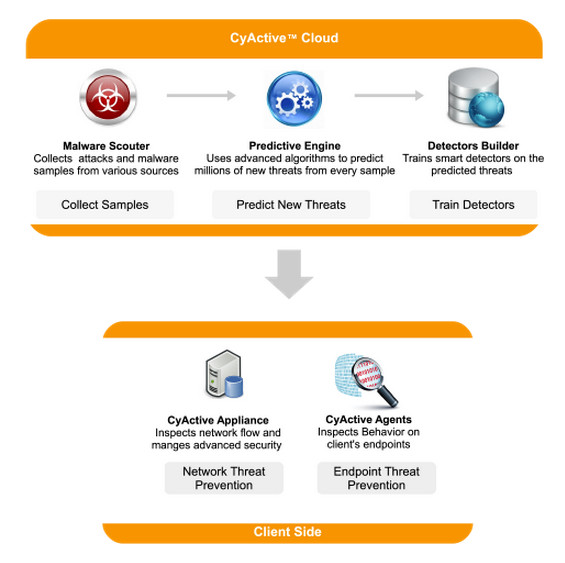
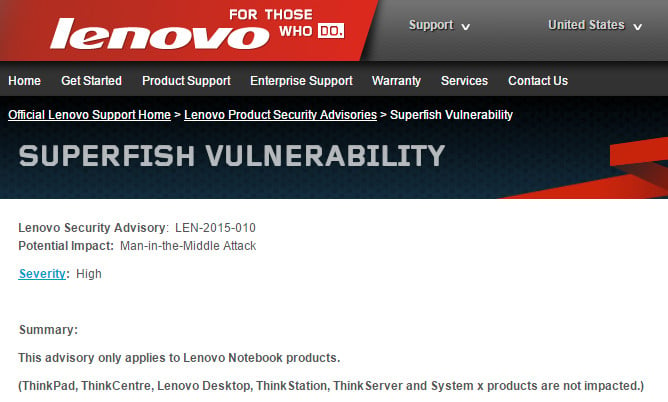
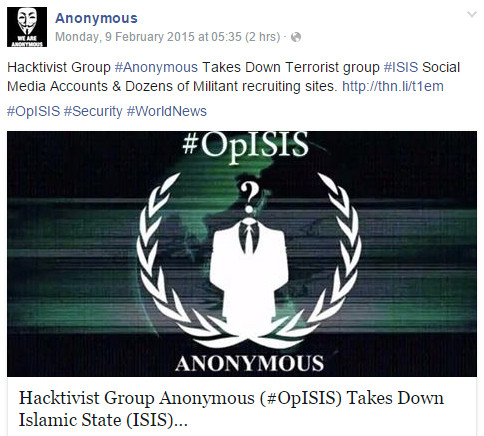
Which 12 year old operating system which is still running on 11 million servers is about to die? Yep, that's the one: Microsoft Windows Server 2003 reaches 'end of life' status on July 14th.
One of the longest running discussions on DaniWeb asks the question Why does Windows XP refuse to die? and I have my suspicions that we may be asking the same of Windows Server 2003 in the years to come. Which is fine as far as it goes, unfortunately that's not very far in terms of security as there will be no more security patches, updates or assisted technical support. One industry expert has described this as being the "biggest security threat of 2015" and published a white paper on the subject with the very apt title of 'Server 2003 is dead. What are you going to do?'
Ade Foxall, CEO of Camwood and co-author of the report, suggests that discussion of Server 2003 end of life has been woefully limited even within the IT professional community, certainly when compared to the kind of coverage that XP got when it was approaching the same terminal stop. In an analysis of more than 5000 IT publications, Foxall discovered that Server 2003 end of life only got 5% of the news coverage that the end of Windows XP stirred up. “After the recent migration away from Windows XP, IT departments should be more aware than ever of the dangers of using an out-of-date platform" Foxall …