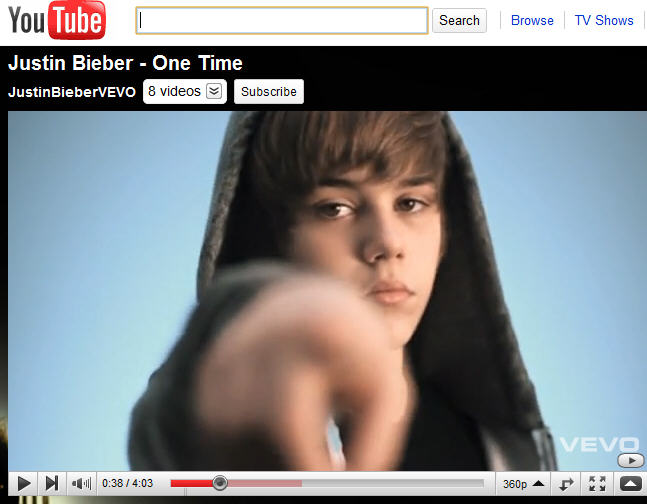 As well as using Justin Bieber video clips as the bait for the attack, the hackers also took the opportunity to leave abusive and obscene comments about the popular teen idol singer. A number of banner messages even appeared beneath the most popular Bieber videos proclaiming that he was dead.
As well as using Justin Bieber video clips as the bait for the attack, the hackers also took the opportunity to leave abusive and obscene comments about the popular teen idol singer. A number of banner messages even appeared beneath the most popular Bieber videos proclaiming that he was dead. 
 Monica Basso, research vice president at Gartner, points to how the productivity gains achieved with using wireless e-mail are driving adoption beyond the purely executive reach and reveals that "in 2010, enterprise wireless e-mail is still a priority for organizations, whose mobile workforces are up to 40 per cent of the total employee base. Most midsize and large organizations in North America and Europe have deployed enterprise wireless e-mail already, but on average, for less than five percent of the workforce."
Monica Basso, research vice president at Gartner, points to how the productivity gains achieved with using wireless e-mail are driving adoption beyond the purely executive reach and reveals that "in 2010, enterprise wireless e-mail is still a priority for organizations, whose mobile workforces are up to 40 per cent of the total employee base. Most midsize and large organizations in North America and Europe have deployed enterprise wireless e-mail already, but on average, for less than five percent of the workforce." I was able to locate plenty of copies of the article by Richard Ashmore which that is was "a hugely embarrassing move for Apple" although truth be told it was actually much more embarrassing for the Daily Mail I would imagine. What a shame that a "spokesperson for Apple was not immediately available to comment" to the story, or Mr Ashmore would have probably have been pointed in the direction of the bio for that '
I was able to locate plenty of copies of the article by Richard Ashmore which that is was "a hugely embarrassing move for Apple" although truth be told it was actually much more embarrassing for the Daily Mail I would imagine. What a shame that a "spokesperson for Apple was not immediately available to comment" to the story, or Mr Ashmore would have probably have been pointed in the direction of the bio for that ' 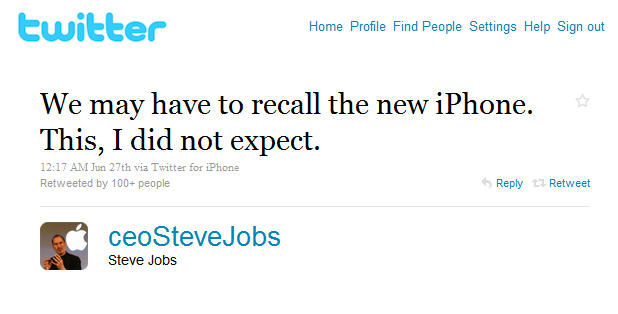 Or maybe the journalist should have looked at some of the other ceoSteveJobs Tweets before coming to the conclusion that it must the real deal. Would the CEO of one of the biggest companies on the planet actually post such things as "FaceTime video calls are the future of AppleCare support" …
Or maybe the journalist should have looked at some of the other ceoSteveJobs Tweets before coming to the conclusion that it must the real deal. Would the CEO of one of the biggest companies on the planet actually post such things as "FaceTime video calls are the future of AppleCare support" … If you cannot wait to get hold of the new iPhone 4, should you have been lucky enough to have successfully pre-ordered, then you could always upgrade your existing iPhone 3G/3GS to iOS 4 and get many of the same features.
If you cannot wait to get hold of the new iPhone 4, should you have been lucky enough to have successfully pre-ordered, then you could always upgrade your existing iPhone 3G/3GS to iOS 4 and get many of the same features. The box that the HandShoeMouse arrived in proudly claims that this is "the only mouse that fits like a glove" although I'd take issue with that. You don't wear it like a glove, but rather it wears you. The glove analogy does hold up when it comes to the pre-purchase ritual, however, as this is the first time I have ever needed my hand to be measured before I could purchase a mouse! The vendor website guides you through the process, with a separate order route for right and left handed users. It's not overly complicated, which is handy if you'll excuse the pun, and simply involves a ruler and some accurate measuring of the length of your hand.No ordinary rodent
The box that the HandShoeMouse arrived in proudly claims that this is "the only mouse that fits like a glove" although I'd take issue with that. You don't wear it like a glove, but rather it wears you. The glove analogy does hold up when it comes to the pre-purchase ritual, however, as this is the first time I have ever needed my hand to be measured before I could purchase a mouse! The vendor website guides you through the process, with a separate order route for right and left handed users. It's not overly complicated, which is handy if you'll excuse the pun, and simply involves a ruler and some accurate measuring of the length of your hand.No ordinary rodent