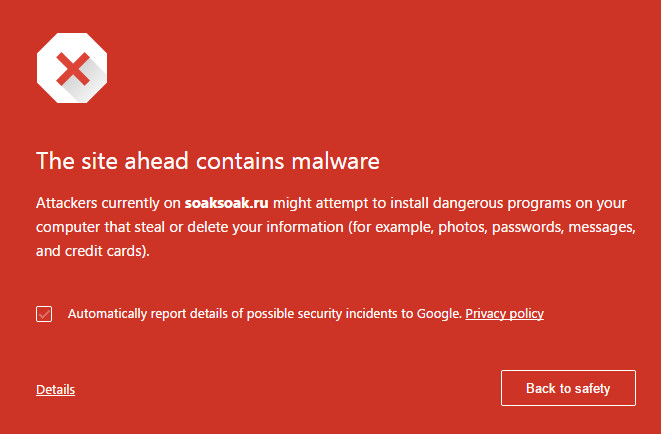
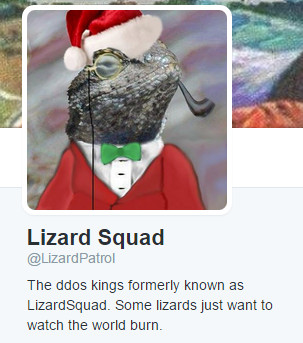
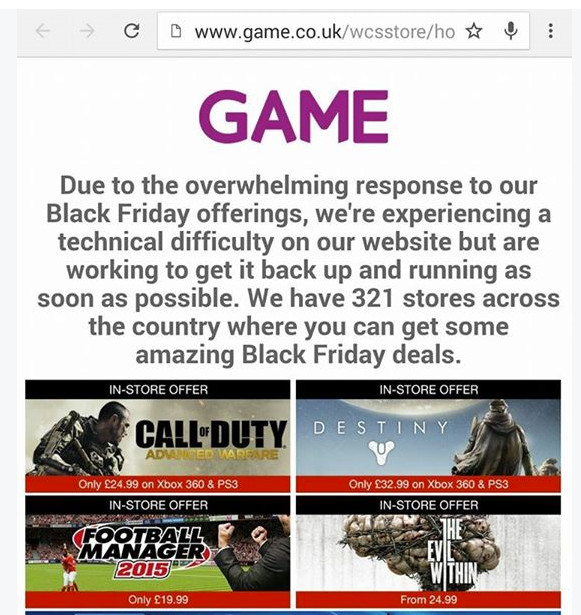
Welcome Scott. You'll be fed up of all my welcomes, what with PM and in forum now :)
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Stuugie commented: Interesting and thanks for sharing. +6
stultuske commented: yup :) +0
pritaeas commented: Congrats! +0
mike_2000_17 commented: Congrats +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
Reverend Jim commented: Hah! +0
Dani commented: I was one of the 10 who liked Me. +0
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster
mouaadable commented: damn so funny +1
happygeek 2,411 Most Valuable Poster Team Colleague Featured Poster