Depends on how 'old' an old person you are talking about. The people behind the simplicITy (still hate that name) are saying 50+ and I know tons of people between 50 and 60 who are very happy indeed using a netbook.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
What do you get if you combine a computer company with a group of Vegans and someone who used to present a popular children's TV show? The less than obvious answer is a Linux computer designed especially for old people.
But there you have it, and according to the press release that sits before me the awfully named simplicITy computer (what's wrong with OAPC I ask you) that is designed specifically to meet the needs of users aged 50 plus, has come about courtesy of a collaboration between a money saving website co-founded by ex Blue Peter presenter Valerie Singleton, a group called Vegan Solutions and a company by the name of Wessex Computers.
The real question I find myself asking is why? Why build a PC just for older people, and why assume that older people are either technophobic or somehow incapable of using a bog standard PC running Linux, Windows or even a Mac for that matter?
"For some time now, we have been aware of the need among older people for a simpler type of computer" Valerie Singleton says, continuing "a large number of 50 pluses only require: email, internet, a writing package, perhaps a means of storing or viewing pictures and a facility to chat. We don’t need the bells and whistles that modern computers offer, we just need something that’s simple to use and reliable".
So buy a netbook then.
The press release gets even odder, insisting that …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
This thread has been marked as solved, the arguing is helping nobody so perhaps now is the time for this particular thread to end?
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
I think, perhaps, now is the right time for this thread to wind down - or at least for participants to step back and take a deep breath before posting.
Let's not have it become a slanging match, or I will simply close the thing.
This message not aimed at anyone in particular, more just a measure of the rising thread temperature overall.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
To be fair, she seems to be good at two things: writing (her fourth book is due soon, and the first three have been best sellers) and cancer research. Those are the things we should be celebrating, not the fact that she ended up prostituting herself in order to complete her education surely?
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Botnets are, without any shadow of a doubt, one of the biggest scourges of IT security today. From sending spam to launching DDoS attacks and distributing malware, botnets can be found at the centre of most of the security problems facing computer users right now.
So wouldn't it be fun if you could take down, knock over and destroy a botnet? The good news is that it seems you can, with a little determination and a lot of inside knowledge.
Researchers at the FireEye Malware Intelligence Lab have been working hard at gathering the necessary knowledge with regards to one Botnet, known as Ozdok or perhaps more commonly Mega-D. Having got to grips with the command and control architecture, along with the fallback mechanisms used to keep the botnet alive should they come under attack, FireEye decided the time was right to strike. This meant moving out of the lab and the purely theoretical realm of botnet takedown and into the real world, which involves getting various agencies working together with an intent to destroy a botnet. So FireEye contacted ISPs, registries and registrars and set about the task in hand.
Atif Mushtaq writes that "all the major Ozdok command and control servers... have been taken down. As it turns out, no matter how many fallback mechanisms are in place, if they aren't all implemented properly, the botnet is vulnerable".
It wasn't easy, but within a 24 hour …
dcosgrove commented: Good News +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Over the weekend news broke that a worm had started infecting Jailbroken iPhones in Australia. Nobody really took the exploit too seriously as all the 'ikee worm' did was change the phone wallpaper to a picture of 80's pop singer Rick Astley in a kind of warped tribute to the RickRolling Internet meme of last year.
However, I warned at the time that "as code variants continue to appear it is only a matter of time, and probably not that much of it, before a malicious party uses it to deliver a payload that is a whole lot more troublesome than Rick Astley" and my gloomy prediction has now borne fruit.
One researcher, Peter James of Mac security specialists Intego, has revealed that a new exploit is taking advantage of the same vulnerability that the ikee worm did, the often unchanged default SSH password of Jailbroken iPhones. iPhone/Privacy.A, as Intego have creatively named it, will allow hackers to "silently copy a treasure trove of user data from a compromised iPhone: e-mail, contacts, SMSs, calendars, photos, music files, videos, as well as any data recorded by any iPhone app".
The hacker would first need to install the tool onto a computer which would then scan for any Jailbroken iPhones connected to the networks it discovers, and assuming that the root password has not been changed it can then quietly go about its business. Although there is a chance of the thing being installed on …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
First Google expressed an interest in the web browser client market, and then the operating system market and now it has launched its own open source systems programming language.
Google Go is being touted as 'expressive, concurrent, garbage-collected' and promises to produce fast code, fast. According to Google a typical build takes but a fraction of a second while the resulting programs run almost as quickly as comparable C or C++ code.
Go has, we are told, pointers but no pointer arithmetic (for random access Google says use slices which know their limits) and promotes writing systems and servers as sets of lightweight communicating processes which it has called goroutines. You can "run thousands of goroutines if you want and say goodbye to stack overflows" Google insists.
So why this and why now? Well, Google argues that while the computing landscape has changed significantly over the last decade there has not been a major systems language that has emerged alongside to exploit the increasing speed of computers, to address the dependency management that is such a big part of software development today, to counter the growing rebellion against 'cumbersome type systems' such as Java and C++, and to properly support fundamental concepts of garbage collection and parallel computation.
"We believe it's worth trying again with a new language, a concurrent, garbage-collected language with fast compilation" Google states.
It tells us that a large Go program will compile in just …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Everyone seems to be talking about how first Facebook and now Twitter are being adopted by business users, as if the concept of social networking in a business environment was somehow new. Of course, the truth is that services such as LinkedIn have been providing just that for many years now.
Indeed, LinkedIn has fairly quietly grown to some 51 million members worldwide now, yet still seems to struggle to command the same type of media pulling power that either Twitter or Facebook have when it comes to generating news headlines and publicity.
I suspect there will be no such problems today as LinkedIn cleverly announces what it calls an 'integration partnership' with none other than Twitter itself, allowing members to share their status updates between both services.
Unfortunately, while LinkedIn is getting all excited about "cross integration of the two networks through the Tweets app" which "allows members of LinkedIn to automatically share their updates on the professional network with their Twitter followers" and the ability to "select Twitter status updates to share with their LinkedIn network" simply by "adding the #in hashtag to tweets on the microblogging site" I am not jumping up and down myself. Well, at least not with joy or excitement.
It has been possible to do much the same between Facebook and Twitter accounts for some time now, and to be honest it has ended up driving me away from Facebook. I pop in rarely now, …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
DaniWeb does have a proper office you know :)
Address can be found by clicking the Contact Us link at the bottom of every page.
sknake commented: thats the page I was thinking of +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
There is free music out there, which is legal. You just have to do the donkey work and find it.
We will not be pointing you at sources of illegal music downloads however.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Some Twitter postings just demand you read them two or three times to take in what is being said in 140 characters. One such posting was made today by Mozilla CEO John Lilly which simply said: "Firefox user growth has been amazing last 8 weeks or so. +30M or so unique monthlies"
That's worth repeating, 30 million new users for Firefox in an 8 week period. Wow!
Tristan Nitot, President of Mozilla Europe, confirmed the figures when speaking to ZDNet in the UK. Nitot explains that it can calculate the number of users per month by multiplying the active daily users by a factor of three to allow for those days when they are not actually browsing the web. In confirming that Mozilla has seen a "significant increase" in Firefox user numbers, Nitot said "Firefox checks for new versions every 24 hours, when it's running, and when it checks, it pings the Mozilla server. We count the number of pings."
The figures collected show that Firefox now has some 330 million monthly users, and increase over the last eight weeks of some 10 million daily users on average. Although the numbers look good for Mozilla, and the latest global market share statistics suggest it is up around 3% from this time last year, it only has 23.75% of that world share. Microsoft, on the other hand, is in decline with a loss of 5% share during the same period, but crucially Internet Explorer still commands …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Forget the Windows 7 launch, the real big news from Microsoft this week is that it has reached a deal with Twitter to include real-time tweet data in Bing searches. If that wasn't excitement enough for the Twitterati, just a few hours after Microsoft made its announcement Google joined in and announced that it too had reached an agreement with Twitter to do the same.
If you still play buzzword bingo, then forget Web 2.0 or even Social Media if you want to score big points, the buzzword today has to be Real Time Web. And that is what has got both Microsoft and Google so excited, the notion of capturing and enabling access to data in real time. It is something of the Holy Grail as far as search is concerned, and something which the deals with Twitter makes a little more of a reality.
In an announcement on Wednesday Microsoft was positively gushing over the glory of Twitter, stating "Twitter is producing millions of tweets every minute on every subject you can imagine. The power of those tweets as a form of data that can be surfaced in search is enormous. Innovative services like Twitter give us access to public opinion and thoughts in a way that has not before been possible".
Which is why Microsoft was pleased to announce that "we now have access to the entire public Twitter feed and have a beta of Bing Twitter search for you …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
GigaTweet has been counting the total number of messages posted to Twitter in real time, and the rolling count is almost hypnotic. Overnight the 5 billionth Tweet was posted.
So what was it?
Perhaps someone speaking out against corporates trying to gag freedom of the press again? Nope.
Maybe another campaign kicking off against insensitive and homophobic ranting in the Daily Mail newspaper? Nope.
Must be an anarchist orchestrating a protest movement then? Nope.
Which surely only leaves the willy waving celebrity crowd, was it one of them letting us know they had eaten dinner with another celeb and were off to bed now? Nope.
It surely wasn't me, @happygeek, saying something profound? Nope, no chance of that I am afraid.
Actually, the 5 billionth Tweet was something of a let down, yet a refreshing reminder that the real power of Twitter is with ordinary users having ordinary conversations with their ordinary friends.
It would appear that Tweet 5,000,000,000 was posted by one Robin Sloan (@robinsloan) in reply to a user called @sexysloan9912e, and simply said "Oh lord".
Indeed.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Not only do I still read the printed word, but I still write books that are published in dead tree format as well.
As an author, I have to say that there is nothing quite like getting the pre-press copies of a proper book in your hands. The look and feel, the smell, the ability to sign inside the cover and give a copy to your loved ones (even if they don't want it) and so on. The e-book loses all of that.
It's hard to explain, I guess that all lovers of the written word will know what I mean, but there is something special about sitting down with a book that you just don't get with an e-reader device.
I say this as a confirmed geek and early adopter. Confused? You betcha!
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Odd isn't it, how Microsoft kicked up a fuss when Google announced the Chrome plugin for Internet Explorer on the grounds that it could make the browser more insecure. Indeed, it went as far as to suggest that it doubled the potential surface area for malware and scripted attacks. Yet, amazingly, Microsoft sees no such problem with installing a plugin into the Firefox browser. What's more it is installed without asking the permission of the user and, he says with more than a hint of irony, it left Firefox vulnerable to a drive-by exploit.
This is nothing new, as those with a memory for such underhand shenanigans will recall, as Microsoft started 'silently' installing a .NET Framework Assistant extension for Firefox users earlier in the year. The sting at the time was that it could not be uninstalled, and when an uninstall option was provided (after much media attention) it managed to break some other Firefox extension during the uninstall process.
So imagine the surprise when numerous Firefox users were presented with an 'Add-ons may be causing problems' popup when they had not added any new extensions. That popup quickly explained what was going on (see screenshot) determining that the Microsoft .NET Framework Assistant 1.1 may be "unstable or insecure". Given the option to restart Firefox so that the add-on could be disabled most punters would, I suspect, jump at the chance.
People have a right to be angry both at Microsoft for plugging something into a …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
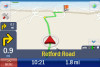
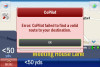
CoPilot Live 8 Mobile Navigation on the iPhone has been a runaway success at the App Store, consistently keeping ahead of its TomTom rival in the 'top grossing' app charts at least in the UK Store. It arrived first and costs half as much as the TomTom app, but is it better?
If you had asked me that question a month ago then the answer would have been a resounding no. Extensive testing showed up huge problems in keeping a GPS lock and the app even refused to start half the time I wanted it to. But then, just as I was about to post a truly damning review, something happened: a brand new update appeared at the App Store, promising to fix the problems.
I've now driven nearly 1000 miles with CoPilot on the iPhone, and can report whether the promise has been fulfilled.
After much complaint, the truly awful CoPilot keyboard has been replaced by the app making use of the proper QWERTY iPhone keyboard instead. Although this might seem like a little thing to those of you who never used it, believe me the previous keyboard was a non-QWERTY atrocity that made any attempt at data entry (like inputting a destination address for example) into a time consuming, fiddly, nightmare of epic proportions. So well done to ALK for listening to its users and replacing that, it makes getting to a destination that little bit quicker and, really, isn't that the whole point of …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
This thread is now closed - DaniWeb will not be party to discussions about taking down websites.
lllllIllIlllI commented: thankyou +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
I love Twitter, and post a lot of links to security related stories via my @happygeek account. But now I am getting a little worried that I might suffer the same fate as a well known, and highly respected security expert. Mikko Hypponen is a familiar face around the security conventions, and a familiar name to anyone who reads security news blogs. Mikko is the Chief Research Officer at F-Secure, and knows a thing or two about issuing security warnings.
Shame that Twitter cannot say the same.
It all started back on August 3rd when Mikko posted a tweet which simply read:
"I guess somebody will fall for it... a desperate MySpace phishing site at www. rnyspece. com (don't go there)."
The eagle-eyed amongst you will note that Mikko inserted spaces into the URL to prevent the hard of thinking from clicking on a link to a phishing site. You might even have spotted the words 'phishing site' and the phrase 'don't go there' which were part of the posting.
Twitter, it would seem, did not spot any of these things. Although it took the micro-blogging outfit a couple of months not to spot them and suspend the @mikkohypponen Twitter account. Yes, suspended the account of a well known Internet security expert for passing on a warning about an Internet security threat. Doh. Or, as Twitter called it, strange activity. The official Twitter response when Mikko tried to access his account was …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Sorry, jbennet is correct.
I also suggest that you reference the work in your report and cite any code which was given to you.
You asked for help, got help and now that help is available for others who might have a similar problem. That's how DaniWeb works.
If we made deleted your code, we would have to then do the same for anyone else who asked and huge gaps would appear in our support messagebase.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
I put the kibosh on it by saying everything was running fine :(
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
I believe it is calculated using the up and down votes your messages get, probably involving the number of individual members and number of individual posts which have been voted upon along the way.
I'm sure Dani will correct me when she wakes up :)
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
I think that it needs time to settle. The whole idea of such a voting system is that it employs the 'wisdom of crowds' and as such we can only see if it is actually working or not over time.
The concept is certainly sound enough, and has been successfully employed at many sites. If it works here or not, well we cannot tell yet, but Dani gets my full support for being bold enough to keep trying new ideas at DaniWeb rather than being happy with a static approach to site design.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
It would appear that a political activist from New York has been arrested by the FBI in connection with helping orchestrate G20 summit protesters in Pittsburgh. According to The Guardian the man, Eliot Madison from Queens, has been charged with hindering prosecution after helping G20 protesters evade police by using Twitter.
Along with another man, Madison is said to have been tracked by law enforcement agents to a motel room during the summt, where he was found in front of a row of laptops and emergency frequency radio scanners.
The official police documents say that both men were using Twitter in order to "inform the protesters and groups of the movements and actions" of law enforcement during the protests. Of course, it should come as no surprise that Twitter is being used to help organise political protest if, indeed, that were the case in this instance. After all, people Tweeting have a proud and proven track record of providing information during all kinds of political disturbances around the world.
When it is someone using Twitter to report on the movements of police during a rebellion in a hostile nation then it is positively encouraged by the US authorities. However, it appears that when the political unrest is nearer to home (well, right inside the house, as it were) then US authorities are less accommodating of the democracy afforded by such real-time micro-blogging.
During the G20 summit the police were seen to be openly monitoring …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Don't forget netbooks, increasingly popular with the tech savvy user :)
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Using newly registered domains with a very short lifespan to host malware websites is so last year. It would appear that these days such things are far more likely to be hosted on much older compromised web sites instead. Could this be down to a decline in domain tasting?
The latest MessageLabs Intelligence report appears to think so, suggesting that the previously widespread practise of cancelling a new domain registration within a few days 'cooling off' period has been in decline recently. Indeed, the Internet Corporation for Assigned Names and Numbers stated as much in June. The MessageLabs analysis of those websites which had been established purely to deliver malware showed that those domains classified as young, registered within three months of being blocked for hosting malicious content, are now relatively small in number. Mainly because they are discovered and taken down within the first 38 days of registration in 90% of cases. When it came to older domains that had been registered for more than three months and then compromised for malware service, MessageLabs discovered that they have a much longer shelf life: 90% are taken down after 138 days. Overall, 80% of sites blocked for serving up malware are established legitimate sites which have been compromised.
"It is not surprising that with a small window of opportunity for younger domains, the attackers register domains much faster" Paul Wood, MessageLabs Intelligence Senior Analyst, Symantec says "suggesting that attackers are working very hard to set up …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Bletchley Park, the top secret code breaking hub that played a pivotal role in the outcome of World War Two, has finally been awarded development funding of some £460,500 ($735,500) from the Heritage Lottery Fund.
The money will literally save the place the saved the lives of countless people by shortening World War two by at least two years. With the money, the Bletchley Park Trust will be able to start plans for transforming Bletchley Park itself into a world class heritage and educational centre. The Trust now has a further two years in which to finalise the plans before submitting them to the HLF in order to raise a further £4.1 million ($6.5 million) of the total £10 million ($15.9 million) needed for the project.
One very vocal supporter of Bletchley Park, the renowned actor, author and Twitterer Stephen Fry could hardly contain his joy: "the news that Bletchley Park has the initial support of the Heritage Lottery Fund is simply wonderful" Fry enthused, adding "and yet, what should the Heritage Lottery Fund do if not exactly this? As each year passes it is becoming clearer and clearer just how vital a role in winning the war Bletchley played".
It has been a good month for code breaker fans. Just a couple of weeks ago the British Prime Minister, Gordon Brown, apologised for the prosecution and persecution of Alan Turing which ended up killing the man who led the technological fight against …
majestic0110 commented: Interesting news! +5
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
When singer Lily Allen posted a passionate plea for people to stop illegally sharing music files, and started a dedicated blog where fellow pop stars could voice their concerns over the 'theft' of their work, you might have been forgiven for thinking it would just turn into the usual bunch of rich kids moaning about how unfair it was that they couldn't buy a second Ferrari this year. However, it quickly got much more interesting than that, thanks to a large dose of double standards on the part of Allen herself.
The trouble with setting yourself up as some kind of industry spokesperson when the debate is as explosive as the music sharing one, and proffering support for a three strikes and you are out law, is that you have to be pretty damn sure of your position. While there is certainly a goodly amount of honesty, passion and common sense in what Allen says on the subject all of that pretty much disappeared up the wazoo, hidden by a smokescreen of her own making. Allen lit the match by seeming to forget that copyright and intellectual property rights apply outside of the glitzy music business. It would appear that the 'It’s Not Alright' blogger rather unfortunately posted a message to kick the whole debate off which, while explaining that copyright infringement is a bad thing, itself infringed the copyright of the person who had actually written most of it and the news site where the cut …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
The posts in question were deleted after being flagged as bad by other DaniWeb members. Upon investigation it turned out that not only did they have no bearing upon the thread/topic/forum in which they were posted but they also expressed a general hatred of Turkish people.
DaniWeb is a global community, where members of all races and nationalities are welcome. We do not tolerate postings which might cause offence to members based upon race, sex or religion.
Now I am sorry that some people seem to think that such postings are OK and should not be deleted, but our community would be a very unhappy place indeed if everyone was able to post messages of hatred and intolerance with impunity.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
There ain't no such thing as a free Windows 7 upgrade. At least that's what it is starting to look like for the majority of people, despite the 'free upgrade' vouchers that are being handed out with new computers as part of the Windows 7 Upgrade Option scheme. A scheme which has been introduced to stop the huge dip in PC sales during the period before a new Windows OS ends up being a standard feature that would otherwise occur.
According to research carried out by PC Pro magazine in the UK, PC manufacturers are charging their customers in order to redeem free upgrade vouchers.
Just how much they are charging customers for the privilege of a free upgrade varies from manufacturer to manufacturer, but the voucher processing fee can be as high as £27.90 ($45) in some cases. That's how much PC Pro revealed was being charged by Toshiba in order to send out the upgrade OS discs. Dell was keeping quiet and refused to say how much it was going to be charging for shipping and handling, however HP, Lenovo and Sony customers can all expect to have to find around £20 ($32.50) for the discs. Just to make matters worse, Microsoft recently announced it would make the full version of Windows 7 Professional available to students in the UK for just £30 ($40).
Of course, nobody is denying that there is a cost to providing Windows 7 upgrade OS discs. Media reproduction …
Phil Friel commented: Useful info, as always +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
According to a new report, published today by SANS, the overwhelming majority of all cyber-security risks can be laid at the door of just two areas: unpatched client-side software and vulnerable Internet facing web sites.
The report was compiled by Rohit Dhamankar, Mike Dausin, Marc Eisenbarth and James King of TippingPoint with assistance from Wolfgang Kandek of Qualys, Johannes Ullrich of the Internet Storm Center, and Ed Skoudis and Rob Lee of the SANS Institute faculty. But, to be fair, I'm not sure that attack data from systems protecting 6000 organisations and vulnerability data from 9,000,000 systems was really needed to arrive at its conclusion.
You only need to keep an eye on the news to realise that unpatched software is being targeted by the spear phishers and bad guys, with client-side vulnerabilities in the likes of Adobe software hitting the headlines this year and last.
The SANS 'Top Cyber Security Risks' report says that it represents "the primary initial infection vector used to compromise computers that have Internet access." What is interesting is the report finding that, on average, major organisations will take at least twice as long to patch these client-side software vulnerabilities as they do to patch operating system vulnerabilities. As SANS puts it "the highest priority risk is getting less attention than the lower priority risk."
And talking of priority risks, the number two according to the report would be vulnerable web sites. SANS …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
If it wasn't bad enough that someone is filing for a trademark to cover an adult-oriented games console called a SexBox, the world's largest adult entertainment company is seeking approval from Sony to turn its entertainment console into a PornStation 3.
Silican Xtal Corp, a San Jose based integrated circuit manufacturing company, has filed a trademark claim with the US Patent and Trademark Office for a SexBox. The filing refers to a "Video Gaming System Console comprised of computer hardware with unique user controls which plays interactive Adult Only rated video game software titles." I cannot imagine that the Microsoft lawyers will be taking this one laying down, considering how close to an Xbox a SexBox sounds. Indeed, the filing itself even talks about playing these adult content games through interactive adult communities and multiplayer online games. Considering that Microsoft does not allow such adults only content games, and we are not referring to 18 rated violent games but rather ones with a very explicit sexual content, you have to imagine it will fight this one all the way. If successful it could bring a whole new meaning to Red Rings of Death I guess.
Meanwhile, the largest adult entertainment (that's porn to you and me) company in the world, Vivid Entertainment, is apparently trying to convince Sony to allow porn content to be made available on the PS3. In an interview, Vivid boss Steve Hirsch argues that as long as "age …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Remember Conficker, the virulent worm which caused such havoc at the start of the year? No, well maybe news headlines such as 'Virus sinks Royal Navy fleet comms' and 'Windows worm infects millions' might help jog your memory. Well hold onto your hats people, Conficker is back. And this time it comes with a new twist.
According to security specialists BitDefender the worm has not turned, but returned. Looking at the e-threat statistical report the company produces, I could hardly believe my eyes: sitting ugly on top of the most infected by charts was Conficker. In fact, of all the infected machines that BitDefender looked into during the month of August, Conficker (a.k.a Win32.Worm.Downadup) was sitting there staring back at them on a really quite staggering 43% of them. That puts it way out in front of other malware threats, with the second most prevalent infection (an Embarcadero Delphi built code injector called Win32.Induc.A) mustering a relatively meagre 15% share.
The latest Conficker variant has some new tricks up its virtual sleeve, such as not only being able to prevent access to IT security vendor websites as it always has but adding the installation of rogue security software onto the compromised machine. Highly profitable scareware scams have hit the headlines here at DaniWeb before, and Microsoft has had some success in hunting down the offenders. But the fact that Conficker is blocking access to legit software sites and leaving the …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
I drive hundreds of miles every week, I write about technology for a living, I've been a TomTom user for years and I own an iPhone. It had to be done, I just had to review the TomTom satnav app for the iPhone.
Being both an iPhone 3GS owner and a happy TomTom satnav in-car user, like many people I had been waiting for the iPhone TomTom application to arrive. The delays seemed to go on forever, and in the meantime other players had entered the market: both Navigon MobileNavigator and ALK CoPilot Live launched before TomTom got into the App Store. But first is not always best, and as TomTom is pretty much the undisputed market leader I decided to hold out and wait for it to finally arrive. Not that it has finally arrived as I was hoping, by which I mean that the software application itself is now in the iPhone App Store for download but the hardware side of the product has yet to be released to retailers. I asked TomTom about this lack of the car kit at the moment, and a spokesperson told me it is "in the process of fine-tuning it so it lives up to the standards and quality we set for our products, and plan to announce the availability and pricing later this summer." Apparently a commercial decision was taken to make the software available despite the car kit not being ready just yet. "Although using the two together will …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
What do you wake up to? An old-fashioned alarm clock with small hammer and large bells atop a round clockface? Maybe a clock-radio or perhaps a straightforward digital alarm with a loud beep-beep-beep to get you moving of a morning? If you do, then you are in the minority as more and more of us apparently wake up to our mobile phones.
According to one new survey which questioned 1500 people regarding their morning bedroom routine, more than half used their mobile phones as alarm clocks.
One leading horologist and fellow of the British Horological Institute told the Daily Mail newspaper that the trend has already been seen with people using mobiles instead of wristwatches, and how it signals modern technology replacing mechanical things.
So what else is the mobile phone replacing? Well the same survey, unsurprisingly conducted for a mobile phone retailer, suggests that 20% of us use them to access the Internet, take photos, organise business schedules and keep on top of social networking.
I have to admit that it never actually occurred to me that I had replaced my alarm clock with an iPhone, but I have. In fact I have not used a 'proper' alarm clock since I first took delivery of the iPhone, it sits on my bedside cabinet acting as a handy one-tap illuminated clock for those middle of the night stumbles to the loo, and as a very effective alarm clock in the morning. I …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Just how much of a geek are you? Do you know who Sergey Brin is? Can you solve a Rubik's Cube, in under five minutes? Do you know the value of Pi beyond 3.14? Would you spend a small fortune to get satnav on your mobile? Or maybe strap a large sucker to your thigh to hold your iPhone in place when sitting down in public?
I did not make that last one up, honest. There really is a company which is marketing an iPhone accessory which is, essentially, just a large sucker cup attached to some velcro which straps around your thigh that you whack your iPhone on to keep it nice and stable when you want to use it sitting down away from a desk or table top.
The Thiphone (yes, that is what it is called) is described as being the 'universal thigh mount' for your iPhone which allows you to write an email and drink a frappuccino at the same time. No, seriously, this is such a geek magnet of an idea that it is exactly the kind of advertising which might just work. The manufacturers even reckon it makes driving safer as you can have your iPhone, controlling your in-car music, out of your hands and on your leg while motoring.
At a cost of $29.95 (£18) there is one thing that the advertising does not mention - you are pretty much guaranteed to look like, well, a …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
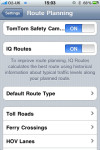
How much for an iPhone-powered TomTom satnav? That's the question that has been on the lips of many an iPhone user ever since TomTom announced it was developing a version of the market leading turn-by-turn satellite navigation system especially for the iPhone. Now, it seems, we are a little closer to knowing the answer. I just hope you are sitting down before I reveal it.
According to one online retailer which has broken ranks and gone public with pre-order pricing, if you want an iPhone-powered TomTom satnav in your car it will cost you a cool £113.85 ($193.75) which works out to £99 ($168.50) plus tax. Which is not, by a long shot, the most expensive iPhone app.
Now before you reel too far back in absolute horror, that isn't the cost of the maps and satnav software alone. In fact it's the price for an in-car kit which includes the software (with the latest Tele Atlas mapping and the TomTom IQ Routes feature) plus a specially designed, and I have to admit rather sexy looking, cradle which provides secure docking, enhanced GPS performance, voice instruction sound boost, hands-free telephone calling and in-situ charging of your iPhone.
In fact, a quick scout around the same site that has published that pre-ordering price is selling the cheapest standalone TomTom in-car unit for £118 ($200) which means that the iPhone version is actually cheaper, assuming you already own an iPhone 3GS that is.
Currently …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Now if you had invested in an Apple iPod Touch and it, well, exploded after you dropped it you probably would not be too happy about. You probably would contact Apple and explain what had happened, and you might be happy to accept a refund. But what if that refund came tied to a signed settlement agreement which legally bound you not to mention what had happened to anyone?
That's what one unhappy chap is claiming happened after the iTouch he bought for his 11 year old daughter went up in flames. Apparently he dropped it, it then started hissing and then he saw what he describes as 'vapour' coming from the device so he chucking it on the floor. 30 seconds later it went up with a bang, and ended being thrown some 10 feet into the air according to reports. This is not thew first time an Apple mobile device has become hot stuff of course.
It would appear that after talking to Apple on the telephone, the man was sent a standard 'deny liability but have your money back anyway' letter which he refused to sign as it also required him and his daughter not to talk about the exploding iTouch to anyone or Apple would seek damages through the courts.
Charming, I am sure.
Apple has declined to comment further on the story at this point in time. Mind you, it probably has other things on its mind …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
There are two things you can be sure of about the annual Las Vegas Black Hat security conference: nobody will use the free wifi as they are all too worried about being hacked, and someone will demonstrate an exploit that will scare the living bejesus out of you. The latter has just happened for iPhone users.
One well known discoverer of such things, Charlie Miller from Independent Security Evaluators, has revealed how a vulnerability can give savvy attackers the ability to gain complete control over your iPhone without any action on the part of the victim. Yep, this is the mother of all mobile remote hijack exploits by the look of it. Using nothing more complicated than a specially constructed text message, Miller says that malicious code can be executed in order to crash the device at the lesser evil end of the scale or take complete control for the more malicious attacker. It is even possible to use the attack to send text messages on to everyone in the victim's contacts list so spreading the hijack quickly to many more handsets.
Miller has been able to demonstrate the vulnerability courtesy of weaknesses in the iPhone CommCenter service that has responsibility for SMS and wireless functionality. Amazingly this runs as root but is not limited by any kind of application sandbox, so Miller realised it was ripe for use as a remote control hacking vector. All that is required is a slight …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
The bad guys of the IT business are always looking for the most effective ways to infect the innocent Internet user, and increasingly that means turning to commonly used web browser plug-ins such as Flash or PDF readers. A couple of years ago we were reporting critical vulnerabilities for all Adobe Flash platforms, and towards the end of last year there were reports of a critical vulnerability in Adobe Reader. Cue Jaws soundtrack: just when you thought it was safe to go back in the Adobe PDF water.
According to an official Adobe security warning "All currently supported shipping versions of Adobe Reader and Acrobat (Adobe Reader and Acrobat 9.1, 8.1.4, and 7.1.1 and earlier versions) are vulnerable" to another zero-day JavaScript vulnerability. That's all shipping versions on all platforms, including Mac and Unix users.
Adobe says that it "plans to provide updates for all affected versions for all platforms to resolve this issue" although it cannot currently say how long this will take other than to confirm it is "working on a development schedule for these updates and will post a timeline as soon as possible."
So what should you do in the meantime? Adobe recommends that in order to mitigate the issue, JavaScript should be immediately disabled in both Adobe Reader and Acrobat. Alternatively you could, of course, find another application for your Flash and PDF requirements which is less popular and not so attractive to the bad guys.
… happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Sexting is one of those words you might not have heard of if you are over a certain age. That age being 18 I would imagine. Sexting can best be defined as sending naked photos of yourself using your mobile phone to another phone or a social networking site.
As I have reported before, the plain fact of the matter is that teens just love posting naked pictures of themselves online. Indeed, surveys suggest that 36 percent of teen girls have posted online, or electronically sent, nude or semi-nude images of themselves as have 31 percent of teenage boys.
The reasons are quite clear, with 38 percent of teens thinking it makes dating more likely, and 52 percent of teenage girls saying it makes a sexy present for a boyfriend.
Now, according to reports, it seems that those youngsters involved in sexting would be getting more than they bargained for. Forget the danger of the images getting posted around the Internet, swapped between other kids and so on, how about getting a criminal record? Yep, high school kids in a dozen US States have already been charged with possession of child porn and disseminating child porn as a result of receiving and sending naked images this way. If they were to be convicted of the charges, which I suspect is unlikely, they could be placed on the sex offender register as a direct result.
I'm not sure that charging these teens on …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Dell is taking the netbook market by the horns, it would seem. First it refuses to accept that the Psion netbook trademark is a valid one, and now it bucks the market trend for not being able to sell Linux powered netbooks.
While the netbook market seems to be moving away from Linux and selling more Windows XP powered machines than anything else, dell is happy to be bucking the trend. Well kind of. Two thirds of the Mini 9 netbooks it has sold have shipped with Windows XP Home, but that has not stopped Dell from shouting from the rooftops that 33 percent of them have shipped with Ubuntu.
Perhaps more interestingly are the return rates that I have been reading about. While the company that makes the 'Wind' netbook, Microstar, reckons that four times as many Linux powered machines come back as returns than Windows XP ones, Dell has a different tale to tell claiming the return rate is much less. In fact it reckons it is the same as for the Windows XP machines, and that is very low.
"We have done a very good job explaining to folks what Linux is" a Dell spokesperson told Laptop Magazine. Which makes a change from 18 months back when we were reporting that Dell staff didn't seem to know that Ubuntu was even an option.
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Plenty of people have done it, gone online pretending to be something they are not. Indeed, plenty of men have gone online into chat rooms, forums, virtual worlds and social networking sites pretending to be women. Usually it is for the attention, sometimes it is for the sexual kicks of a gay guy getting chatted up (or even engaging in cyber-sex with) an unsuspecting straight man. Most people do not enter into this game of false identity with blackmail and sexual assault in mind though.
Yet that is precisely what an 18 year old teenager from Wisconsin is charged with doing. He is alleged to have used Facebook as the launchpad for a bizarre blackmail plot which culminated in the real world sexual assault of other teen boys.
Anthony Stancl, so Waukesha County prosecutors claim, is said to have not only posed as a number of females using Facebook but managed by so doing to entice teenage boys into sending naked photographs and videos of themselves to him. Hell, we all know how much teens just love posting naked photos of themselves online. Once they had done that, it is alleged, he then used the photos and videos as leverage in order to extort sexual favours even though he was aware that no less than six of them were under the age of sexual consent.
Of course, it is not illegal to pose as a woman, or indeed a man, on Facebook or …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Multiple arbitrary code execution vulnerabilities in Ruby have been revealed by the Apple Product Security team which could lead to Denial of Service attacks. A total of five vulnerabilities have been reported, with versions impacted being:
1.8.4 and all prior versions
1.8.5-p230 and all prior versions
1.8.6-p229 and all prior versions
1.8.7-p21 and all prior versions
1.9.0-1 and all prior versions
Upgrading to either 1.8.5-p231, 1.8.6-p230, 1.8.7-p22 or 1.9.0-2 is recommended.
This is, of course, of particular interest to Apple as its Mac OS X Leopard comes complete with a Ruby on Rails web development framework.
For an in-depth examination of the vulnerabilities head over to security guru Eric Monti at the Matasano Chargen blog who has been dissecting the detail.
Monti says "These vulnerabilities are likely to crop up in just about any average ruby web application. And by “crop up” I mean “crop up exploitable from trivial user-specified parameters”. Unlike un-handled ruby exceptions getting raised, these bugs aren’t the fault of the programmer as much as the fault of the interpreter. Part of the unwritten “contract” with your interpreted language is that it will prevent you from letting ridiculous things happen by raising an exception."
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Back in May, I broke the story on DaniWeb in this very blog of how the online application facility for UK visas was not only insecure, but that it had potentially been so for years. The company concerned, VFS Global, which operated the visa online application form filing service on behalf of the UK government in India and other countries, had such Mickey Mouse security in place that anyone could easily get hold of the full application form information of anyone who had made such an application. That's anyone as is terrorist, identity thief, innocent applicant stumbling across the information or even an investigative journalist. The story quickly gathered momentum, and featured as the lead on Channel 4 News in the UK after I brought it to their attention and aided with the investigation.
Today, the UK Information Commissioner's Office (ICO) has found the Foreign and Commonwealth Office (FCO) in breach of the Data Protection Act following an investigation into that application facility security fiasco.
This follows on from an independent report, instigated by the UK Foreign Secretary at the time, and conducted by Linda Costelloe Baker in June which concluded that the VFS operated online application system should not be re-opened. Indeed, it has remained closed ever since I first brought the security problem to light back in May.
I alerted the ICO the very first day that the security breach became clear, following my own 'testing' of the database …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
There was a kind of cult of C-list celebrity surrounding Adam Lyons a few years back, but only amongst teenage boys who asked him for help with cheat codes on the UK Sky One TV video gamers show Gamezville. Back then he was known simply as the Games Guru, but since leaving the show he has been setting himself up as an expert player of a different kind. I was rather bemused to get a press release detailing how Adam had turned his attention from cracking the hardest games to finding the cheat codes for picking up women. Apparently, by suing simple systems and word games he has 'managed to break down his system into a simplified formula that is duplicable by all' and which is particularly of interest to video gamers.
According to Lyons guys that play videogames actually have a massive advantage when it comes to learning this stuff. Lyons says "gamers are predisposed to be good at observing patterns and breaking systems. We've been doing it against those end of level bosses for years. All I've done is shift the focus from the screen onto the girls." There's even a video of Adam on YouTube using his pick-up techniques in a video game shop, to prove just how easy it is.
OK, so what are the top five techniques that a video gamer should apply to picking up members of the opposite sex then?
- Open, Open, …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
IBM researchers have unveiled prototype 3D visualisation software that will enable doctors to interact with their medical data in pretty much the same way they interact with their patients. The technology, known as the Anatomic and Symbolic Mapper Engine (ASME), uses an avatar representation of the human body which the doctor can click on to trigger a medical records search relevant to that body part.
"It's like Google Earth for the body," said IBM Researcher Andre Elisseeff, who leads the healthcare projects at IBM's Zurich Research Lab. "In hopes of speeding the move toward electronic healthcare records, we've tried to make information easily accessible for healthcare providers by combining medical data with visual representation, making it as simple as possible to interact with data that can improve patient care."
If went to see my doctor today with a bad back, they would question me about any previous back problems I may have experienced, examine me both visually and physically, maybe run some tests. The doctor will also rifle through records to search for relevant information, some of it archived on computer some of it buried in the paper files. Even in the increasingly networked age we live in, the chances are that the doctor will not have immediate access to a full patient history however. Which means the patient will not have access to an immediate and 100 percent accurate diagnosis.
IBM argues that the ASME 3-D avatar changes that. By clicking on …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Internet security giant Symantec has just published the latest Internet Security Threat Report, based on an in-depth analysis of global Internet traffic and email during the last six months. Beyond all the usual who is hosting what and where, how much malware is contained in spam and which threats are continuing to cause problems data, there is one truly shocking statistic buried within the 134 page document: stolen information is dirt cheap on the black web economy.
The report suggests that cyber crime has become a professional, even a corporate, business. Organized crime units across the world are rolling out targeted, sophisticated and above all else hugely profitable online attacks. But they are also showing real business-savvy by creating the tools and the opportunity for wanabees to get involved who possess little in the way of criminal hacking, coding or scamming skill. They are establishing what can only be described as a criminal and fraudsters pyramid scheme.
If you want to enter the world of the cyber crime lord then you can start at the bottom by investing in an out-of-the-box toolkit, just $50 for a ready made phishing kit that is easy to install and professionally coded to enable the newbie to get out there and get defrauding the online public. These packages even come with built-in support for everything from fake website creation to email targeting. A Symantec investigation into the three most widely used phishing toolkits reveals that they alone were responsible for …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Simon Willcocks is a man on a mission, albeit an unusual one that no doubt many developers will recognise as being something of a geek driven dream. The mission in question to deliver native RISC OS desktop applications under Linux. This dream is fast becoming a reality, however, with the news that the RISC OS Look and Feel (ROLF) project is ready to produce a live bootable CD to demonstrate just what it is capable of. The ROLF live CD is said to include an iconbar, filer, terminal emulator, MP3 player, NetSurf, Inkscape and more.
The idea of being able to run native RISC OS apps alongside Linux ones, all the time retaining a familiar desktop environment, is certainly ambitious. If Willcocks can pull it off, the end result will be a Linux driven PC that can produce the RISC goods as well as being able to play DVDs, games and deliver the latest web technologies.
Using a custom written window manager, ROLF enables GTK+ applications to run on a RISC OS style desktop courtesy of an interface layer. Using the bundled library it is possible to develop native ROLF applications, although it should not be too difficult to port programs using OSLib in the enar future either the developer promises.
What is missing at the moment is the ability to allow native ARM-targeted RISC OS applications to run over the Brandy BASIC interpreter and QEMU on a standard Intel-powered Linux PC, although Willcocks says …
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Were you one of the many, and the chances are that being a reader of Inside Edge dumps you squarely into the informed geek category (and there really is no offense meant in that remark, says a fellow informed geek), who mourned the passing of promised core parts of Longhorn such as WinFS when Vista finally emerged?
If you shed a tear then, perhaps you might want to get the big box of tissues out again. This is not going to be a good news day for you.
It has come to my attention that attempts to revive a version of Vista, complete with WinFS, have been shot through the head by the Microsoft legal machine.
It should come as no real surprise that the Longhorn Reloaded project is officially dead. “To put the projects aims simply, we aim to finish off what Microsoft started before the operating system was canceled. It is a modification of Windows 6.0.4074, which was originally released during the 2004 Windows Hardware Engineers Conference” says the project blurb. It was doomed to failure from the get go.
Did anyone seriously think that Microsoft would allow an early Vista Beta to be promoted, distributed and lauded?
Of course not.
Doesn’t stop me from applauding the effort to take this build and build upon though, not least because it would have been nothing short of a miracle if the Longhorn Reloaded project could succeed given that it …